OAuth with Verify Identity Access
IBM Verify Identity Access provides user-friendly access management and multifactor authentication to help organizations maintain security as they adopt new technologies. It can be used as an Identity Provider by the IBM Application Gateway (IAG) using OAuth Introspection (as depicted below).
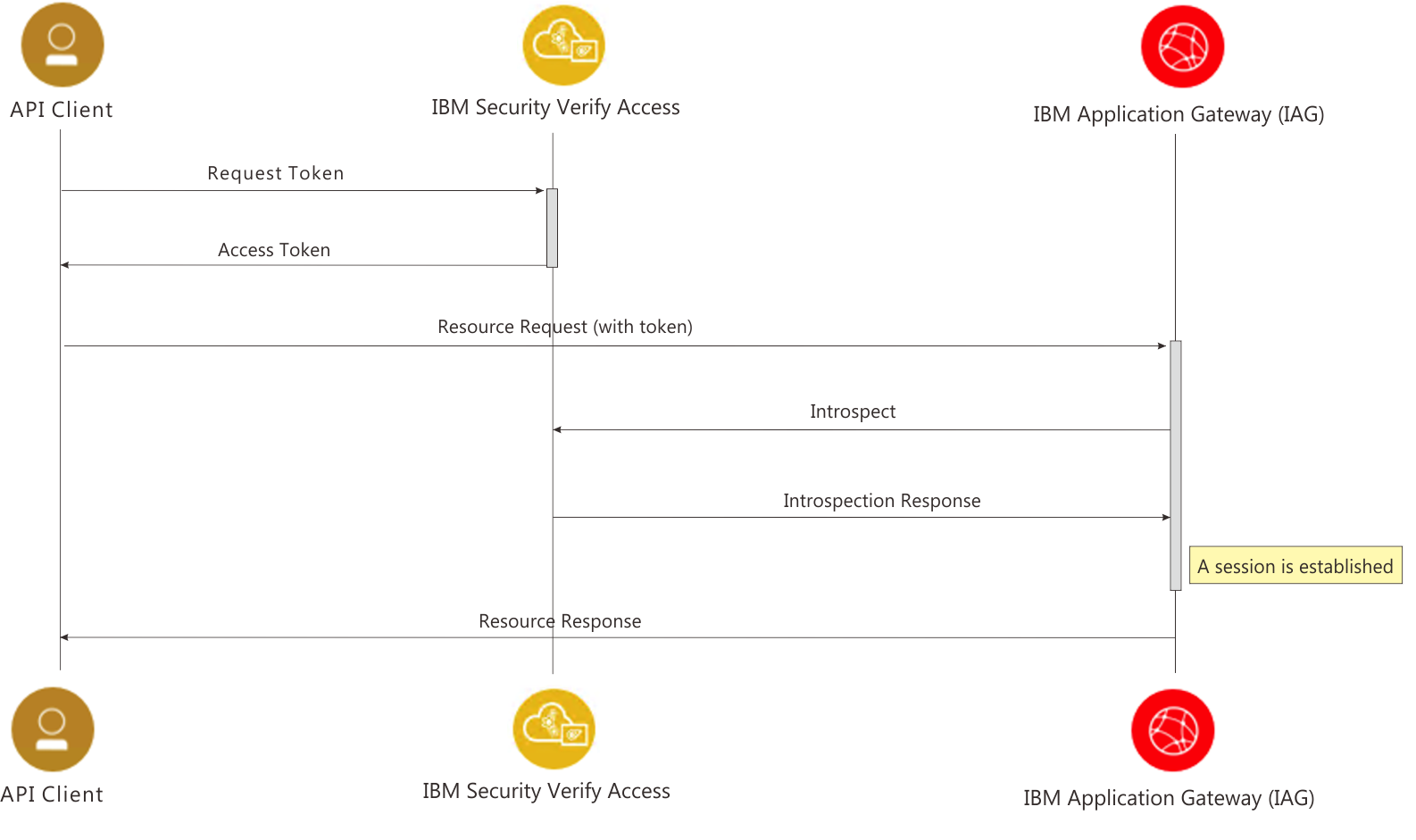
Prerequisites
Before attempting to configure Security Verify Identity Access as an identity provider for IAG:
- You need an IBM Verify Identity Access or IBM Security Access Manager 9.0.3.0+ appliance with the Advanced Access Control offering activated.
- You need to create an API Protection definition. More information on how to create an API Protection definition can be found in the IBM Verify Identity Access documentation: https://www.ibm.com/docs/en/sva/latest?topic=support-configuring-oauth-20-api-protection. When creating the Client for the API Protection definition you need to take special note of the created client ID and secret.
Configuration
The IBM Verify Identity Access configuration is contained within the identity/oauth node of the IAG configuration YAML:
- A description of the configuration options is available from the oauth page within the YAML reference. A minimal configuration requires the following configuration data:
- Name
- Introspection Endpoint
- Client Identity
- Client Secret
- Attributes
- IBM Verify Identity Access CA certificate
- An example configuration file is also available in the IBM Verify Identity Access: OAuth example page.
Updated 3 months ago
