Deployment Considerations
Deployment Considerations
When you deploy The IBM Verify Identity Access OIDC Provider, consider the following points.
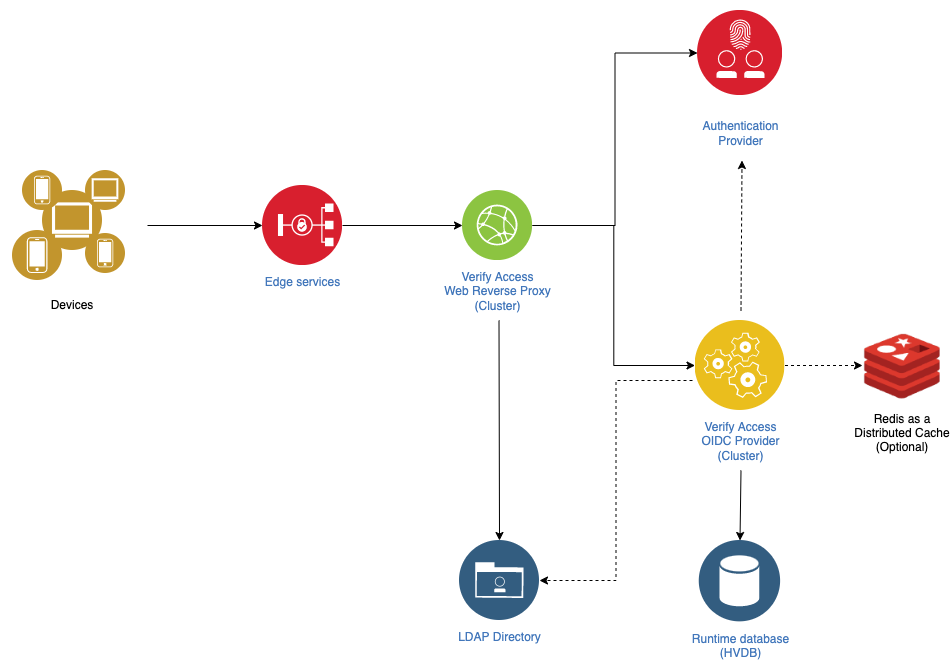
.
-
IBM Verify Identity Access OIDC Provider must be hosted in a secure network zone and not visible to the public zone. It is only routed through Verify Identity Access Web Reverse Proxy.
-
All non-TLS communication must be disabled. Enable TLS-only communication between IBM Verify Identity Access OIDC Provider and data layer components such as Verify Identity Access runtime database, LDAP and Redis.
-
Verify Identity Access runtime database must be hosted in a secure network zone and not be routable from the internet.
-
Use a highly available solution for the external Runtime Database. This service is critical to Verify Identity Access OIDC Provider operation.
-
If external session storage is used, in the form of the Runtime Database or Redis, it must be hosted in a secure network zone and not be accessible directly from the public zone.
-
Use an external logging server or service to store logs. IVIAOP streams logs into the container standard output (stdout).
-
Keep the host systems and Docker up to date.
-
Run the Verify Identity Access OIDC Provider as a non-root user.
High Availability Considerations
When you deploy The IBM Verify Identity Access OIDC Provider for high availability, consider the following points.
-
Use Redis or Runtime Database as session storage. Redis is preferred given it is highly performant and provides automated cleanup of expired data.
-
In-memory session storage is not recommended. If it is used, modify the IVIAOP junction to be Stateful. See https://www.ibm.com/docs/en/sva/10.0.5?topic=junctions-configuration-stateful.
Network Boundary Protection
-
For ingress controls, ensure that only required pods and services are exposed.
-
For egress controls, ensure that outbound accesses are given for required pods only and that ports, protocol, and destinations are limited whenever possible.
-
For Inter-pod controls, allow only flows between specific pods or groups of pods that are required to communicate as part of normal operations.
Updated 3 months ago
