Protecting IBM Verify Identity Access OIDC Provider runtime using Mutual TLS
Protecting IBM Verify Identity Access OIDC Provider runtime by using Mutual TLS
When the IBM Verify Identity Access OIDC Provider runtime is hosted on a cloud platform, it's important to put appropriate network security policies in place to protect the runtime container. Otherwise, it can lead to attacks by bad actors.
To improve the security posture of the runtime container, protect the runtime container by using Mutual TLS.
Configuring provider.yml
- Setting the server configuration
require_mtlsto true. - Configuring a client_auth_trust_store where all the trusted certificates are stored.
# Copyright contributors to the IBM Verify Identity Access OIDC Provider Resources project
version: 24.08
logging:
level: debug
definition:
id: 1
name: OIDC Definition
grant_types:
- authorization_code
- password
- client_credentials
- implicit
- refresh_token
- urn:ietf:params:oauth:grant-type:token-exchange
- urn:ietf:params:oauth:grant-type:jwt-bearer
- urn:ietf:params:oauth:grant-type:device_code
pre_mappingrule_id: isvaop_pretoken # Pre-Token mapping rule ID.
post_mappingrule_id: isvaop_posttoken
base_url: https://isvaop.ibm.com:445/isvaop
token_settings: # Token Settings
issuer: https://isvaop.ibm.com # OP's issuer URI.
signing_alg: PS256 # Signing algorithm for ID token generated.
signing_keystore: isvaop_signing # Signing keystore name.
signing_keylabel: jwtsigning # Signing key label.
device_flow_settings:
device_flow_polling_interval_seconds: 10
device_flow_codelifetime_seconds: 300
device_flow_usercode_length: 7
device_flow_usercode_charset: 'ABCD1234'
enforce_clientauth_device_authorize: true
attribute_map: # Attribute mapping to resolve claims. also refer to attributesources.yml
surname: surname
server:
ssl:
key: ks:rt_profile_keys/httpserverkey
certificate: ks:rt_profile_keys/httpservercert
client_auth_trust_store : ks:truststore
require_mtls : true
jwks:
signing_keystore: isvaop_signing
secrets:
obf_key: "ENC:iUt+3MzCntxSL2FPTUuJqER79UaiRSApMz3cbgJm4yzuiv6H7KN8ADsamX6+Qre1oTsATjnb1bJ0Lmi7WWfxWeGT477yqqvgVayFlCDIFzZeNkdINjASfTE3B+/3Sm9YjIYuWtZdySiXeydhJXSiOGU9osdA9g2BZXR4eMrXNutCuaSvFH6MY+TyOH5q15vy6vEWOebJQHrnug0A8rN6NF8G8XaxCe/+yqH57jJpdhm0N7iUydIYOBOQ1wDgCc8nRMWkQqlkcRhDZvLLAIlhoshYvo06ubyryt8/vv/0AvTLq9AIiQoL8CtYLr+SNZlzWe4CnHYZdO9S+AIrUOVORw=="
enc_key: "@keys/private.pem"
Configuring Web reverse proxy
- Web reverse proxy is used as the point of contact for the IVIAOP runtime.
- After require_mtls is set to true, the communication between the web reverse proxy and the IVIAOP runtime is also protected by using Mutual TLS.
- Hence, the Web reverse proxy junction configuration needs to be updated to send client certificate during the junction communication.
- On the IVIA local management interface, navigate to System->SSL Certificates-> pdsrv.
- Create a new Personal Certificate that will be used as client certificate for Mutual TLS, here is an
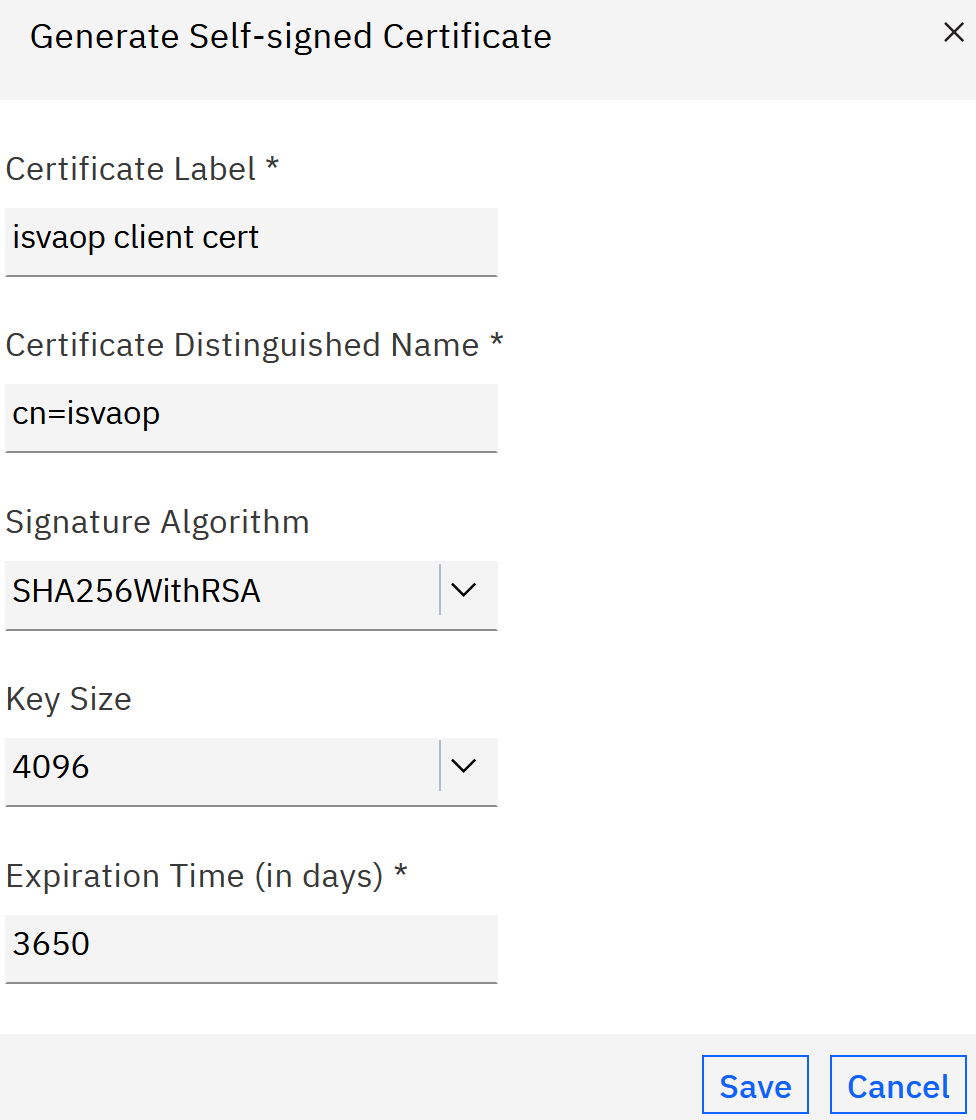
.
- Save, Deploy the pending change, and Restart the Web Reverse Proxy instance.
- Navigate to the reverse proxy instance, Manage ->
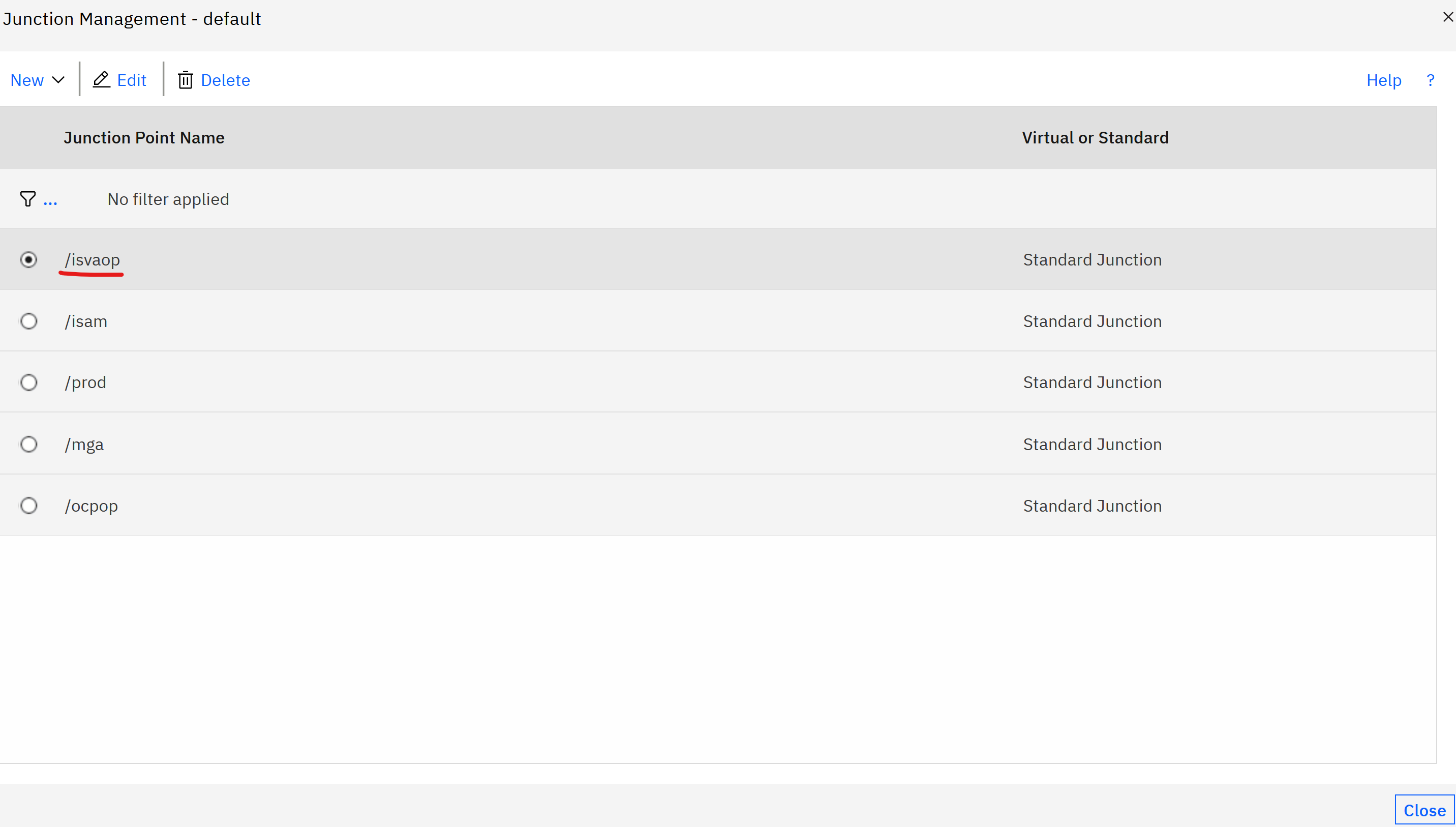
.
- Select the junction configured to IVIAOP runtime. Check Enable mutual authentication to junctioned WebSEAL servers in the Basic Authentication tab and select
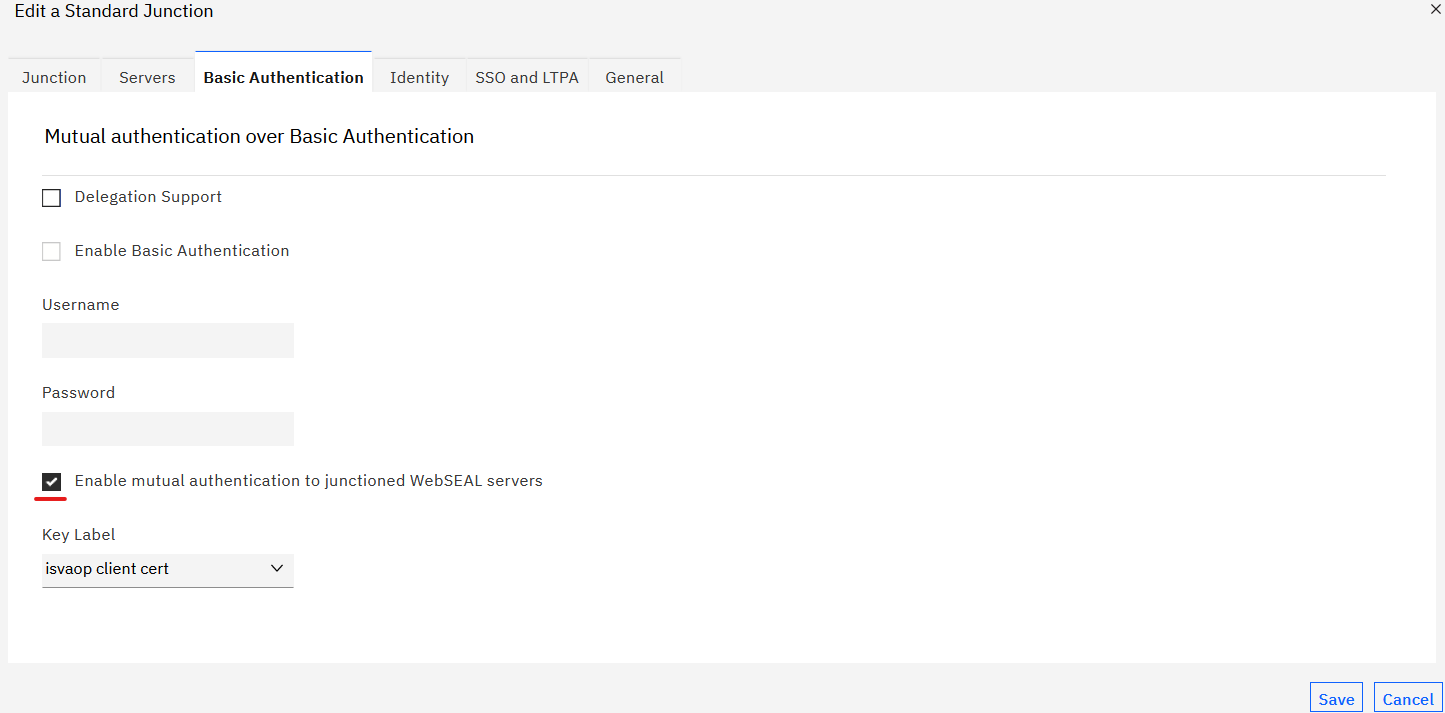
.
- Save the junction changes.
Adding the client certificate to the trust store
- As an example for SSL configuration, the client_auth_trust_store is configured to ks:truststore in the server configuration.
- The certificate that is used for Mutual TLS needs, must be added to the ks:truststore.
- Retrieve the certificate from the IVIA, pdsrv keystore and add it into ks:truststore.
- Example
keystore:
- name: truststore
type: pem
certificate:
- label: mtlsclientcert
content: |
-----BEGIN CERTIFICATE-----
MIIE5jCCAs6gAwIBAgIII7QhYxUdmcswDQYJKoZIhvcNAQELBQAwETEPMA0GA1UE
AxMGaXN2YW9wMB4XDTI0MDQwNzA0MTMwNFoXDTM0MDQwNjA0MTMwNFowETEPMA0G
A1UEAxMGaXN2YW9wMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAmukm
abTj0CHVrG/nTDAMm+jEQ7YJURg/XfQpIlrELLMEubXHDzn3Rk4jYkwaJHnKd2Jz
nWVluSyngF/TgWqhRALdKn4zel1djia8pB6fkoOkjHqlNlX86O7PDvgVko2HBXBL
2CJsOa787pw8kl4Odw9W6WeRmHz6VybTw91z0xfjfk3MCgCKUXg61RFlYtOIHU8B
jeUxitwWBcF93Qa/AB7MXINKHSmxfqNqfMJMH26Dfu6N0DWQEttEmUphNo1NJynC
ofZUUImGJcDKmr8m8JeSwLBXha0dvOmNnFVQ4GkUwsOk3zjP21JwB6Gy4TqvcYSU
tt7jrJSqTeJFKIH2FMHbegpxwCDVlVz3cmilsIv1n9I4glkZCNLn2xNnYGyMW+tH
/K628zKeB1KfZIcubgp1iMzmMhcSkiQ3Fpg7gSNRSDSMp8qPbK4b1qEqTux5KO5d
HHUy3+MJHZX/0S7EYMmSbMC9sdFs75i3/eHEWtkcX8X2pS0CS+JzVG/Of3Ua1wwg
qx8HxOMEDkxqzwQGA4/pzHh8CwXZ4bPKEIhMGW9z0Q2FE2LNeAu7t5ZurDecgkOP
4nelnABqMTfdJQ38+0H5BkUEXdLxXzFQpKpFsZQpOfw9mu6JCgbElfbmltPDhGEw
0+WqjaPLg+dxXjPAPVQn55fnd7W1CpCxy66xnvMCAwEAAaNCMEAwHQYDVR0OBBYE
FA13+nOk4op66sDx6loy2OoTaHJFMB8GA1UdIwQYMBaAFA13+nOk4op66sDx6loy
2OoTaHJFMA0GCSqGSIb3DQEBCwUAA4ICAQBwM7lTvU7ChadVtKfdMceQleVWDcJu
5hBKhwGfk+2udW4naJrKWfCO88zsm1D62b+bYb4myAJiUxxqA2pIioI9Veaor/U8
iQXZXC9NxA8gmyFr2KO47siIbbIK2QNeAePMh7FVOkzRq21FWgIJI+D7QXiMy3YZ
PORq2qZJfyLmKoMEfnH4sdTu61BRzKuiL6crThTuB4agXAv1YeevKr2DX3tQ9etW
WUQFF9ZiGWazUY6OoHyWxlQX5edShZbmwAJ/6A+DZ1Tywh5j4xVOWZzqDoAIqiIW
xytHUnVwthGYNQV6q52E39xGHVn5pu0Co/3cmvnguc9IRbLcmBakM7llC07YWvWV
2UGLqggRMR1B11FJZ5lubOL2hyqswGTz7AP4vrS/VLVmO7pcIZoz4pLMH6FBC+6/
sI8c59jmFNmY4Ue0peLfnx+bWI9pEebh56hSTeNCvWdiJgRcE4Avf9iIG0q75nJ1
n5+hGN9kBmT68uumA2waCkNtOX+75GD/m45d7slH3IHTg7YhtwnuepZe0cL/7Ksf
CuIhUVZK9BYqKKE2CsaTGM7XquFg1jjPHBCQ3zCMHd+JlKzpGKay3Jm9gi2lMZeF
wx7TNlZtKhNpxV0bO3x5aF+fjEWTBuqXooMAfNai7iANaNlLbWgvtbSo0xRFrI2j
TV+GFMVLwuHGPg==
-----END CERTIFICATE-----
Updated 2 months ago
