Using pre-authenticaiton access policy to determine first factor authentication
Using pre-authenticaiton access policy to determine first factor authentication
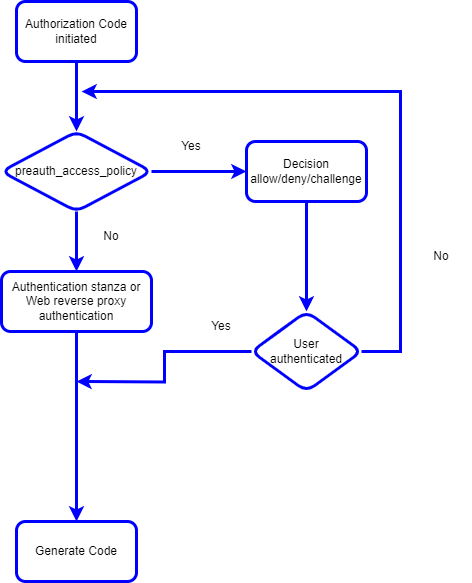
Scenarios exist where incoming OAuth/OIDC runtime parameters are used to determine the authentication method for a user, a pre-authentication access policy can now be configured when user authentication needs to be determined by an incoming Authentication Class Reference (ACR) value, scope or any protocol specific runtime parameter.
Configuration
- A new definition level configuration parameter preauth_access_policy_id.
definition:
id: 1
name: OIDC Definition
...
preauth_access_policy_id: test_policy
...
rules:
access_policy:
- name: test_policy
content: '@rules/preauthpolicy.js'
- The Web reverse proxy needs to be updated to attach an unauth ACL to the auth endpoint.
Pre-authentication policy snippet
importClass(Packages.com.tivoli.am.fim.trustserver.sts.utilities.IDMappingExtUtils);
importClass(Packages.com.tivoli.am.fim.trustserver.sts.utilities.IDMappingExtCache);
importClass(Packages.com.tivoli.am.fim.trustserver.sts.utilities.OAuthMappingExtUtils);
var protocolContext = context.getProtocolContext();
var reqScope = protocolContext.getAuthenticationRequest().getAuthenticationContext().getScope();
var acr = protocolContext.getAuthenticationRequest().getAuthenticationContext().getAuthenticationClassReference();
IDMappingExtUtils.traceString("reqScope: " + reqScope);
IDMappingExtUtils.traceString("acr: " + acr);
if(acr == "silver"){
var handler = new RedirectChallengeDecisionHandler();
let url = "https://www.acme.ibm.com/mga/sps/authsvc/policy/username_totp";
handler.setRedirectUri(url);
context.setDecision(Decision.challenge(handler));
}
else if(acr == "platinum"){
var handler = new RedirectDenyDecisionHandler();
handler.setRedirectUri("https://www.ibm.com");
context.setDecision(Decision.deny(handler));
}
else if(acr == "gold"){
var handler = new HtmlPageDenyDecisionHandler();
handler.setMacro("@MESSAGE@", "Incorrect acr_values requested");
handler.setPageId("error.json");
context.setDecision(Decision.deny(handler));
}
else{
IDMappingExtUtils.traceString("Allow");
context.setDecision(Decision.allow());
}
- Details about the available context and Decisions are available in the access_policy topic.
- User context is not available in pre-authenticaiton access policy, since a user session is not established.
Note
If the redirect challenge decision does not come back with a valid user session, the access policy will be executed with no prior context.
Updated 2 months ago
