Apply policies for UI access
Introduction
Usually access policies are associated with specific applications but you may also want to specify an access policy which is evaluated as soon as a user attempts to access the platform. This could be an end user accessing the launchpad or an administrator accessing the tenant admin console.
In this guide you will learn how to apply access policies to the end user launchpad and the admin console.
Pre-requisites
The steps in this guide will use a built-in access policy to require 2FA for all users. If you want to use a custom policy then you will need to create it before continuing with this guide.
Be careful not to lock yourself out of the administration console
Before you apply a policy to the administration console, make sure you can meet that policy or you will lock yourself out. For example, if your policy requires 2nd factor authentication, make sure you have access to an allowed and enabled 2nd factor.
The built-in 2FA policy used in this guide allows any 2FA factor to be used. This includes a one-time password to the e-mail address associated with your account.
Navigate to portal access configuration
In your tenant admin UI, navigate to the Security page. The Portal access tab is shown when this page opens.
Navigate to access policies configuration
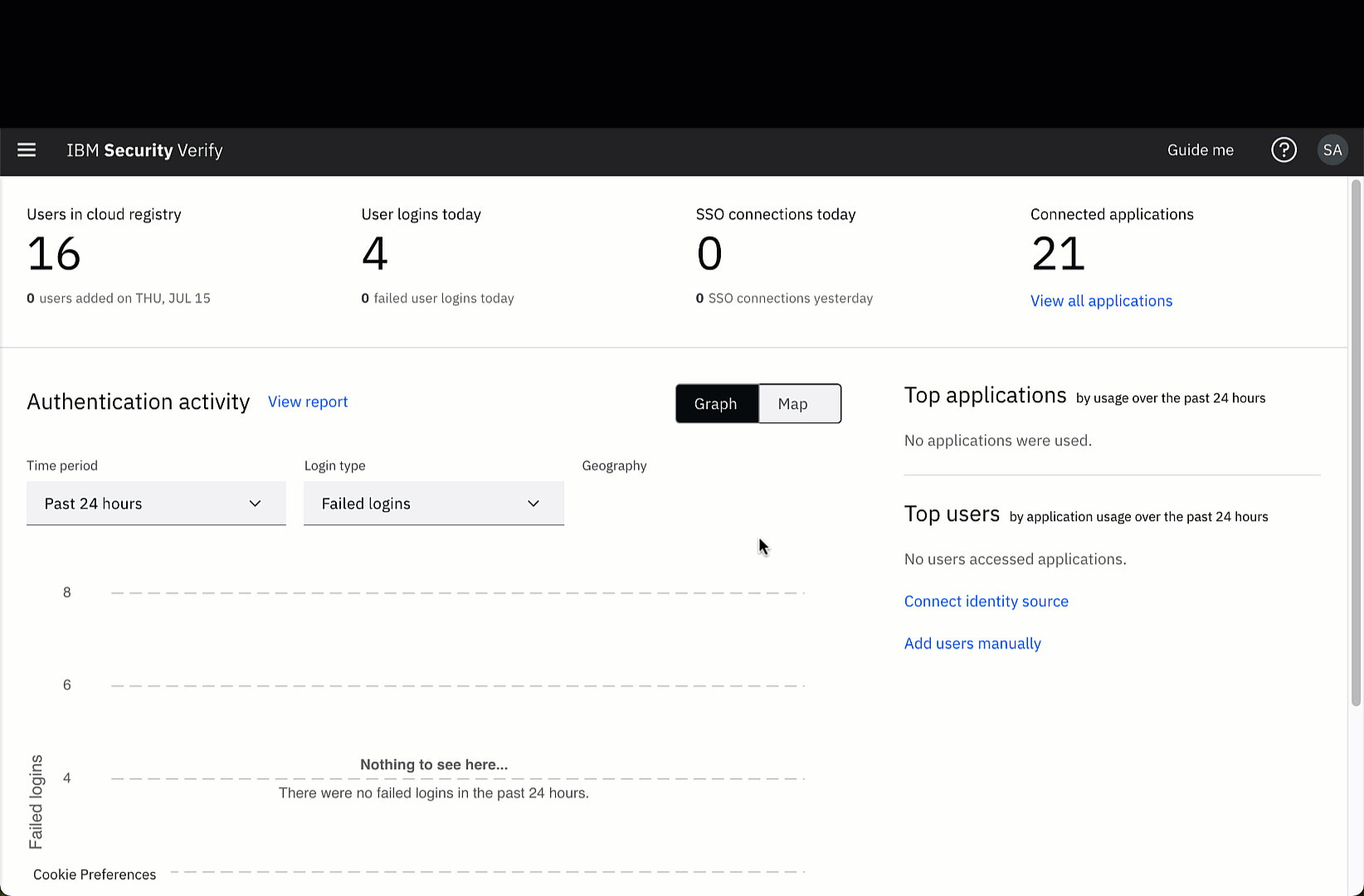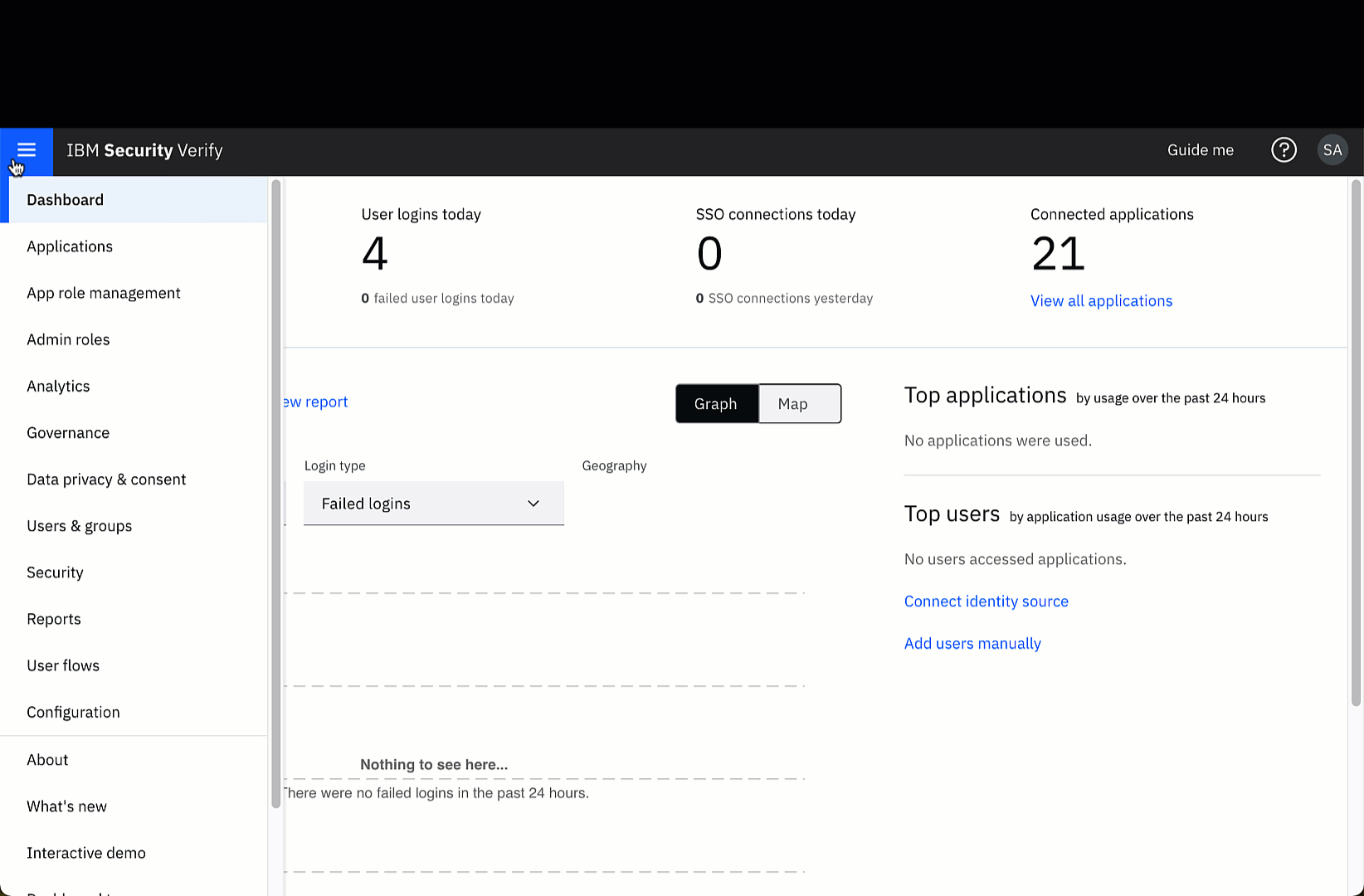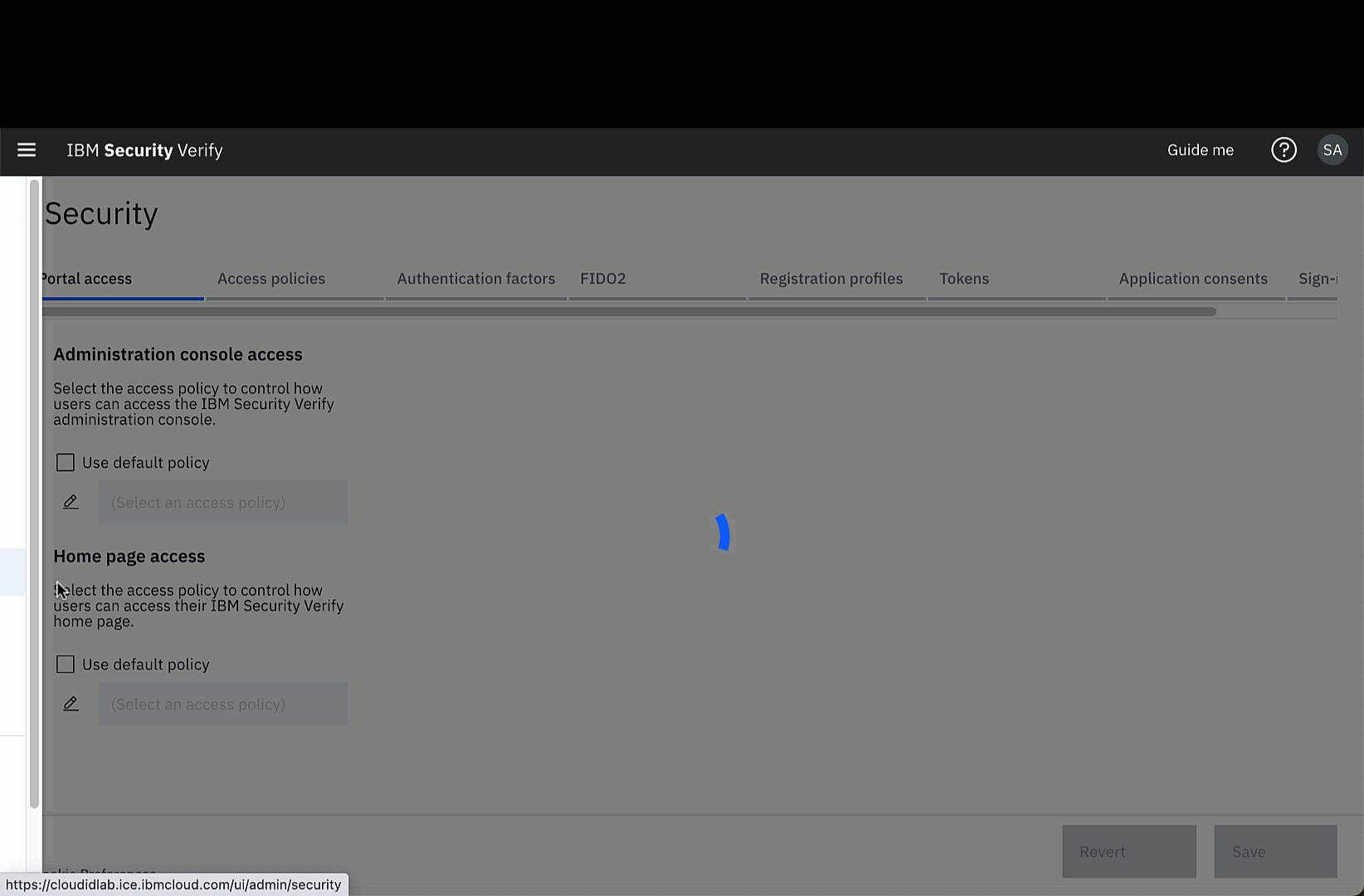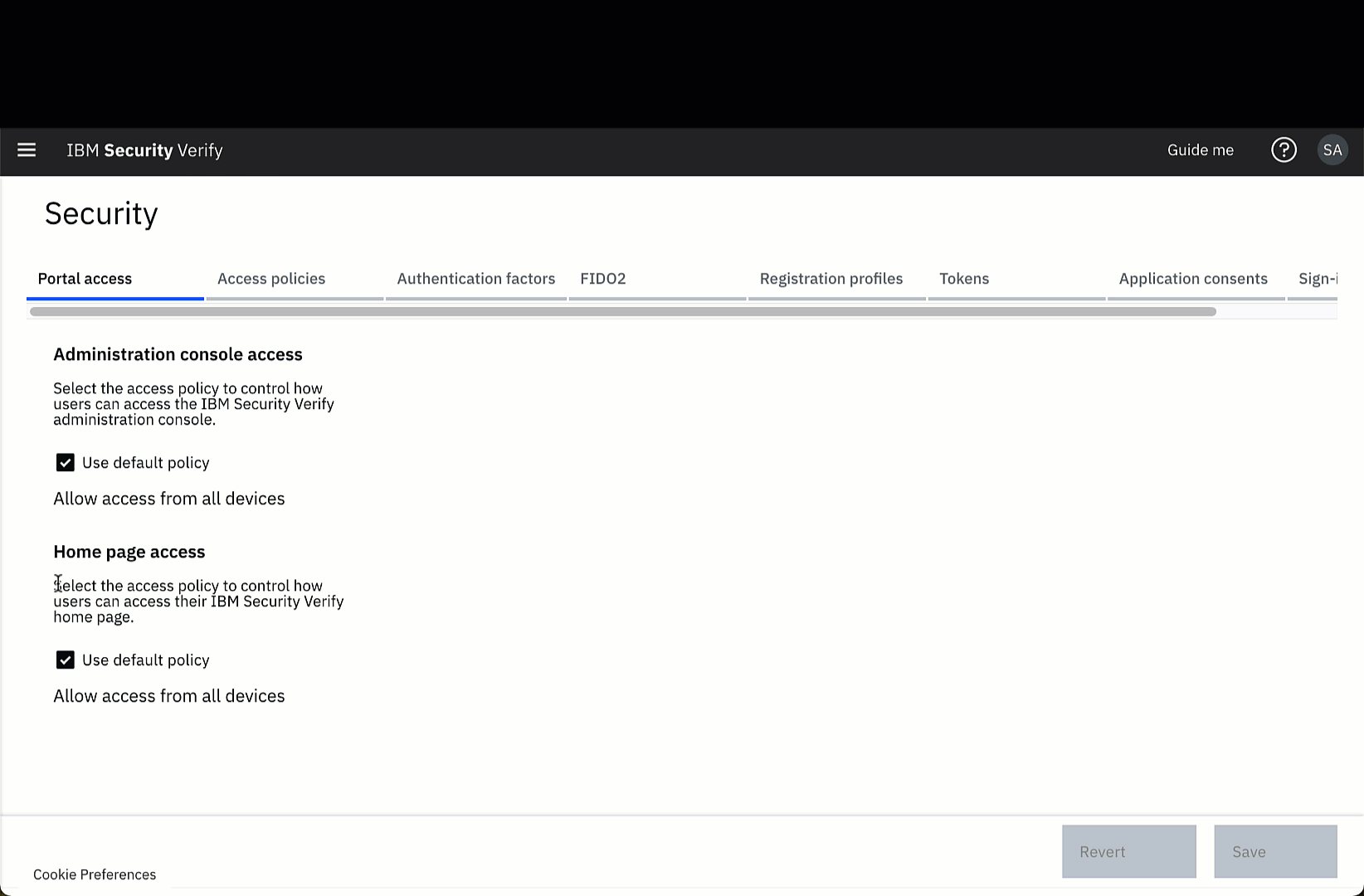
On this page you can see that the system is using the default policy for both administration console access and homepage access. You can see that the default policy is Allow access from all devices. This is a permissive policy which always allows access with no second factor authentication.
Select policy for administration console access
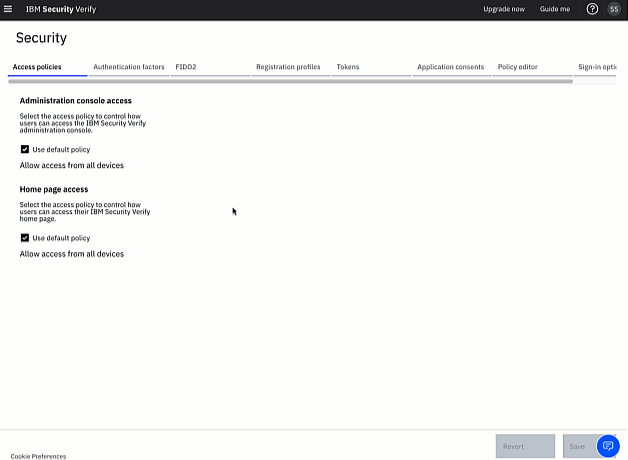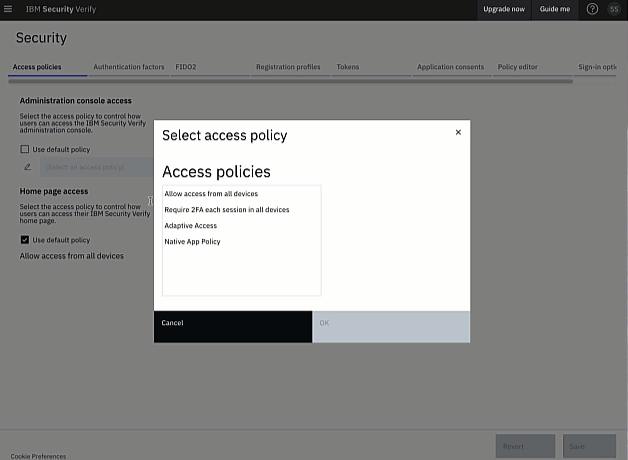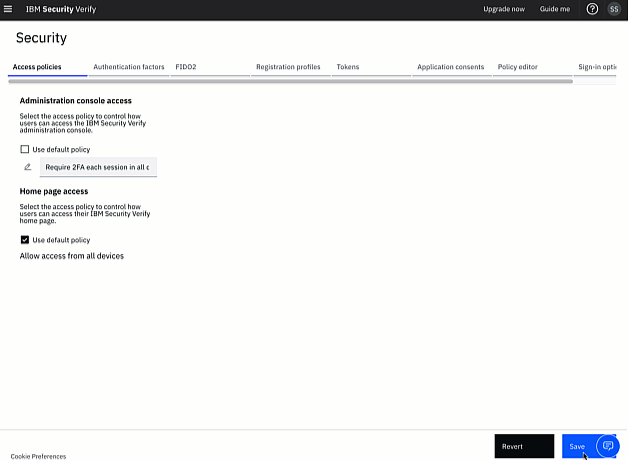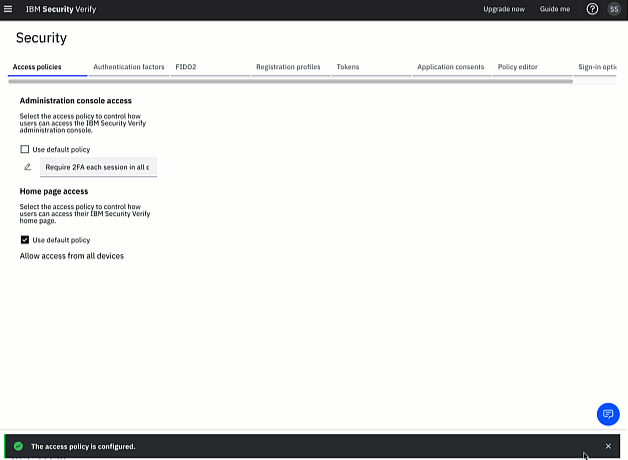
To set a non-default access policy for administration console access, clear the Use default policy checkbox and then click the edit icon which appears. A list of available access policies is shown.
Select the built-in Require 2FA each session in all devices policy. A description of the policy is shown.
Click OK to accept the policy. The policy is now displayed in the Administrative console access section of the configuration screen.
Click Save to save the updated configuration.
Test
With the updated policy in place, users accessing the IBM Verify administration console will now have to complete 2nd Factor Authentication before being granted access.
Safety first
It's a good idea to leave your current administration console session open while you test the new policy in a different browser (or an incognito or private window). That way, if there's an issue, you can disable the policy using this existing session.
In a different browser, navigate to the administration console of your Verify tenant. The login page is displayed.
Authenticate as you usually do.
When this first factor authentication is complete, the new access policy is invoked and you should be prompted for 2nd Factor Authentication. If you have multiple factors registered you will see a selection page. If you only have one factor registered, you will see a challenge using that factor.

Complete 2FA authentication. You can now access the Administration console.
If you are unable to complete 2FA for any reason, re-check the Use default policy checkbox using the browser session that is still logged in. Click Save to save the configuration.
Updated 6 months ago
