First access to trial instance
Introduction
In the trial of IBM Verify, the world is your oyster. We've enabled all use cases by default so you can try everything that Verify has to offer at your own pace. That can seem overwhelming at times, so this guide will walk you through the typical milestones that we would expect to get you going. It is our goal that by the time the trial period ends, you will have accomplished all the milestones that give you the most value of Verify.
"Guide me" for quick help
Within the admin console, you can always monitor your progress and get quick help such as in-app guides to walk you through scenarios that interest you. This guide me button is located at the top right of the trial. View various onboarding tasks or "show me how" guides for step by step tutorials.
Getting started milestones
Add your first application
First and foremost, adding an application gives you the ability to test almost every aspect of Verify. Once you have added an application, you can play around with various use cases such as:
- Entitlement management (such as request access workflows)
- Access policies and multi-factor authentication
- Attribute mapping and functions (more advanced)
- Access certification campaigns
Adding an application opens the doors for a wide variety of other scenarios which is why it's considered the number one thing to complete during your trial.
Search the catalog
Within Application management, once you click add application you will be shown a long list of SaaS applications that can be configured with ease. Inside each connector, we've made it easy for you to configure and read instructions at the same time.
Select an application from the list. Each connector has some questions that should be answered before moving on (such as the hostname or the URL of your instance for the application). Answering these questions first will help automate the process going forward.
In case you are curious, you can check out IBM's full list of applications that are supported. If the application you are trying to onboard doesn't exist in the catalog, then you can always use the custom connector option which supports both OpenID connect and SAML2.0 specifications allowing IBM Verify to support more varieties of connectors that other vendors.
Don't have an application to add or test out? No problem, we've got you covered. Read more on adding a sample application if you don't have one.
Connect your users
At the core of IBM Verify is user management, otherwise known as identity management. In conjunction with applications, this is how your users (whether a consumer, employee, staff, student, etc) will get into those apps. Without a user account however, applications would useless.
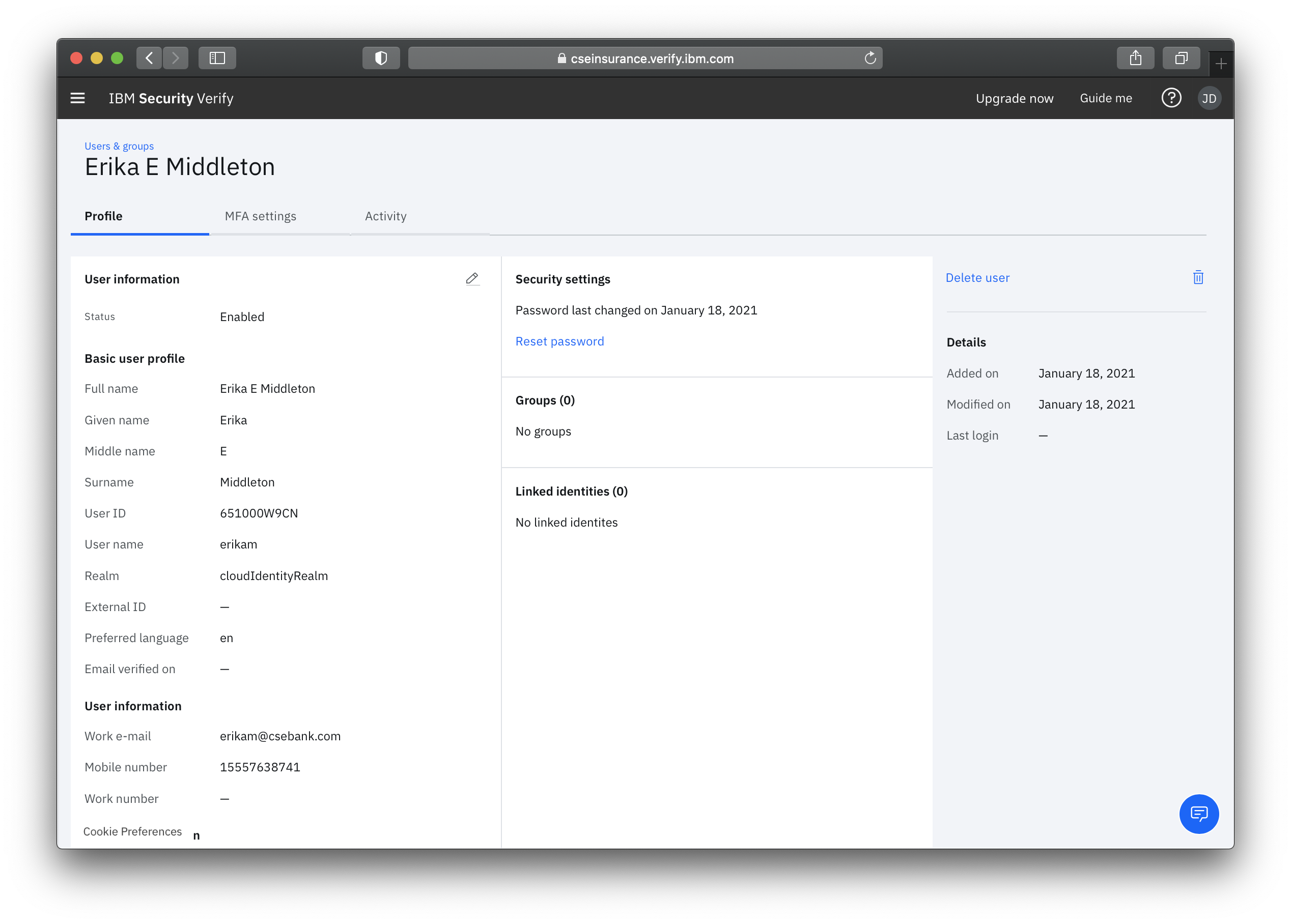
IBM Verify provides a robust directory service that can handle millions of users around the world. Use the built-in user directory to create local users that reside solely in your tenant. Verify also has the ability to bring in external users from a variety of different identity sources sources (Active Directory, LDAP, SAML, Social) and device managers (MaaS360, Intune, and JAMF).
Give your users a way to authenticate to Verify:
| Method | Config guide | Product documentation |
|---|---|---|
| Local users | User & group management | Managing users and groups |
| Active directory / LDAP | Connect to Active Directory | Configuring identity agents for authentication |
| Social providers | Using social providers | Adding a social provider identity source |
| SAML Enterprise | Coming soon | Adding a SAML identity source |
Updated 7 months ago
