Overview and use cases
Summary
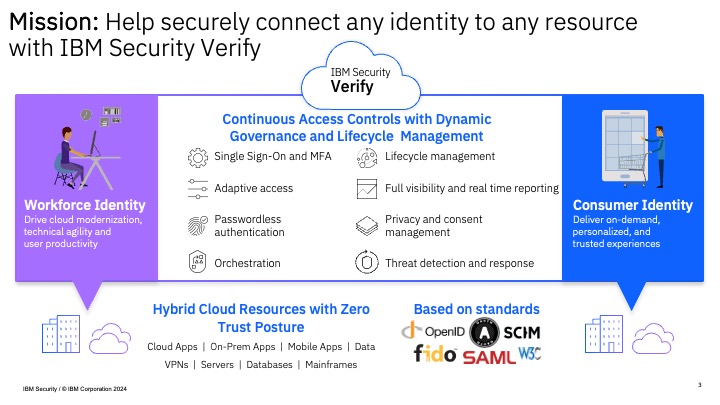
Organizations need unified identity repositories and policies to deliver cloud transformation and IT modernization, while enabling a remote workforce and increasing user productivity and security. Simultaneously as consumers pivot faster to digital channels, these same organizations need to provide a consistent, secure and frictionless experience across channels to their prospects, customers and citizens.
IBM Verify protects users and applications both inside and outside the enterprise, while enabling technical agility and operational efficiency as a cloud-native solution. Beyond single-sign on and multifactor authentication, Verify is a modernized, modular IDaaS that provides deep AI-powered context for risk-based authentication and adaptive access decisions, guided experiences for developer time-to-value and comprehensive cloud IAM capabilities. From privacy and consent management to holistic risk detection and identity analytics, Verify centralizes workforce and consumer IAM for any hybrid cloud deployment.
Continuous delivery
IBM Verify provides a continuous stream of new features that are made available to customers immediately. All features improve upon existing subscriptions and will never impact existing work streams or flows. Features can be turned on through self-service user interfaces in the administration console.
Centralized user management
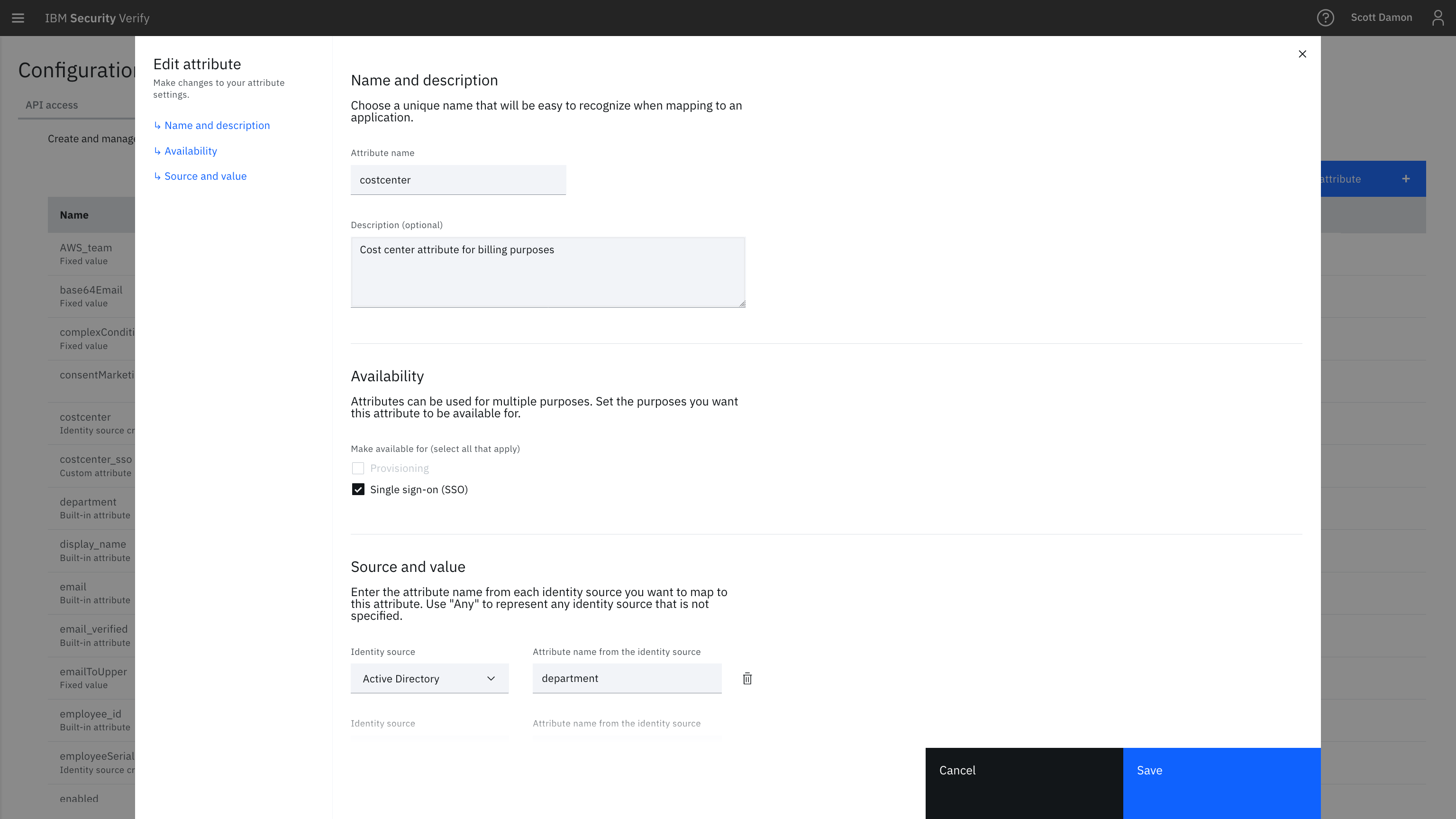
Managing users, their attributes, their relationships, their applications, etc is what IBM Verify does best. IBM Verify provides a centralized user management interface that can be managed through the admin UI or automatically through REST APIs .
Full profile management through System for Cross-domain Identity Management (SCIM 2.0) is supported for provisioning inbound from HR systems and outbound to applications and other endpoints.
Link multiple identities together for easier user migration and for a flexible user experience when user accounts live in multiple sources (such as social provider authentication ).
Single sign-on
Set up applications in minutes to connect users to their applications without missing a beat. Hundreds of application connectors are provided to make application onboarding simple, with side-by-side configuration and instructions so you never have to flip between windows.
IBM Verify is built upon open standards such as OpenID Connect and SAML 2.0. Onboard custom-developed applications that support single page web applications, browserless apps, and even TVs, Smart hubs, and more.
IBM Verify acts as an authentication broker connecting all of your users - wherever they may be - to all of your applications - no matter which single sign-on method they support.
Password-less authentication
Authenticate users without passwords to improve user agility. Within Verify, there are multiple passwordless methods at your disposal including FIDO2 WebAuthn . This allows you to bypass passwords completely and use Windows Hello or TouchID for user authentication.
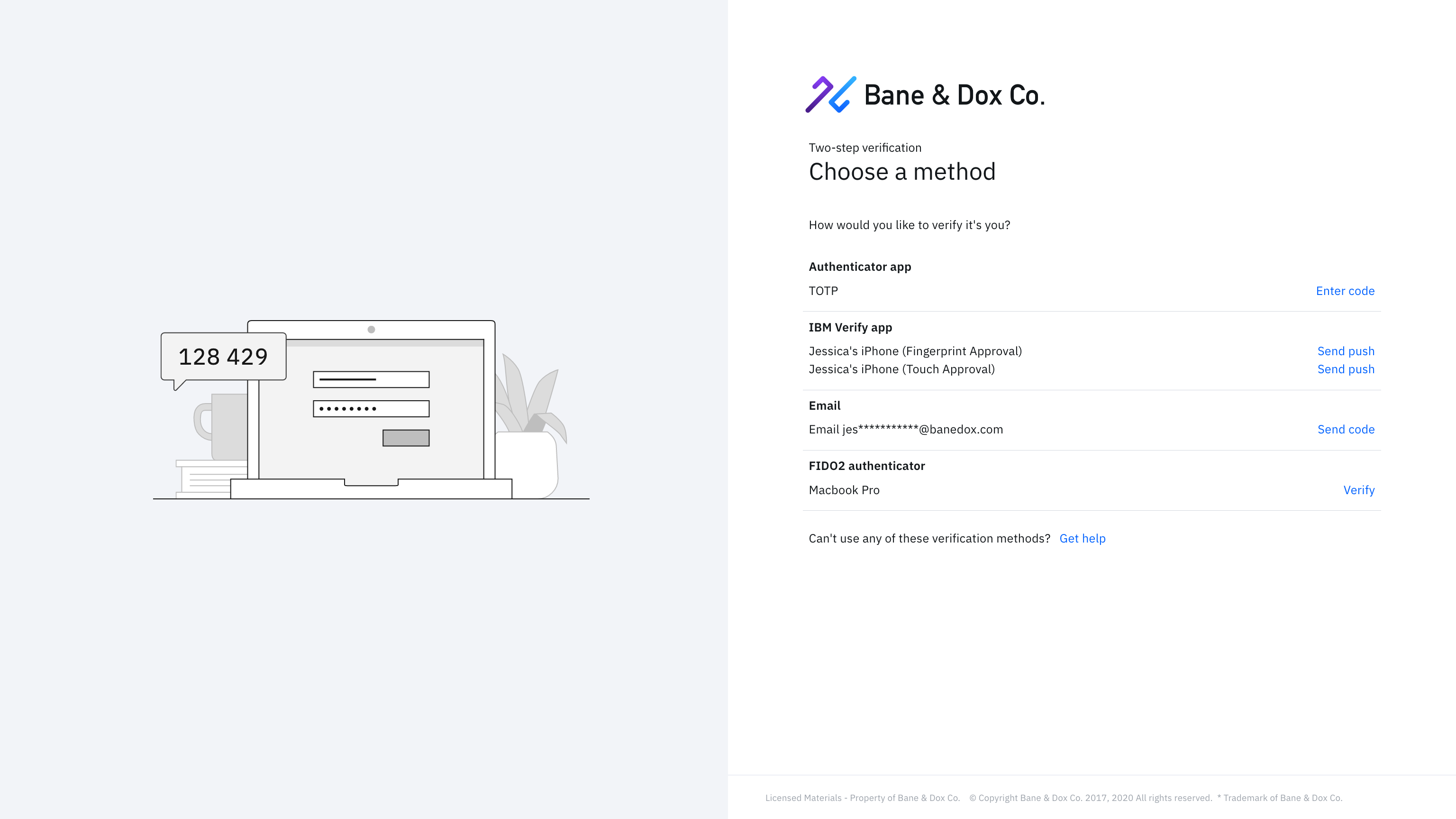
Multi-factor verification
Verify users with out-of-the-box MFA methods including:
- Knowledge questions
- SMS, Email, Voice callback one-time passcode (OTP)
- Time-based one-time passcode (TOTP)
- Push notification approval (IBM Verify app)
- Biometric approval for fingerprint and face recognition
Control and protect applications with granular access policies based on contextual conditions like network, geographic location, device fingerprinting, and user & group attributes. With MaaS360, you have the ability to also enforce device compliance.
In addition to web applications, use a single authenticator to verify users on Linux (RHEL, Ubuntu, SLES, Power, etc), AIX, IBM z, Windows Remote Desktop, and RADIUS (VPN).
Don't want to enroll users? You can utilize Verify's MFA capabilities without users lifting a finger.
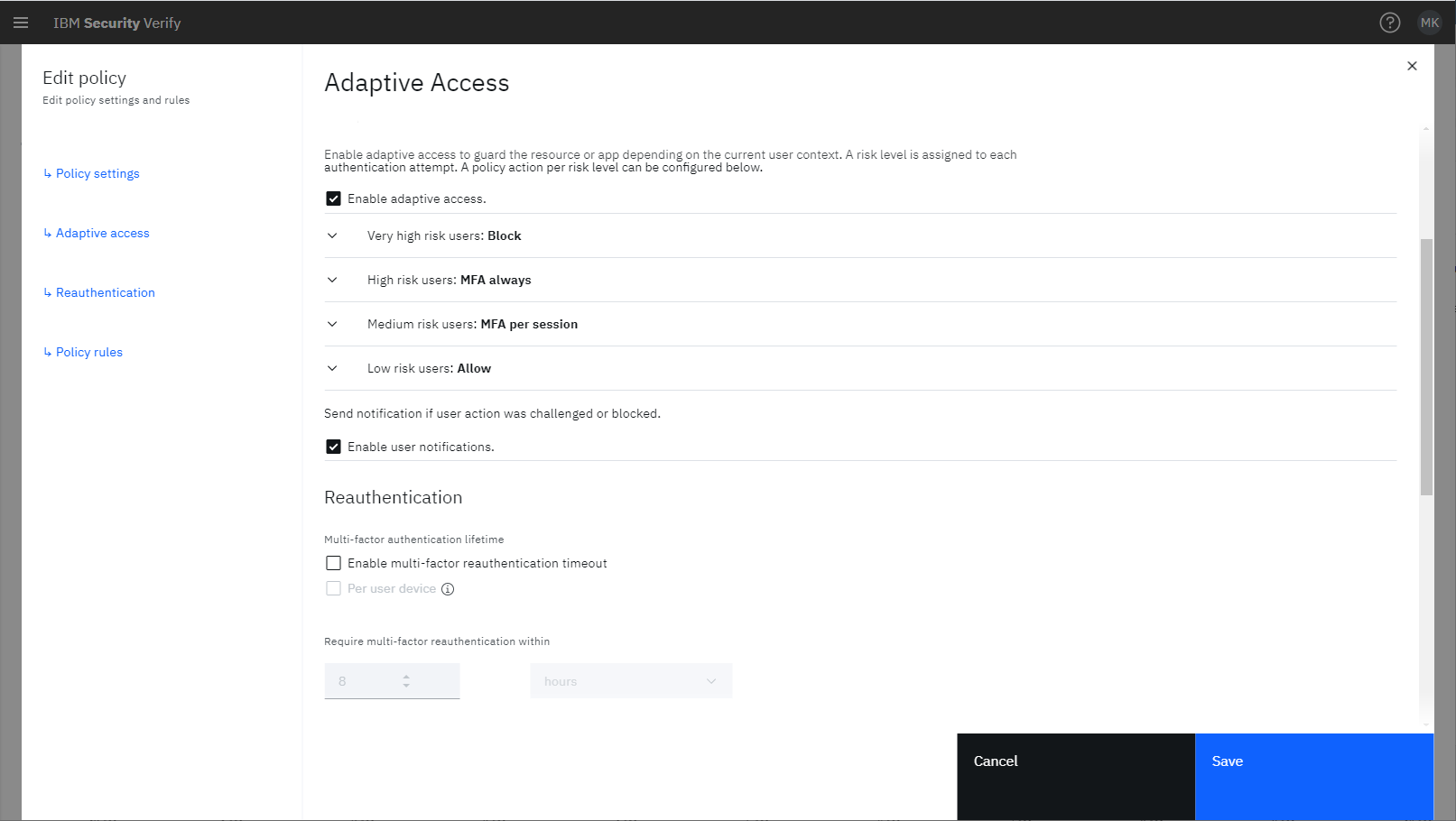
Risk-based authentication and adaptive access
Reduce user access friction across web applications without compromising on security. Create access rules in the Verify policy manager based on risk insights from IBM Trusteer, collected in a pre-defined, no code, web page.
Using well-established and deep insights from IBM Security's Trusteer platform, a risk score is generated based on contextual information provided by the user such as device fingerprinting, connection details, location, and behavioral anomalies. Without any code, proactively protecting apps is as simple as checking a box.
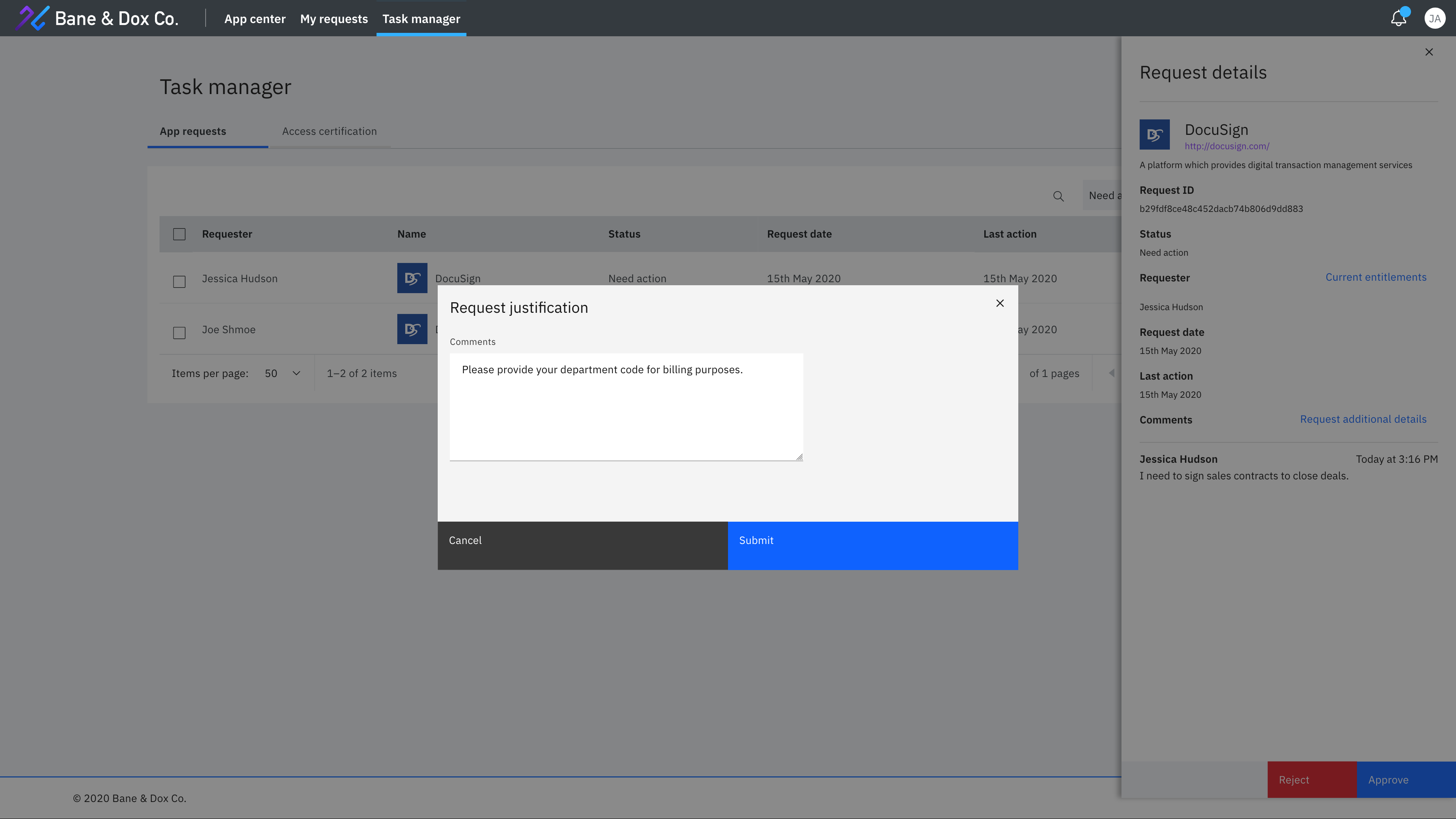
User lifecycle management
With Verify, connect application access with business governance workflows. Require justification from users and assign application owners or managers to approve access without complicated flow editors.
Automate user onboarding and offboarding with Verify's provisioning capabilities. Handle user provisioning to out-of-the-box adapters such as Google, Microsoft365 (Azure), Box, Salesforce, ZenDesk, and more. Verify has a custom connection option as well for standards based apps supporting SCIM2.0 for provisioning and deprovisioning. And when user's accounts change on applications, you can reconcile changes easily through Verify's admin console.
Updated 7 months ago
