User & group management
Introduction
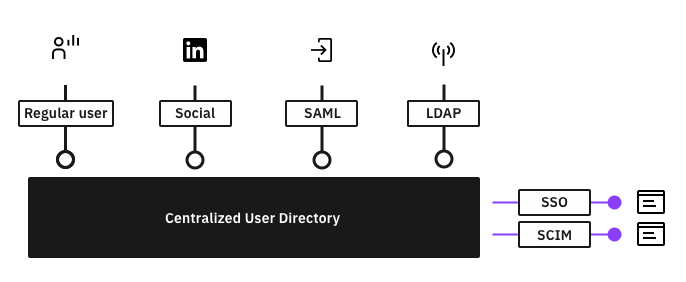
IBM Verify provides a robust centralized user directory for managing hundreds to millions of users from a single console to all customers. This is included for all customers because without a universal cloud user directory, IBM Verify wouldn't be an identity product.
This scalable technology that runs millions of users world wide has been used to handle citizens, bank clients, car customers, and more.
Management
There are many ways to manage user data in Verify. Through no-code and easy management through the user interface or through more complex system development, Verify satisfies use cases across the spectrum of complexity.
User types
There are two types of users in Verify: regular and federated. Regular users have local user passwords that are encrypted in Verify's directory. Federated users are metadata records of user information but no inherent authentication mechanism. Federated users are users that originated from an identity agent (like through LDAP or Active Directory ) or social providers. All federated users will authenticate with their third party identity provider, and then they will be allowed through into Verify.
Admin interface
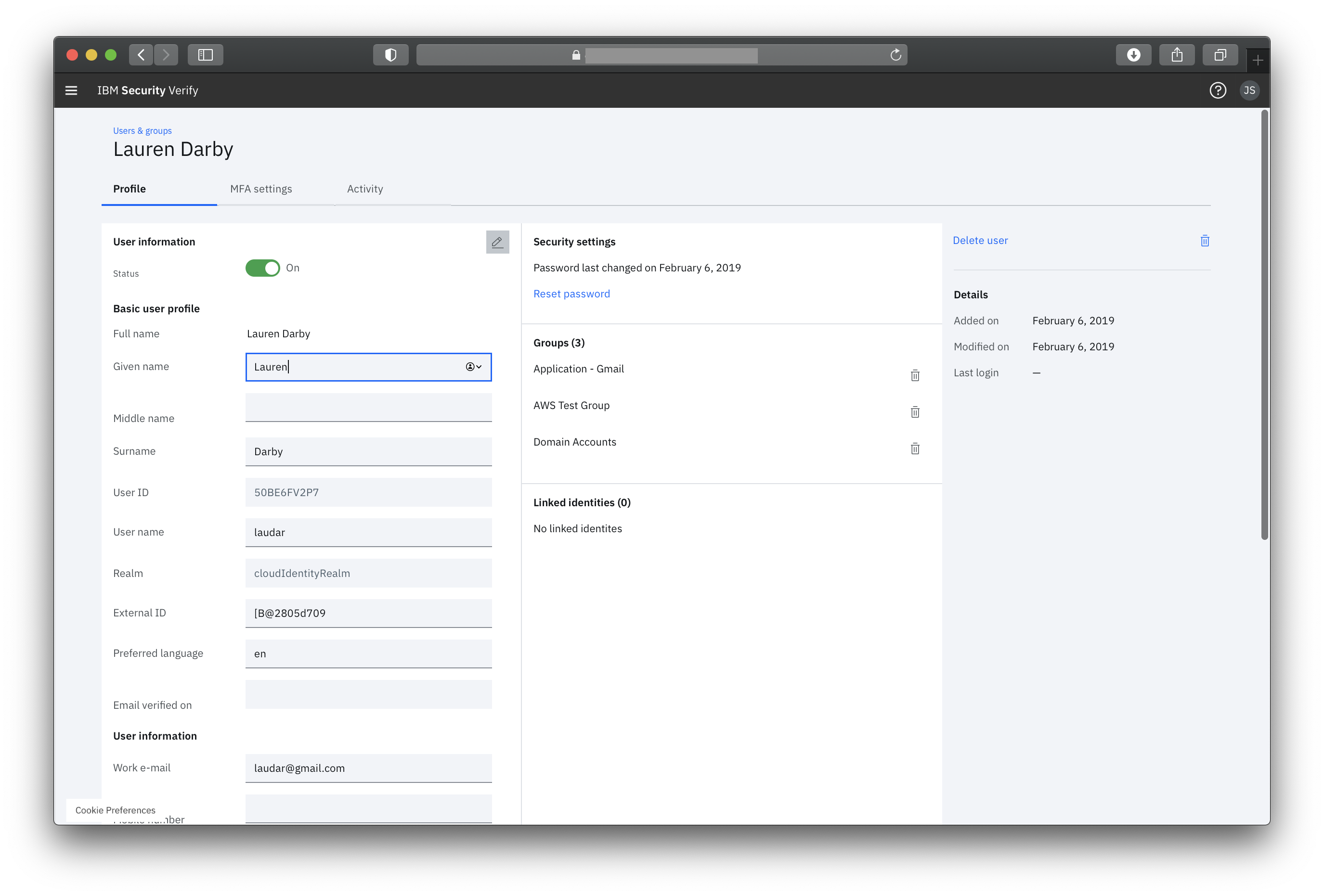
Every user that exists in Verify can be fully managed in the admin console. Manage standard attribute (name, email, phone, address, etc) and custom attribute values. View and manage 2nd factor enrollments to help users unlock their accounts. View account activity to visualize the user journey.
Standards based user management (SCIM)
Because of our commitment to modern standards, Verify uses the System for Cross-domain Identity Management (SCIM) specification that makes managing user identities in cloud-based applications easy.

This standard protocol allows for user repository synchronization from databases and enterprise applications (such as HR applications) without any custom coding. However, if custom coding is required, SCIM2.0 makes it easy. Create and manage users in the central user cloud directory through this method and Verify will automatically provision users (and changes) to target applications.
Identity linking
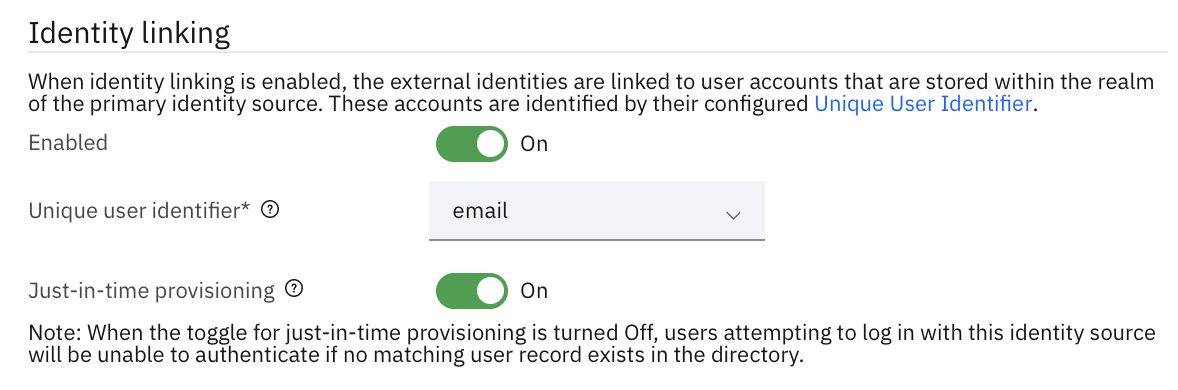
When bringing in multiple users through different identity sources, Verify can automatically link those accounts together when their unique identifiers match (like phone or email address). Engage your users with multiple ways of authentication, like Social providers, while providing a single identity for navigating across applications.
Managing account linking through Configuration and then clicking Identity sources. Every identity source has the ability to link accounts through just in time provisioning settings.
Attributes
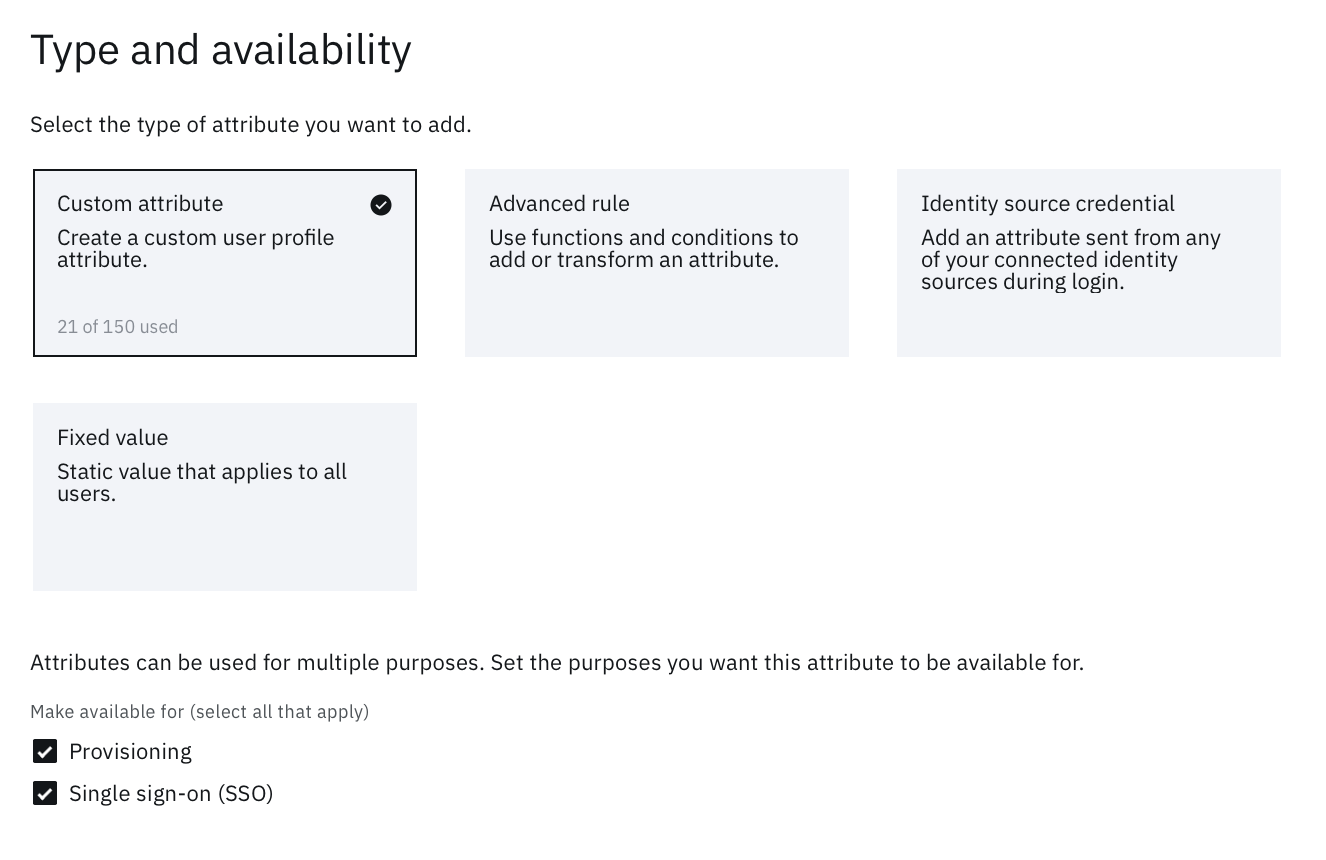
User's have various associations in their profile. From email to birthday, and frequent flier number to credit card number, user accounts are the single entity that defines an identity. Verify includes a standard user schema that includes basic user information (e.g. display name, email, phone, etc). 150 custom attributes can be added to extend the user schema to fit any use case. All of these attributes are available to be used in applications (ID token / SAML assertions).
All attributes have the ability to be mapped from a source to a target. Map a SAML attribute and a social identity source attribute to a single attribute.
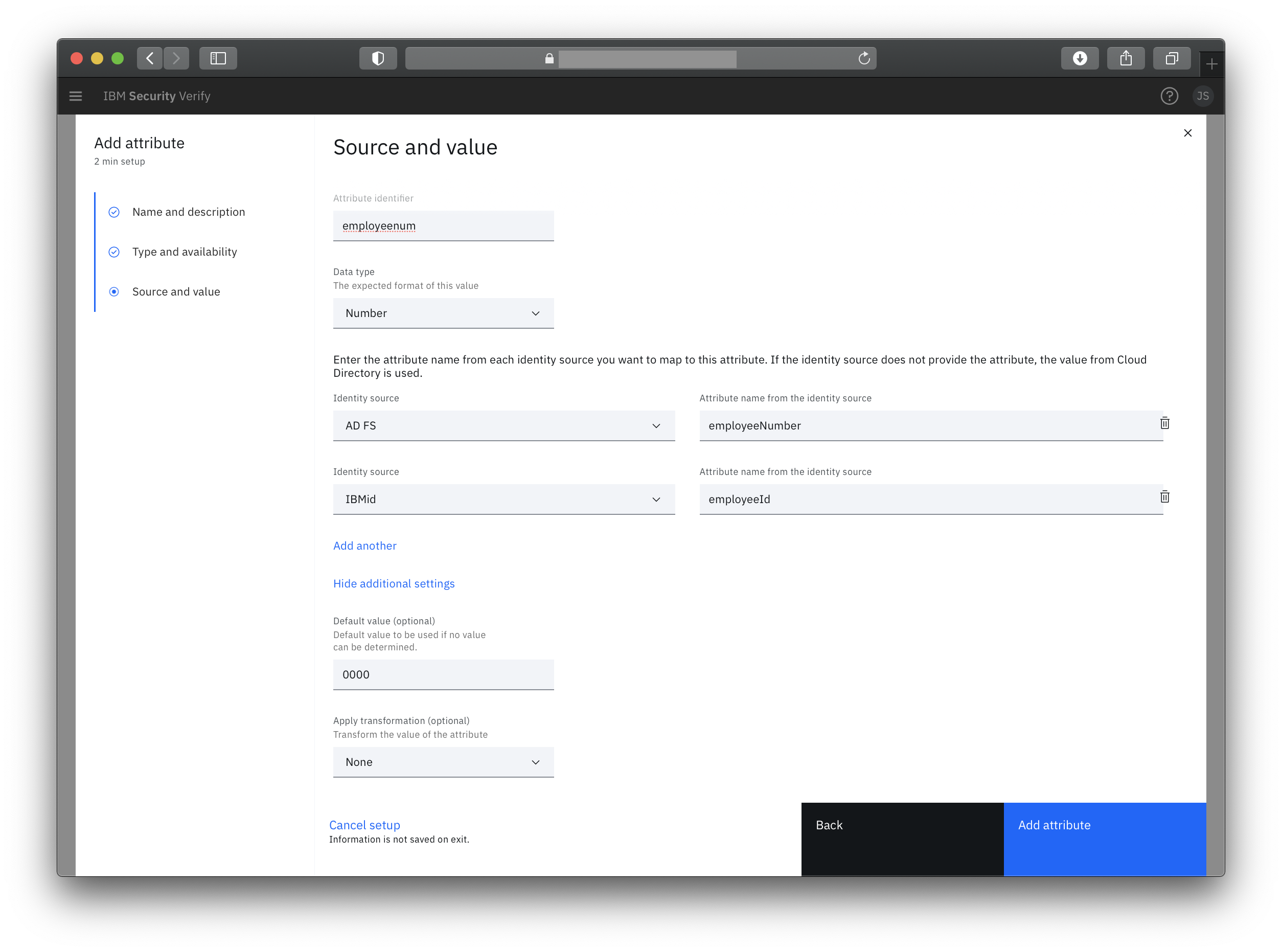
If you have a need to manipulate attributes in anyway, you can apply out of the box functions, like base64 encode or URI encode, through a simple drop down choice. However, more complex functions can be written using attribute functions. Rules can be single-line expressions or multi-line complex functions to completely transform the user's data. This is a clean and simple way to manage attribute values without having to write any complex syntax.
statements:
- context: "workEmails := has(user.emails) ? user.emails.filter(e, e.type == 'work') : []"
- context: "workEmail := size(context.workEmails) > 0 ? context.workEmails[0].value : ''"
- if:
match: context.workEmail != ""
block:
- context: cn := context.workEmail.substring(0, context.workEmail.lastIndexOf('@'))
- if:
match: context.cn != ""
block:
- return: context.cn + "@github.com"
- return: ""
Updated 7 months ago
