Threat Intelligence in Verify
Securing organizations against large-scale identity attacks in IBM Verify
Data breaches due to an increase in Digital Transformation across industries are proving to be costly to remediate and adversely impacting brand reputation. As per Cost of a Data Breach Report 2022, the use of stolen or compromised credentials remains the most common cause of a data breach. Breaches caused by stolen or compromised credentials had an average cost of USD 4.50 million. These breaches had the longest lifecycle — 243 days to identify the breach, and another 84 days to contain the breach. Hence customers are looking for visibility into suspicious traffic coming to their tenants and take proactive action to avoid Identity-related attacks. Identity-based attacks also include continued resource attacks through numerous login attempts and second-factor attempts. Organizations must remain alert and aware, 24x7, creating much consternation and discomfort for teams protecting these resources.
Because of these threat vectors and organization concerns, IBM Verify SaaS introduces a feature to analyze traffic across all tenants to detect indicators of compromise and anomalies for identity-related attacks such as Brute force, Credential Stuffing attacks, Login deviations, and soon more to come. These alerts will provide visibility into suspicious traffic to the organization's identity and access management (IAM) admins so that they can take proactive remediation actions such as blocking an IP address or disabling the user account(s).
Note
This feature is available as part of a closed Beta. Please reach out through IBM Support if you have an interest to have this enabled
in your tenant.
Overview
IBM Verify helps organizations secure against large-scale identity-based attacks. One mechanism is through the use of advanced threat detection based on anomalies found in traffic across all customers in IBM Verify. This is described in greater detail in this document.
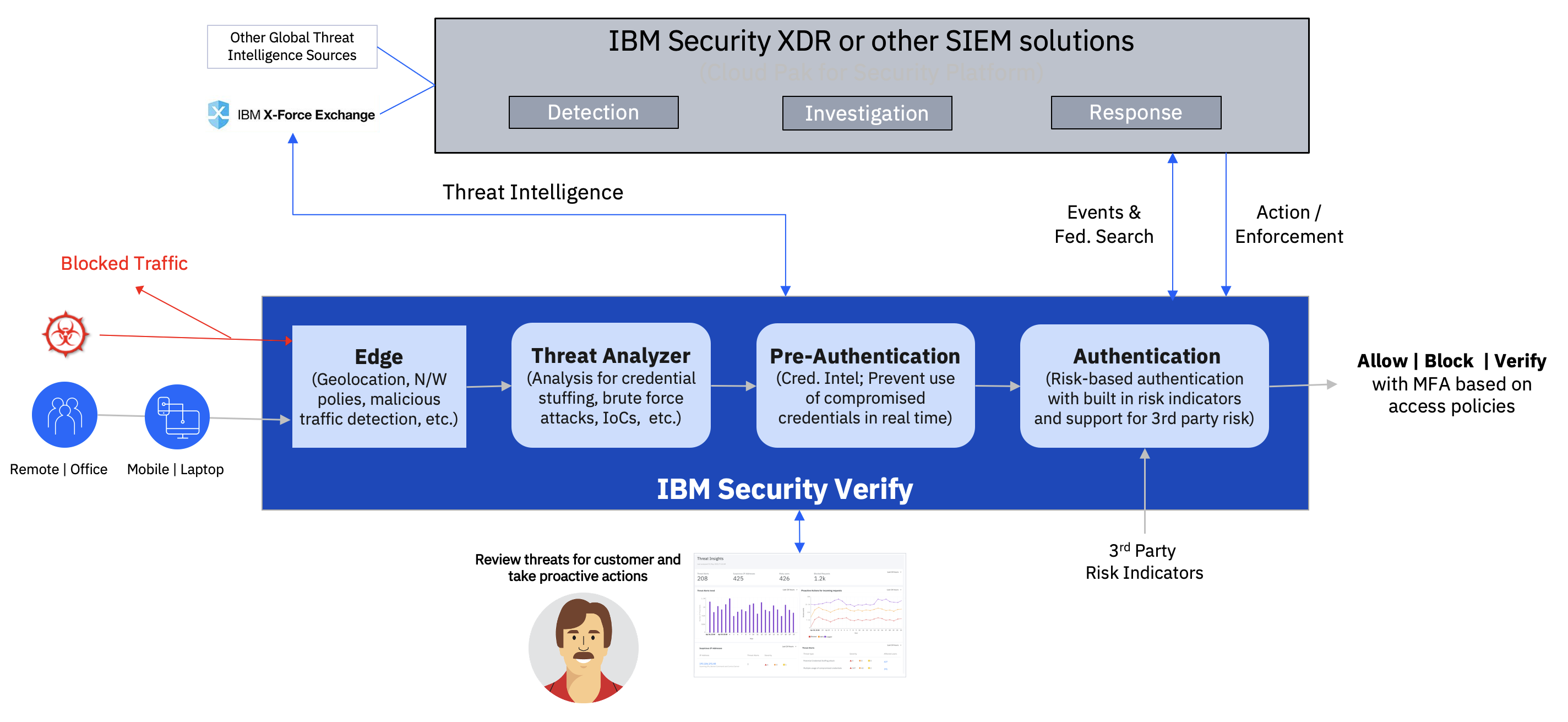
Edge protection
Whenever a request comes to Verify, it is first analyzed at the Edge to block suspicious traffic to prevent attacks like Command Injection, Cross Site Scripting (XSS), DDOS, Invalid HTTP, PHP Injection, Remote File Inclusion, SQL Injection, Trojan, etc. With an edge security solution, Verify also uses Geo-location and network policies to secure Infrastructure. This includes Web Application Firewall rules, IP rules, DOS Protection based on rate limits per IP, and client reputation based on prior behavior of individual and shared IP addresses. It is designed to stop malicious clients before they can attack.
In addition, the bot manager detects, alerts and prevents bot traffic. Additionally, custom rules are defined by IBM to deny suspicious traffic that may not fall under any of the standard protections provided by the WAF service. This capability in IBM Verify has existed for years and is not new.
The security detection and response team at IBM Verify monitors for threats and suspicious activity across its ecosystem of thousands of customers and partners, and it responds by taking appropriate action. Known malicious IPs are added to a block-list at the edge layer along with various security controls covering encryption, tenant data security, network segregation and security, and more. This prevents access from these IPs to any Verify tenant.
Threat Analyzer
The next layer of defense is the Threat Analyzer which analyzes incoming traffic to detect potential identity-related attacks such as credential stuffing, brute force attacks, login anomalies, and more. It also leverages threat intelligence from IBM Security X-Force Exchange for IP addresses about reputation and historical data of activities such as malware, bots, and more. IBM Security X-Force Exchange is a cloud-based threat intelligence sharing platform enabling users to rapidly research the latest security threats, aggregate actionable intelligence, and collaborate with peers. IBM X-Force Exchange, supported by human- and machine-generated intelligence, leverages the scale of IBM X-Force to help users stay ahead of emerging threats.
This is the new capability discussed in this article.
The threat analyzer uses historical threat patterns generated across all IBM Verify tenants. Thus, any tenant can take advantage of the alerts generated by the threat analyzer, even if there was no previous attack. This allows for proactive mitigation of attacks.
Threat Analyzer will initially track four major threat vectors. These threat vectors analyzed will be continually enhanced and augmented, and new threat models will be added for additional vectors, without requiring any specific tenant configuration. The currently supported models are described below.
-
X-Force Actionable IPs: This threat vector looks at the data feeds provided by IBM Security X-Force. This data feed is a cooperative of signals evaluated and aggregated to identify and classify suspicious IPs through telco and other network data IBM Security X-Force participates within and contributes feeds into. This is aimed at preventing known, suspicious IPs from accessing the system.
-
Failed logins: This threat vector looks at failed login patterns for both first and second factor to determine if the failed logins are within the normal threshold experienced or are deviating from normal thresholds. This is aimed at preventing large scale attacks via brute force logins from the IPs that are using this pattern of attack.
-
Login deviations: This threat vector looks at successful login patterns for both first and second factor to determine if the successful logins are within the normal threshold experiences or are deviating from normal thresholds. This is aimed at preventing successful stolen credential logins from the IPs that are using this pattern of attack.
-
Credential stuffing/compromised credentials: This threat vector looks at the use of common or phished passwords during login to identify IPs that persist the behavior of using common or phished passwords. This is aimed at preventing common or phished credential logins from the IPs that are using this pattern of attack.
Pre-Authentication
Once it is confirmed that traffic is not suspicious then it goes for Pre-Authentication checks. It includes checking if the incoming credential is a common password or a previously compromised credential. If this check is passed, IBM Verify applies access policies to determine if the request should be allowed/blocked or if further verification is required.
This will be part of a future update.
Authentication
IBM Verify offers an adaptive and robust risk engine that can be configured to evaluate access control rules based on request context (such as Geography and IP subnet ranges), user context and attributes, compliance state of a device drawn from a device management solution, dynamic user behavior biometrics, etc. Based on the outcome of a policy evaluation, the decision may range from allowing the transaction, blocking it, challenging for additional authentication factors or to direct the user to an external system.
The risk-based authentication capability is Adaptive Access. MFA options include SMS/Email OTP, TOTP, and IBM Verify Authenticator app (ex: push, user presence, and biometric). Passwordless options also include QRCode and passkeys (FIDO).
Exporting or notifying threat events
This section describes different ways threat events can be queried and pushed to external tools such as SIEM for further investigation. You can choose the one which you are already using to query other events. If you are configuring it for the first time, then we recommend using the notification webhooks approach.
-
Notification webhooks: This can be done by specifying
event_type = threatas interest while adding a custom event in the event subscription for notification webhook configuration. For more details on how to configure notification webhook refer to Creating a notification webhook -
Query threat events using events API: This can be done by specifying
event_type = threatas a filter for events API. For more details on how to use Events API refer to Pulling activity and event data -
QRadar DSM: QRadar DSM can be configured to query threat events by selecting
event_type = threat. For more details on how to use QRadar DSM refers to IBM Security QRadar
Threat events and investigation
This section describes various alerts generated by IBM Verify and provides guidance on possible steps for further investigations to determine if traffic is suspicious or not. It also provides details on proactive remediation actions if traffic is determined to be suspicious.
Alert Name: Actionable IP addresses from XFE
Indicates: Brute force attack
Details: High-risk IP addresses are involved in malicious activities, such as performing password spray, and Botnet C&C, and may indicate compromised accounts in the last 1 hour. Here are four categories of Actionable IP addressed that we are using:
- Scanning IPs (scanning)
- Malware (mw)
- Bots (bots)
- Botnet Command and Control Server (c2server)
Investigation: Analyze traffic to understand if any remediation action is required.
- Identify the affected tenant URL (
top5_affected_tenantname) - Identify the type of events generated due to activity from actionable IP addresses (
top5_affected_event_type) - If management events are generated, identify if resetting passwords or the addition of MFA devices is done for one or more users. This could indicate the risk of account takeover.
- Identify the list of suspicious IPs and validate whether any login requests were successful from these IPs.
xfe_confirmed_malicious_ips: List of actionable IPs from which SSO, Authentication, or management events are found in the last 1 hourxfe_threat_insight: Categories associated with actionable Ips. For instance, "Found 3 known malicious IPs, having categories: anonsvcs: 0, bots: 3, c2server: 0, mw: 0, scanning: 0."suspicious_ips: List of actionable IPs found in the last hour along with fail %, # of success, and # of failed login events for each IP.
- Identify the severity of the alert :
- Critical: If 5 or more IP addresses are found from actionable IPs
- Warning: If 1 or <5 IP addresses are found from actionable IPs
- If requests from actionable IP addresses are failed, then
top5_affected_data_causegives more information on the cause of failures. - Identify affected usernames (
top5_affected_data_username) which show the top 5 accounts mostly used during the attack. - Identify if any account was accessed successfully (
compromised_users) from suspicious IPs - Identify the affected application (
top5_affected_data_applicationname)
Possible remediation Actions:
- Block IP address if traffic looks suspicious. Refer to the block IPs section for more details.
- Block user accounts if they are found to be compromised. Refer to the block accounts section for more details.
{
"rule_id": "XFE_ACTIONABLE_IP",
"rule_name": "Actionable IP addresses from XFE",
"summary": "Actionable IP addresses from XFE: 115 risky events are observed from 2022-12-17 11:00:00 UTC to 2022-12-17 12:00:00 UTC.",
"source": "[('tenantid', '874f131f-79a9-4581-b078-de7681091fbc')]",
"component": "Login activity",
"anomalous_event_count": 115,
"normal_traffic_volume": 0,
"start_time": 1671274800000,
"end_time": 1671278400000,
"date": "2022-12-17",
"severity": "critical",
"index": "event-*",
"impacted_user_count": 22,
"suspicious_ips": "[['ip', 'fail_percentage', 'failure_count', 'success_count'],
['193.118.55.162', 100.0, 5, 0], ['103.153.190.238', 40.0, 2, 3], ['209.141.36.112', 100.0, 1, 0],
['198.235.24.173', 100.0, 1, 0], ['140.213.15.89', 33.33, 1, 2], ['197.210.53.113', 33.33, 1, 2],
['47.9.0.237', 25.0, 1, 3], ['164.100.133.253', 0.0, 0, 2], ['197.210.70.62', 0.0, 0, 1],
['171.245.218.108', 0.0, 0, 1], ['116.50.59.204', 0.0, 0, 1], ['102.88.62.82', 0.0, 0, 1],
['223.196.170.127', 0.0, 0, 2], ['180.247.45.59', 0.0, 0, 1], ['129.205.124.227', 0.0, 0, 7],
['105.113.20.110', 0.0, 0, 2], ['213.55.85.89', 0.0, 0, 3], ['105.178.43.219', 0.0, 0, 7],
['103.134.0.5', 0.0, 0, 1], ['103.28.246.254', 0.0, 0, 3], ['102.89.34.16', 0.0, 0, 4],
['197.211.58.30', 0.0, 0, 5], ['121.101.133.181', 0.0, 0, 2]]",
"anomalous_suspicious_ips": [
"193.118.55.162", "103.153.190.238", "209.141.36.112",
"198.235.24.173", "140.213.15.89", "197.210.53.113",
"47.9.0.237", "164.100.133.253", "197.210.70.62",
"171.245.218.108", "116.50.59.204", "102.88.62.82",
"223.196.170.127", "180.247.45.59", "129.205.124.227",
"105.113.20.110", "213.55.85.89", "105.178.43.219",
"103.134.0.5", "103.28.246.254", "102.89.34.16",
"197.211.58.30", "121.101.133.181"
],
"compromised_users": "{'105.178.43.219': ['[email protected]'], '129.205.124.227': ['[email protected]'], '197.211.58.30': ['[email protected]'], '102.89.34.16': ['[email protected]'], '103.153.190.238': ['[email protected]'], '103.28.246.254': ['[email protected]'], '213.55.85.89': ['[email protected]'], '47.9.0.237': ['[email protected]'], '105.113.20.110': ['[email protected]'], '121.101.133.181': ['[email protected]'], '140.213.15.89': ['[email protected]'], '164.100.133.253': ['[email protected]'], '197.210.53.113': ['[email protected]'], '223.196.170.127': ['[email protected]'], '102.88.62.82': ['[email protected]'], '103.134.0.5': ['[email protected]'], '116.50.59.204': ['[email protected]'], '171.245.218.108': ['[email protected]'], '180.247.45.59': ['[email protected]'], '197.210.70.62': ['[email protected]']}",
"xfe_threat_insight": "Found 23 known malicious IPs, having categories: bots: 22, c2server: 0, mw: 0, scanning: 2",
"xfe_confirmed_malicious_ips": [
"129.205.124.227", "116.50.59.204", "102.89.34.16",
"193.118.55.162", "103.153.190.238", "180.247.45.59",
"164.100.133.253", "197.210.70.62", "171.245.218.108",
"198.235.24.173", "102.88.62.82", "213.55.85.89",
"105.178.43.219", "103.134.0.5", "209.141.36.112",
"103.28.246.254", "197.211.58.30", "47.9.0.237",
"197.210.53.113", "223.196.170.127", "121.101.133.181",
"105.113.20.110", "140.213.15.89"
],
"top5_affected_event_type": "{'risk': 44, 'authentication': 36, 'sso': 31, 'management': 4}",
"most_significant_event_type": [
"risk",
"authentication",
"sso"
],
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 115}",
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_tenantname": "{'tenant1.abc.com': 92, 'tenant2.abc.com': 23}",
"most_significant_tenantname": [
"tenant1.abc.com"
],
"top5_affected_data_subtype": "{'oidc': 23, 'user_password': 17, 'mfa': 11, 'saml': 8, 'token-exchange': 7}",
"most_significant_data_subtype": [
"oidc",
"user_password",
"mfa"
],
"top5_affected_data_scope": "{'openid': 20, 'openid email': 2, 'openid profile': 1}",
"most_significant_data_scope": [
"openid"
],
"top5_affected_data_cause": "{
'Token Exchange Successful': 7,
\"CSIAC4610E Unable to retrieve the application's configuration for the Entity ID https://18.135.137.31/samlsp.em7?action=metadata because there is no match found.\": 5,
'Authenticated user \"[email protected]\" successfully.': 2,
'Authenticated user \"[email protected]\" successfully.': 2,
'The system failed to authenticate user \"[email protected]\" because of \"INVALID_CREDS\".': 2
}",
"most_significant_data_cause": [
"Token Exchange Successful",
"CSIAC4610E Unable to retrieve the application's configuration for the Entity ID https://18.135.137.31/samlsp.em7?action=metadata because there is no match found.",
"Authenticated user \"[email protected]\" successfully."
],
"top5_affected_data_sourcetype": "{'clouddirectory': 24, 'oidc': 7, 'saml': 1}",
"most_significant_data_sourcetype": [
"clouddirectory",
"oidc"
],
"top5_affected_servicename": "{'risk': 44, 'oidc_rt': 23, 'profilemgmt': 17, 'factors': 11, 'saml_runtime': 9}",
"most_significant_servicename": [
"risk",
"oidc_rt",
"profilemgmt"
],
"top5_affected_data_providerid": "{'https://18.135.137.31/samlsp.em7?action=metadata': 5, 'https://18.135.144.228/samlsp.em7?action=metadata': 1, 'https://3.123.117.242/samlsp.em7?action=metadata': 1, 'https://tenant1.abc.com/saml/sps/saml20ip/saml20': 1, 'https://sso.everbridge.net/GNMManager': 1}",
"most_significant_data_providerid": [
"https://18.135.137.31/samlsp.em7?action=metadata",
"https://18.135.144.228/samlsp.em7?action=metadata",
"https://3.123.117.242/samlsp.em7?action=metadata"
],
"top5_affected_data_grant_type": "{'authorization_code': 18, 'resource_owner': 7, 'implicit': 5}",
"most_significant_data_grant_type": [
"authorization_code",
"resource_owner"
],
"top5_affected_data_mfamethod": "{'Email OTP': 15}",
"most_significant_data_mfamethod": [
"Email OTP"
],
"top5_affected_data_username": "{'[email protected]': 16, '[email protected]': 12, '[email protected]': 10, '[email protected]': 8, 'UNKNOWN': 7}",
"most_significant_data_username": [
"[email protected]",
"[email protected]",
"[email protected]",
"[email protected]"
],
"top5_affected_geoip_country_name": "{'Nigeria': 46, 'India': 20, 'Indonesia': 20, 'Rwanda': 12, 'Netherlands': 5}",
"most_significant_geoip_country_name": [
"Nigeria",
"India",
"Indonesia"
]
}
Alert Name: Potential credential stuffing (PCS) attack
Indicates: Credential stuffing attack
Details: Sudden increase in username password failures as compared to normal behavior for SSO or Auth events in the last 14 days. Alert will have details on rouge IP addresses found during the attack.
Investigation: Analyze traffic to understand if it could be a real attack or not and if any remediation action is required.
-
Identify the affected tenant URL (
top5_affected_tenantname). -
Identify the list of suspicious IPs and validate whether any login requests were successful from these IPs.
xfe_confirmed_malicious_ips: List of actionable IPs from which SSO, Authentication, or management events are found in the last 1 hourxfe_threat_insight: Categories associated with actionable Ips. E.g.: "Found 3 known malicious IPs, having categories: anonsvcs: 0, bots: 3, c2server: 0, mw: 0, scanning: 0."suspicious_ips: List of actionable IPs found in the last hour along with fail %, # of success, and # of failed login events for each IP.
-
Identify severity of the alert:
- Critical: if number of anomalous events are
> max(5*normal_failure_count, 10000). - Warning: if number of anomalous events are between
[min(3* normal traffic volume, 5000), 10000]
- Critical: if number of anomalous events are
-
top5_affected_data_causegives more information on the cause of failures. -
Identify affected usernames (
top5_affected_data_username) which show the top 5 accounts mostly used during the attack. -
Identify if any account was accessed successfully (
compromised_users) from suspicious IPs -
Identify the affected application (
top5_affected_data_applicationname) -
normal_traffic_volumeprovides a baseline count based on the last 14 days of events compared with events in the last 1 hour.anomalous_event_countis the difference between total events in the last 1 hr and normal_traffic_volume. -
In some cases, an increase in username and password failures could be due to the onboarding of more users or the onboarding of new applications. Identify if this could be a possible reason for the alert.
-
The following additional fields can be analyzed to get further context for the investigation to debug affected components during the attack or for operational issues
most_significant_data_client_namemost_significant_data_provideridmost_significant_data_redirecturlmost_significant_data_scopemost_significant_data_subtypemost_significant_geoip_country_namemost_significant_servicename
-
You can see the number of events for each of the values corresponding to the above attributes in their respective
top5_affected_<FIELD NAME>attribute. -
Typically, in addition to this alert there might be other alerts generated during the attack such as
- Multiple failed login attempts from IP Address (or)
- Abnormal number of failed SSO/Authentication events observed per tenant.
- Based on context from previous steps, determine if it could be a real attack or not.
Some known analysis patterns:
- Identify
xfe_confirmed_malicious_ipslist. If any IP is found in the category, it can be directly blocked or can be reported as an attack with high confidence. - Look at the statistics of IPs in
suspicious_ipslist- If Most of the failed events are from single IP and the remaining all have a very less number of failure events then someone may have run a script/application by configuring a wrong username/password (Identify valid username(s) accessed from the IP). Also, look at the cause of failure and
top5_affected_data_applicationnameto see if it is one of the known issues. - If multiple IPs have a significant failure count in the suspicious IP list then it is highly likely to be an attack. Identify the
top5_geoip_country_namein the alert and also the country and username distribution for the high failure suspicious IPs individually. - If failures are for a specific application then it could be due to misconfiguration of the application. Check with the application owner.
- If Most of the failed events are from single IP and the remaining all have a very less number of failure events then someone may have run a script/application by configuring a wrong username/password (Identify valid username(s) accessed from the IP). Also, look at the cause of failure and
- For authentication events, if most failure causes have strings like
INVALID_CREDSin them, then it may be an attack.
Possible remediation Actions:
-
If unsure about whether it is an attack => Monitor the traffic to determine if traffic with username password failure is increasing.
-
If confirmed as an attack, then block the IPs in
anomalous_suspicious_ipsattribute. Refer to block IPs section for more details. -
Accounts that were successfully logged in from suspicious IPs could potentially be compromised. The potentially compromised usernames corresponding to each suspicious IP can be found in
compromised_usersattribute. For compromised accounts, customers can decide action if they want to reset password or disable these accounts. Refer to block accounts section or prompt for password reset section for more details.
{
"rule_id": "CREDENTIAL_STUFFING_SSO",
"rule_name": "Potential credential stuffing attack (SSO)",
"summary": "Potential credential stuffing attack (SSO): 31348 anomalous events are observed, beyond normal traffic volume, from 2022-11-23 17:00:00 UTC to 2022-11-23 18:00:00 UTC.",
"source": "[('tenantid', '874f131f-79a9-4581-b078-de7681091fbc'), ('tenantname', 'tenant1.abc.com'), ('data.result', 'failure')]",
"component": "Login activity",
"anomalous_event_count": 31348,
"normal_traffic_volume": 1004,
"start_time": 1669222800000,
"end_time": 1669226400000,
"date": "2022-11-23",
"severity": "critical",
"index": "event-sso-*",
"impacted_user_count": 32090,
"impacted_apps_count": 5,
"suspicious_ips": "[['ip', 'fail_percentage', 'failure_count', 'success_count'],
['52.117.163.162', 98.72, 10517, 136], ['169.50.223.22', 98.53, 5502, 82], ['169.50.223.24', 98.42, 5431, 87],
['169.59.129.120', 98.44, 5242, 83], ['169.59.129.116', 98.67, 5185, 70]]",
"anomalous_suspicious_ips": [
"169.50.223.22",
"169.50.223.24",
"169.59.129.116",
"169.59.129.120",
"52.117.163.162"
],
"compromised_users": "{'52.117.163.162': ['[email protected]', '[email protected]', '[email protected]'], '169.50.223.24': ['[email protected]', '[email protected]', '[email protected]'], '169.59.129.120': ['[email protected]', '[email protected]', '[email protected]', '[email protected]'], '169.50.223.22': ['[email protected]', '[email protected]', '[email protected]'], '169.59.129.116': ['[email protected]', '[email protected]']}",
"xfe_threat_insight": "Found 1 known malicious IPs, having categories: anonsvcs: 0, bots: 0, c2server: 0, mw: 1, scanning: 0.",
"xfe_confirmed_malicious_ips": ['52.117.163.162'],
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 32352}",
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_tenantname": "{'tenant1.abc.com': 32352}",
"most_significant_tenantname": [
"tenant1.abc.com"
],
"top5_affected_servicename": "{'oidc_rt': 32352}",
"most_significant_servicename": [
"oidc_rt"
],
"top5_affected_data_subtype": "{'oidc': 32352}",
"most_significant_data_subtype": [
"oidc"
],
"top5_affected_data_scope": "{'openid': 32352}",
"most_significant_data_scope": [
"openid"
],
"top5_affected_data_cause": "{'CSIAQ0264E The user name or password is invalid.': 32321, 'CSIAQ0264E El nombre de usuario o la contraseña no es válido.': 12, 'CSIAQ0264E O nome do usuário ou a senha é inválida.': 9, 'CSIAQ0264E 用户名或密码无效。': 4, 'CSIAQ0264E 사용자 이름 또는 비밀번호가 올바르지 않습니다.': 2}",
"most_significant_data_cause": [
"CSIAQ0264E The user name or password is invalid."
],
"top5_affected_data_applicationname": "{'urx_next': 31877, 'ABC_PROD_CLOUD': 347, 'ABC Cloud IAM production - global': 117, 'ABC Cloud IAM staging - global': 7, 'ABC Cloud IAM integrationtest': 4}",
"most_significant_data_applicationname": [
"urx_next"
],
"top5_affected_data_client_name": "{'urx_next': 31877, 'ABC_PROD_CLOUD': 347, 'ABC Cloud IAM production - global': 117, 'ABC Cloud IAM staging - global': 7, 'ABC Cloud IAM integrationtest': 4}",
"most_significant_data_client_name": [
"urx_next"
],
"top5_affected_data_redirecturl": "{'UNKNOWN': 32352}",
"most_significant_data_redirecturl": [
"UNKNOWN"
],
"top5_affected_data_providerid": "{}",
"most_significant_data_providerid": [],
"top5_affected_data_username": "{'[email protected]': 319, '[email protected]': 17, '[email protected]': 9, '[email protected]': 6, '[email protected]': 6}",
"most_significant_data_username": [
"[email protected]"
],
"top5_affected_geoip_country_name": "{'United States': 32334, 'Australia': 17, 'United Kingdom': 1}",
"most_significant_geoip_country_name": [
"United States"
]
}
Alert Name: Multiple failed login attempts from IP Address
Indicates: Brute force or Credential stuffing attack
Details: Sudden increase in failed logins from an IP address as compared to normal behavior for SSO or Auth events in the last 7 days.
Investigation Steps: Analyze traffic to understand if it could be a real attack or not and if any remediation action is required.
- Identify the affected tenant URL (
top5_affected_tenantname) - Identify the list of suspicious IPs and validate whether any login requests were successful from these IPs.
xfe_confirmed_malicious_ips: List of actionable IPs from which SSO, Authentication or management events are found in the last 1 hourxfe_threat_insight: Categories associated with actionable IPs. E.g.: "Found 3 known malicious IPs, having categories: anonsvcs: 0, bots: 3, c2server: 0, mw: 0, scanning: 0."suspicious_ips: List of actionable IPs found in the last hour along with fail %, # of success, and # of failed login events for each IP.
- Identify the severity of the alert:
- Critical: if number of anomalous events are
> max(5*normal_failure_count, 5000) - Warning: if number of anomalous events are between
[min(3* normal traffic volume, 1000), 5000]
- Critical: if number of anomalous events are
top5_affected_data_causegives more information on the cause of failures. This can help in determining if failures are due to any operational issue.- Identify affected usernames (
top5_affected_data_username) which show the top 5 accounts mostly used during the attack. - Identify if any account was accessed successfully (
compromised_users) from suspicious IPs. - Identify the affected application (
top5_affected_data_applicationname). normal_traffic_volumeprovides a baseline count based on the last 7 days of events compared with events in the last 1 hour.anomalous_event_countis the difference between total events in the last 1 hr and normal_traffic_volume.- In some cases, failure logins are generated due to some operational issues. Identify if there are any known issues that could be causing these failures resulting in an alert.
- The following additional fields can be analyzed to get further context for the investigation to debug affected components during the attack or for operational issues
most_significant_data_client_namemost_significant_data_provideridmost_significant_data_redirecturlmost_significant_data_scopemost_significant_data_subtypemost_significant_geoip_country_namemost_significant_servicename
- You can see the number of events for each of the values corresponding to the above attributes in their respective
top5_affected_<FIELD NAME>attribute. - Identify if multiple usernames are used from the IP. If multiple usernames are used, then identify if it's VPN. If the IP address is not VPN, then it could be an attack.
- Based on context from previous steps, determine if it could be a real attack or not.
Some known analysis patterns:
- Identify
xfe_confirmed_malicious_ipslist, if found positive, then block that IP. - Check for the number of Multiple Failed Login alerts generated in that hour then identify
top5_affected_data_cause,top5_affected_data_applicationname, andtop5_affected_data_username.- If the traffic is from a specific application and a specific user, then maybe someone has configured the wrong username/password and ran a script for something. Confirm if it's legitimate traffic or not.
- If the traffic is coming from multiple users: Block the IP (unless it is some VPN/proxy IP address). If the IP is VPN/proxy IP, then identify
top5_affected_data_causeto determine whether it is due to any operational issues. - If multiple Alerts are found in one hour: Identify
top5_affected_tenantnameandtop5_affected_data_usernamefor each alert. If multiple IPs have the most failures for a single tenant and from multiple users, possibly be an attack or major application/system failure.
Possible remediation Actions:
- If unsure about whether it is an attack => Monitor traffic to determine if failures are decreasing or increasing.
- If it is confirmed to be an attack, then block suspicious IP addresses. Refer to block IPs section for more details.
- Accounts that were successfully logged in from suspicious IPs could potentially be compromised. The potentially compromised usernames corresponding to the suspicious IP can be found in
compromised_usersattribute. For compromised accounts, customers can decide the action i.e., if they want to reset passwords or disable these accounts. Refer to block accounts section or prompt for password reset section for more details.
{
"rule_id": "MULTIPLE_FAILED_LOGIN_AUTH",
"rule_name": "Multiple failed login from an IP address (Auth)",
"summary": "Multiple failed login from an IP address (Auth): 5597 anomalous events are observed, beyond normal traffic volume, from 2023-01-10 17:00:00 UTC to 2023-01-10 18:00:00 UTC.",
"source": "[('data.origin', '165.155.173.54'), ('data.result', 'failure')]",
"component": "Login activity",
"anomalous_event_count": 5597,
"normal_traffic_volume": 0,
"start_time": 1673370000000,
"end_time": 1673373600000,
"date": "2023-01-10",
"severity": "critical",
"index": "event-authentication-*",
"impacted_user_count": 17,
"suspicious_ips": "[['ip', 'fail_percentage', 'failure_count', 'success_count'], ['165.155.173.54', 98.45, 5597, 88]]",
"anomalous_suspicious_ips": [
"165.155.173.54"
],
"compromised_users": "{'165.155.173.54': ['serafina', 'alessi', 'donyg', 'evanb', 'joelr', 'taqb', 'anthony', 'heaven', 'jenny', 'jessica']}",
"xfe_threat_insight": "Found 0 known malicious IPs.",
"xfe_confirmed_malicious_ips": [],
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 5597}",
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_tenantname": "{'tenant1.abc.com': 5593, 'tenant2.abc.com': 4}",
"most_significant_tenantname": [
"idpcloud.nycenet.edu"
],
"top5_affected_data_subtype": "{'user_password': 5596, 'mfa': 1}",
"most_significant_data_subtype": [
"user_password"
],
"top5_affected_data_scope": "{}",
"most_significant_data_scope": [],
"top5_affected_data_cause": "{'The system failed to authenticate user \"aariz\" because of \"INVALID_CREDS\".': 5579,
'The system failed to authenticate user \"anthony\" because of \"INVALID_CREDS\".': 2,
'The system failed to authenticate user \"mtorr\" because of \"INVALID_CREDS\".': 2,
'CSIAH2417E The one-time password that you submitted was invalid. Submit a valid one-time password.': 1,
'The system failed to authenticate user \"aless\" because of \"INVALID_CREDS\".': 1}",
"most_significant_data_cause": [
"The system failed to authenticate user \"aari\" because of \"INVALID_CREDS\"."
],
"top5_affected_data_sourcetype": "{'clouddirectory': 5596}",
"most_significant_data_sourcetype": [
"clouddirectory"
],
"top5_affected_servicename": "{'profilemgmt': 5596, 'authsvc': 1}",
"most_significant_servicename": [
"profilemgmt"
],
"top5_affected_data_providerid": "{}",
"most_significant_data_providerid": [],
"top5_affected_data_grant_type": "{}",
"most_significant_data_grant_type": [],
"top5_affected_data_mfamethod": "{'SMS OTP': 1}",
"most_significant_data_mfamethod": [
"SMS OTP"
],
"top5_affected_data_username": "{'aari': 5579, 'anthony': 2, 'mtor': 2, 'ANor': 1, 'aless': 1}",
"most_significant_data_username": [
"aari"
],
"top5_affected_geoip_country_name": "{'United States': 5597}",
"most_significant_geoip_country_name": [
"United States"
]
}
Alert Name: Abnormal number of failed SSO/Authentication events observed per tenant.
Indicates: Brute force or Credential stuffing attack or Operational issues
Details: Sudden increase in failed logins for a tenant as compared to normal behavior for SSO or Auth events in the last 14 days.
Investigation Steps: Analyze traffic to understand if it could be a real attack or not and if any remediation action is required.
- Identify affected tenant URLs (
top5_affected_tenantname). - Identify the list of suspicious IPs and validate whether any login requests were successful from these IPs.
xfe_confirmed_malicious_ips: List of actionable IPs from which SSO, Authentication or management events are found in the last 1 hourxfe_threat_insight: Categories associated with actionable IPs. E.g.: "Found 3 known malicious IPs, having categories: anonsvcs: 0, bots: 3, c2server: 0, mw: 0, scanning: 0."suspicious_ips: List of actionable IPs found in the last hour along with fail %, # of success, and # of failed login events for each IP.
- Identify the severity of the alert:
- Critical: if number of anomalous events are
> max(5*normal_failure_count, 10000) - Warning: if number of anomalous events are between
[min(3* normal traffic volume, 5000), 10000]
- Critical: if number of anomalous events are
top5_affected_data_causegives more information on the cause of failures. This can help to determine if failures are due to operational issues.- Identify the affected usernames (
top5_affected_data_username) which show the top 5 accounts most frequently used during the attack. - Identify the affected application (
top5_affected_data_applicationname). normal_traffic_volumeprovides a baseline count based on the last 14 days of events compared with events in the last 1 hour.anomalous_event_countis the difference between total events in the last 1 hr and normal_traffic_volume.- In some cases, failure login events are generated due to some operational issues.
- Identify if there is any known issue that could be causing these failures resulting in an alert.
- Identify if there are any other alerts generated indicating an attack such as Multiple failed login attempts from IP Address (or) Potential credential stuffing attack
- The following additional fields can be analyzed to get additional context for the investigation to debug affected components during the attack or for operational issues
most_significant_data_client_namemost_significant_data_provideridmost_significant_data_redirecturlmost_significant_data_scopemost_significant_data_subtypemost_significant_geoip_country_namemost_significant_servicename
- You can see the number of events for each of the values corresponding to the above attributes in their respective
top5_affected_<FIELD NAME>attribute. - Based on context from previous steps, determine if it could be due to an attack or operational issue.
Possible remediation Actions:
- If unsure about whether it is an attack => Monitor traffic to determine if failures are decreasing or increasing.
- If it is confirmed to be an attack, then block the IP addresses mentioned in the
anomalous_suspicious_ipsattribute. Refer to the block IPs section for more details. - Accounts that were successfully logged in from suspicious IPs could potentially be compromised. The potentially compromised usernames corresponding to the suspicious IP can be found in the
compromised_usersattribute. For compromised accounts, customers can decide the action i.e., if they want to reset passwords or disable these accounts. Refer to the block accounts section or prompt for password reset section for more details.
{
"rule_id": "TENANT_FAILED_SSO_EVENTS",
"rule_name": "Abnormal number of failed SSO events observed per tenant.",
"summary": "Abnormal number of failed SSO events observed per tenant.: 24456 anomalous events are observed, beyond normal traffic volume, from 2022-12-19 10:00:00 UTC to 2022-12-19 11:00:00 UTC.",
"source": "[('tenantid', '874f131f-79a9-4581-b078-de7681091fbc'), ('tenantname', 'tenant1.abc.com'), ('data.result', 'failure')]",
"component": "Login activity",
"anomalous_event_count": 24456,
"normal_traffic_volume": 711,
"start_time": 1671444000000,
"end_time": 1671447600000,
"date": "2022-12-19",
"severity": "critical",
"index": "event-sso-*",
"impacted_user_count": 88,
"impacted_apps_count": 37,
"suspicious_ips": "[['ip', 'fail_percentage', 'failure_count', 'success_count'],
['177.241.73.204', 100.0, 24777, 0], ['129.42.21.2', 100.0, 26, 0], ['129.42.18.2', 100.0, 24, 0],
['129.42.19.2', 100.0, 24, 0], ['89.64.54.76', 100.0, 19, 0], ['52.116.134.146', 100.0, 12, 0],
['122.161.79.4', 100.0, 11, 0]]",
"anomalous_suspicious_ips": [
"122.161.79.4",
"177.241.73.204",
"89.64.54.76"
],
"xfe_threat_insight": "Found 1 known malicious IPs, having categories: anonsvcs: 0, bots: 1, c2server: 0, mw: 0, scanning: 0`",
"xfe_confirmed_malicious_ips": ['122.161.79.4'],
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 25167}",
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_tenantname": "{'tenant1.abc.com': 25167}",
"most_significant_tenantname": [
"tenant1.abc.com"
],
"top5_affected_servicename": "{'oidc_rt': 25167}",
"most_significant_servicename": [
"oidc_rt"
],
"top5_affected_data_subtype": "{'oidc': 25167}",
"most_significant_data_subtype": [
"oidc"
],
"top5_affected_data_scope": "{'openid email': 24790, 'openid': 259, 'openid profile': 2, 'openid profile email': 1}",
"most_significant_data_scope": [
"openid email"
],
"top5_affected_data_cause": "{'CSIAQ0178E Login is required. The request cannot be processed without authentication.': 24777,
'CSIAQ0278E User is not authorized to access the application due to policy constraints.': 150,
'CSIAQ0158E The [authorization_grant] of type [authorization_code] does not exist or is invalid.': 70,
'CSIAQ0158E The [authorization_grant] of type [refresh_token] does not exist or is invalid.': 31,
'CSIAQ0158E タイプ [refresh_token] の [authorization_grant] は存在しないか無効です。': 13}",
"most_significant_data_cause": [
"CSIAQ0178E Login is required. The request cannot be processed without authentication."
],
"top5_affected_data_applicationname": "{'Gaz-HAT-Production': 24777, 'abc-refresh-service-prod': 107, 'ABCProductionOIDC': 72, 'ABC Publisher': 63, 'FastPassPRDClient': 30}",
"most_significant_data_applicationname": [
"Gaz-HAT-Production"
],
"top5_affected_data_client_name": "{'ABC-HAT-Production': 24777, 'ABCrefresh-service-prod': 107, 'ABCProductionOIDC': 72, 'abc Publisher': 63, 'abcFastPassPRDClient': 30}",
"most_significant_data_client_name": [
"Gaz-HAT-Production"
],
"top5_affected_data_redirecturl": "{'https://gaz.tuc.stglabs.ibm.com/oidc/callback/': 24777, 'https://w3-authorization-service.us-south-k8s.intranet.ibm.com/sso/callback': 88, 'https://w3.ibm.com/w3publisher/redirect.html': 63, 'UNKNOWN': 50, 'https://fastpass.w3cloud.ibm.com:443/oidcclient/redirect/FastPassPRDClient': 30}",
"most_significant_data_redirecturl": [
"https://gaz.tuc.stglabs.ibm.com/oidc/callback/"
],
"top5_affected_data_providerid": "{}",
"most_significant_data_providerid": [],
"top5_affected_data_username": "{'UNKNOWN': 24978, '[email protected]': 19, '[email protected]': 17, '[email protected]': 11, '[email protected]': 10}",
"most_significant_data_username": [
"UNKNOWN"
],
"top5_affected_geoip_country_name": "{'Mexico': 24777, 'United States': 192, 'India': 84, 'Poland': 26, 'Japan': 22}",
"most_significant_geoip_country_name": [
"Mexico"
]
}
Alert Name: Frequent authentication from a single user
Indicates: Brute force attack or Operational issues
Details: Sudden increase in successful authentication requests from a single user as compared to normal behavior for SSO or Auth events in the last 7 days.
Investigation Steps: Analyze traffic to understand if it could be a real attack or not and if any remediation action is required.
- Identify the affected tenant URL (
top5_affected_tenantname). - Identify the severity of the alert:
- Critical: if number of anomalous events are
> max(5*normal_failure_count, 10000) - Warning: if number of anomalous events are between
[min(3* normal traffic volume, 5000), 10000].
- Critical: if number of anomalous events are
- Identify the affected usernames (
top5_affected_data_username) to assess accounts used from IP addresses. - Identify the affected application (
top5_affected_data_applicationname). normal_traffic_volumeprovides a baseline count based on the last 7 days of events compared with events in the last 1 hour.anomalous_event_countis the difference between total events in the last 1 hr and normal_traffic_volume.- In some cases, frequent authentication could be due to the misconfiguration of the app. Identify if there is any known issue that could be causing these failures resulting in an alert.
- The following additional fields can be analyzed to get further context for the investigation to debug affected components during the attack or for operational issues.
most_significant_data_client_namemost_significant_data_provideridmost_significant_data_redirecturlmost_significant_data_scopemost_significant_data_subtypemost_significant_geoip_country_namemost_significant_servicename
- You can see the number of events for each of the values corresponding to the above attributes in their respective
top5_affected_<FIELD NAME>attribute. - Based on context from previous steps, determine if it could be suspicious traffic.
Some known analysis patterns:
- Identify if multiple alerts are coming in the same interval for a single tenant. If yes, then check for any known operational issue for the tenant, otherwise look at the
top5_affected_data_applicationnameattribute to identify the application responsible for generating the alert. - If the alert is being generated from the same source (i.e., same tenant URL and username) for multiple hours, the user can be blocked for some duration (eg: 24 hrs).
- Look for IP address and application-name distribution to identify if it's a distributed attack.
Possible remediation Actions:
- If unsure of suspicious traffic => Monitor traffic to determine if failures are decreasing or increasing.
- If traffic is identified as suspicious, then block the account for which the alert is generated as proactive remediation. Refer to the block accounts section for more details.
{
"rule_id": "FREQUENT_AUTH_SINGLEUSER_AUTH",
"rule_name": "Frequent authentication from single user (Auth)",
"summary": "Frequent authentication from single user (Auth): 16283 anomalous events are observed, beyond normal traffic volume, from 2022-12-26 10:00:00 UTC to 2022-12-26 11:00:00 UTC.",
"source": "[('tenantid', '874f131f-79a9-4581-b078-de7681091fbc'), ('data.username', 'MSurk'), ('data.result', 'success')]",
"component": "Login activity",
"anomalous_event_count": 16283,
"normal_traffic_volume": 0,
"start_time": 1672048800000,
"end_time": 1672052400000,
"date": "2022-12-26",
"severity": "critical",
"index": "event-authentication-*",
"impacted_user_count": 1,
"anomalous_suspicious_ips": [
"12.153.148.57"
],
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 16283}",
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_tenantname": "{'tenant1.abc.com': 16283}",
"most_significant_tenantname": [
"tenant1.abc.com"
],
"top5_affected_data_cause": "{'Authenticated user \"MSurk\" successfully.': 16283}",
"most_significant_data_cause": [
"Authenticated user \"MSurk\" successfully."
],
"top5_affected_data_subtype": "{'user_password': 16283}",
"most_significant_data_subtype": [
"user_password"
],
"top5_affected_data_scope": "{}",
"most_significant_data_scope": [],
"top5_affected_data_sourcetype": "{'clouddirectory': 16283}",
"most_significant_data_sourcetype": [
"clouddirectory"
],
"top5_affected_servicename": "{'profilemgmt': 16283}",
"most_significant_servicename": [
"profilemgmt"
],
"top5_affected_data_origin": "{'12.153.148.57': 16283}",
"most_significant_data_origin": [
"12.153.148.57"
],
"top5_affected_data_providerid": "{}",
"most_significant_data_providerid": [],
"top5_affected_data_grant_type": "{}",
"most_significant_data_grant_type": [],
"top5_affected_data_mfamethod": "{}",
"most_significant_data_mfamethod": [],
"top5_affected_data_username": "{'MSurk': 16283}",
"most_significant_data_username": [
"MSurk"
],
"top5_affected_geoip_country_name": "{'United States': 16283}",
"most_significant_geoip_country_name": [
"United States"
]
}
Alert Name: Abnormal number of MFA device enrollements
Indicates: Brute force attack
Details: Sudden increase in MFA devices from a single user as compared to normal behavior in the last 7 days.
Investigation Steps: Analyze traffic to understand if it could be a real attack or not and if any remediation action is required.
- Identify the affected tenant URL (
top5_affected_tenantname). - Identify the severity of the alert:
- Critical: if number of anomalous events are
> 18. - Warning: if number of anomalous events are
> 10.
- Critical: if number of anomalous events are
- Identify the most used mfamethod (
top5_affected_data_mfamethod) in the last 1 hour. normal_traffic_volumeprovides a baseline count based on the last 7 days of events compared with events in the last 1 hour.anomalous_event_countis the difference between total events in the last 1 hr and normal_traffic_volume.- Based on context from previous steps, determine if it could be suspicious traffic.
Some known analysis patterns:
This alert is generated on management events. If any alert is found then, then look whether it is from a valid user or not. If the user is valid, then identify the type of authentication (top5_affected_data_mfamethod) and the number of devices being enrolled (anomalous_event_count). Take action if found suspicious.
Possible remediation Actions:
- If unsure of suspicious traffic => Monitor traffic to determine if failures are decreasing or increasing.
- If traffic is identified as suspicious, then block the account for which the alert is generated as proactive remediation. Refer to the block accounts section for more details.
{
"rule_name": "Abnormal number of device enrollments",
"rule_id": "ABNORMAL_DEVICE_ENROLLMENT",
"summary": "Abnormal number of device enrollments: 20 anomalous events are observed, beyond normal traffic volume, from 2023-01-12 17:00:00 UTC to 2023-01-12 18:00:00 UTC.",
"severity": "critical",
"date": "2023-01-12",
"start_time": "2023-01-12 17:00:00",
"end_time": "2023-01-12 18:00:00",
"component": "Login activity",
"normal_traffic_volume": 0,
"anomalous_event_count": 20,
"impacted_user_count": 1,
"index": "event-management-*",
"most_significant_data_origin": [
"129.41.58.3"
],
"top5_affected_data_username": "{'Henry': 20}",
"source": "[('data.mfamethod', 'Voice OTP'), ('data.username', 'Henry')]",
"top5_affected_servicename": "{'factors': 20}",
"most_significant_data_mfamethod": [
"Voice OTP"
],
"most_significant_geoip_country_name": [
"United States"
],
"most_significant_data_grant_type": [],
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 20}",
"top5_affected_tenantname": "{'tenant1.abc.com': 20}",
"most_significant_servicename": [
"factors"
],
"most_significant_tenantname": [
"tenant1.abc.com"
],
"top5_affected_data_origin": "{'129.41.58.3': 20}",
"anomalous_suspicious_ips": [
"129.41.58.3"
],
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_geoip_country_name": "{'United States': 20}",
"top5_affected_data_grant_type": "{}",
"top5_affected_data_mfamethod": "{'Voice OTP': 20}",
"most_significant_data_username": [
"Henry"
]
}
Alert Name: Multiple use of compromised credentials
Indicates: Account takeover, brute force, credential stuffing
Details: Sudden increase in the use of compromised credentials for authentication requests from an IP as compared to it's normal behavior for Auth events in the last 7 days. A large set of compromised credentials are stored in Verify's GLOBAL Dictionary, which customers can configure in their tenant for additional protection against reuse of compromised credentials.
Investigation Steps: Analyze traffic to understand if it could be a real attack or not and if any remediation action is required.
- Identify the affected tenant URL (
top5_affected_tenantname). - Identify the severity of the alert:
- Critical: if number of anomalous events are
> 50 - Warning: if number of anomalous events are between
[8, 50].
- Critical: if number of anomalous events are
- Identify the IP address trying to use the compromised credentials in
sourceattribute. - Identify the affected usernames (
top5_affected_data_username) to assess accounts used from IP addresses. normal_traffic_volumeprovides a baseline count based on the last 7 days of events compared with events in the last 1 hour.anomalous_event_countis the difference between total events in the last 1 hr and normal_traffic_volume.- The following additional fields can be analyzed to get further context for the investigation to debug affected components during the attack or for operational issues.
most_significant_data_sourcetypemost_significant_data_provideridmost_significant_data_scopemost_significant_data_subtypemost_significant_geoip_country_namemost_significant_servicename
- You can see the number of events for each of the values corresponding to the above attributes in their respective
top5_affected_<FIELD NAME>attribute. - Based on context from previous steps, determine if it could be suspicious traffic.
Some known analysis patterns:
- Identify whther the IP is trying to access multiple users using the compromised credentials form
top5_affected_data_usernameattribute. If yes, then the IP can be blocked for some duration. - If multiple alerts were found from multiple IPs in an hour or same IP was detected by
Multiple_failed_loginrule orcredential_stuffingrule, may be an brute force attack or credential stuffing attack is going on.
Possible remediation Actions:
- If unsure of suspicious traffic => Monitor traffic to determine if compromised password usage is decreasing or increasing.
- If some user accounts were successfully accessed during the attack duration from the same IP, log out the user from all active sessions and prompt for password change or temporarily block user as proactive remediation. Refer to the block accounts section for more details.
- If multiple users are getting accessed from the IP with compromised credentials, block the IP in the
sourceattribute. Refer to block IPs section for more details.
{
"rule_id": "COMPROMISED_CREDENTIALS",
"rule_name": "Multiple use of compromised credentials",
"summary": "Multiple use of compromised credentials: 100 anomalous events are observed, beyond normal traffic volume, from 2023-02-08 21:00:00 UTC to 2023-02-08 22:00:00 UTC.",
"source": "[('data.origin', '129.41.58.3'), ('data.dict_type', 'GLOBAL')]",
"component": "Login activity",
"severity": "critical",
"impacted_user_count": 1,
"anomalous_event_count": 100,
"normal_traffic_volume": 0,
"date": "2023-02-08",
"top5_affected_data_scope": "{}",
"rule_attribute": "compromised_credentials",
"top5_affected_data_username": "{'Henry': 100}",
"start_time": "2023-02-08 21:00:00",
"end_time": "2023-02-08 22:00:00",
"index": "event-authentication-*",
"top5_affected_servicename": "{'profilemgmt': 100}",
"most_significant_data_mfamethod": [],
"most_significant_geoip_country_name": [
"United States"
],
"most_significant_data_grant_type": [],
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 100}",
"top5_affected_tenantname": "{'tenant1.abc.com': 100}",
"top5_affected_data_providerid": "{}",
"most_significant_servicename": [
"profilemgmt"
],
"most_significant_tenantname": [
"tenant1.abc.com"
],
"most_significant_data_sourcetype": [
"clouddirectory"
],
"most_significant_data_scope": [],
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_data_subtype": "{'user_password': 100}",
"most_significant_data_subtype": [
"user_password"
],
"most_significant_data_providerid": [],
"top5_affected_geoip_country_name": "{'United States': 100}",
"top5_affected_data_grant_type": "{}",
"top5_affected_data_mfamethod": "{}",
"top5_affected_data_sourcetype": "{'clouddirectory': 100}",
"most_significant_data_username": [
"Henry"
]
}
Alert Name: Grouping by cause of failure
Indicates: Operational issues
Details: Sudden increase in failure events having a specific cause compared to normal behavior in the last 7 days. The causes are unrelated to username/password failure.
Investigation Steps: Analyze traffic to understand if it could be a real attack or not and if any remediation action is required.
- Identify the affected tenant URL (
top5_affected_tenantname). - Identify the severity of the alert:
- Critical: if number of anomalous events are
> max(5*normal_failure_count, 10000). - Warning: if number of anomalous events are
> [min(3* normal traffic volume, 5000), 10000].
- Critical: if number of anomalous events are
- Identify affected usernames (
top5_affected_data_username). - Identify the affected application (
top5_affected_data_applicationname). normal_traffic_volumeprovides a baseline count based on the last 7 days of events compared with events in the last 1 hour.anomalous_event_countis the difference between total events in the last 1 hr and normal_traffic_volume.- The following additional fields can be analyzed to get further context for the investigation. Below attributes can help debug the affected components during the operational issues
most_significant_data_client_namemost_significant_data_provideridmost_significant_data_redirecturlmost_significant_data_scopemost_significant_data_subtypemost_significant_geoip_country_namemost_significant_servicename
- You can see the number of events for each of the values corresponding to the above attributes in their respective
top5_affected_<FIELD NAME>attribute. - This alert is primarily for operational issues. Identify the affected application and type of issue from
top5_affected_data_applicationnameand thesummaryattributes.
Possible remediation Actions:
Based on the operational issue, it might require configuration changes on the Verify admin console or the help of Verify Support team.
{
"rule_id": "CAUSE_OF_SSO_FAILURE",
"rule_name": "Grouping by the cause of failure (SSO)",
"summary": "Grouping by the cause of failure (SSO): 11314 anomalous events are observed, beyond normal traffic volume, from 2023-01-18 15:00:00 UTC to 2023-01-18 16:00:00 UTC.",
"source": "[('data.cause', 'CSIAC5061E An unexpected error has occurred with a protocol module com.tivoli.am.fim.fedmgr2.protocol.GenericPocAuthenticationDelegateProtocol.'), ('data.result', 'failure')]",
"component": "Login activity",
"anomalous_event_count": 11314,
"normal_traffic_volume": 1595,
"start_time": 1674054000000,
"end_time": 1674057600000,
"date": "2023-01-18",
"severity": "critical",
"index": "event-sso-*",
"impacted_user_count": 7774,
"impacted_apps_count": 20,
"top5_affected_tenantid": "{'874f131f-79a9-4581-b078-de7681091fbc': 12909}",
"most_significant_tenantid": [
"874f131f-79a9-4581-b078-de7681091fbc"
],
"top5_affected_tenantname": "{'tenant1.abc.com': 11057, 'tenant2.abc.com': 1852}",
"most_significant_tenantname": [
"tenant1.abc.com"
],
"top5_affected_servicename": "{'saml_runtime': 12909}",
"most_significant_servicename": [
"saml_runtime"
],
"top5_affected_data_subtype": "{'saml': 12420, 'WS-Fed': 489}",
"most_significant_data_subtype": [
"saml"
],
"top5_affected_data_scope": "{}",
"most_significant_data_scope": [],
"top5_affected_data_cause": "{'CSIAC5061E An unexpected error has occurred with a protocol module com.tivoli.am.fim.fedmgr2.protocol.GenericPocAuthenticationDelegateProtocol.': 12909}",
"most_significant_data_cause": [
"CSIAC5061E An unexpected error has occurred with a protocol module com.tivoli.am.fim.fedmgr2.protocol.GenericPocAuthenticationDelegateProtocol."
],
"top5_affected_data_applicationname": "{'ABC-365': 320, 'Google.com': 67}",
"most_significant_data_applicationname": [
"ABC-365"
],
"top5_affected_data_client_name": "{}",
"most_significant_data_client_name": [],
"top5_affected_data_redirecturl": "{}",
"most_significant_data_redirecturl": [],
"top5_affected_data_providerid": "{'UNKNOWN': 12472, 'urn:federation:MicrosoftOnline': 323}",
"most_significant_data_providerid": [
"UNKNOWN"
],
"top5_affected_data_username": "{'UNKNOWN': 86, '[email protected]': 60, '[email protected]': 31, 'julia': 20, 'Bryan': 11}",
"most_significant_data_username": [
"UNKNOWN",
"[email protected]",
"[email protected]"
],
"top5_affected_geoip_country_name": "{'United States': 12295, 'India': 178, 'Canada': 84, 'United Kingdom': 72, 'Mexico': 36}",
"most_significant_geoip_country_name": [
"United States"
]
}
Correlation between multiple alerts:
This section provides guidance on investigation and proactive remediations when more than one alert is generated.
| Correlation of Alerts | Indicator of | Remediation Action in Verify | Investigation |
|---|---|---|---|
| Potential credential stuffing + Multiple failed login | Credential stuffing | Block the IPs in Verify | Follow potential credential stuffing attack investigation |
| Abnormal number of failed + Multiple failed Login | Operational issue caused by some selected machines | Inform the customer about the Ips and users related to those IP. | Look at the cause of failure and user distribution per IP. |
| (Potential credential stuffing/Multiple failed login) + Abnormal device enrolments | Account takeover | Block the compromised user(s) | |
| (Potential credential stuffing + Multiple failed login / Abnormal number of failed) + Compromised credentials | Password Spraying | Block the Ips and prompt the compromised users to change password |
Remediations Steps
Block Users or Accounts
You can block users either through the UI or using an API. See Updating User Details to disable a user via the UI, and Modify User API to update a specific user's "active" status as "false" using the API.
Block IP Addresses
Add an IP condition to access policies where feasible. You may also open a ticket with IBM support with information about the IP addresses to be blocked.
Reset Password
To reset the password of a cloud directory user, use the reset password API. If the user is a federated user, reset the password at the source (e.g. Active Directory).
Priti Patil, Nagesh Bhagwat & M Krishnakant Achary, IBM Security
Updated 7 months ago
