Exchange access token for web session
Introduction
OpenID Connect provides a ton of options for authenticating users and devices: from the normal Authorization Code grants, to Client Credentials, to ROPC, and many more. However, in some cases, you are limited with what you can do once you've authenticated. In an Authorization Code grant flow, your session at the identity provider side may have expired but your access tokens may still be valid. In an ROPC grant flow, you have obtained rights to interact with the identity provider, but you never established a session with the browser so if you attempted to go elsewhere, you'd be out of luck.
In this scenario, we will use the ROPC grant flow with IBM Verify to obtain an access token, and then make an ajax based HTTP call with that token and obtain an established authenticated session with IBM Verify. Once the session has been established, users are able to traverse other applications, both SAML and OIDC, without re-authenticating directly with the identity provider.
Note: For the time being, CORS bypass needs to be enabled via a browser plugin. I'm working on a workaround at the moment.
New authentication session endpoint
In IBM Verify, there is an API endpoint that allows for session cookies to be set when called from within a browser:
GET /v1.0/auth/session
When calling this API, a valid access token must be provided in the Authorization HTTP header:
'Authorization: bearer {access_token}'
A web session is created for the user identified by the access token and a cookie to maintain that session in the browser is returned.
This new API is pretty simple to call using an ajax call. In the code sample below, I've created a JavaScript function, providing the access token I received, and upon a successful response from the API call, I send the user to the launchpad (which is in of itself an OIDC application) and I wont be asked for any further authentication (unless multi-factor authentication is required by your security policy).
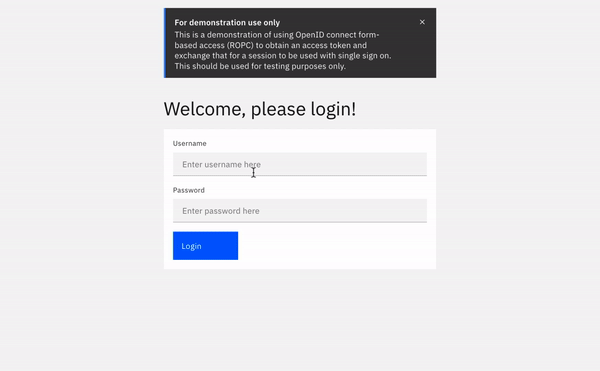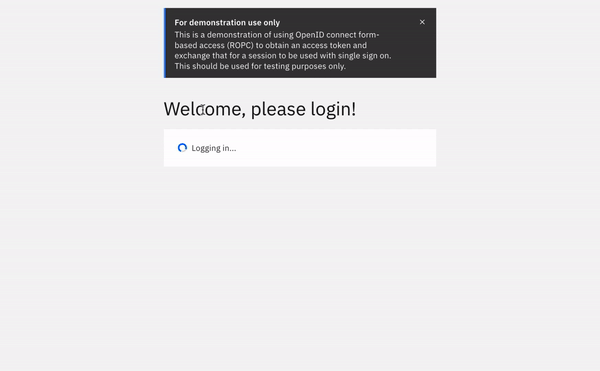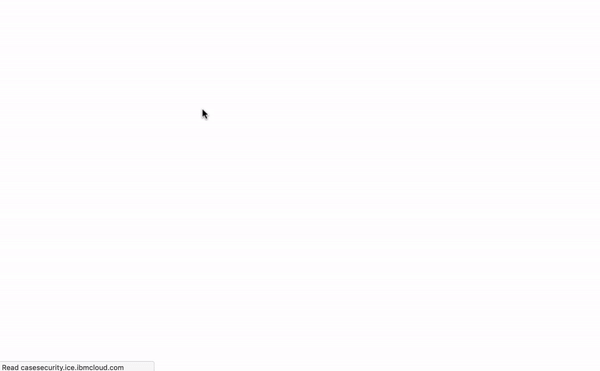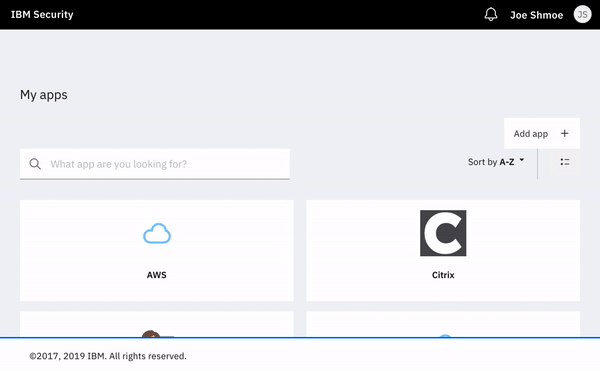
Sample form-based login flow example
I have put together a sample application, no more than 160 lines of HTML/JS code. This application does one thing, and one thing only: logs a user in to the launchpad from an third party application.
Pre-requisites
Create a new OIDC application for ROPC
Create a new custom application in IBM Verify and select OpenID Connect as the type. Enable Resource Owner Password Credential (ROPC) grant, with a public client ID, and no secret. For this flow, the secret does not really do us much good because this is just a front-end based application. It wouldn't really be private anyway as there isn't a real good option to hide it.
Add your domain to allowed domains in IBM Verify
This application is a third party site, so you will need to add your server URL, whether localhost or a fully-qualified domain, to your Allowed Domains.
In the admin portal of IBM Verify, navigate to the Configuration tab. Under the API Clients tab, select Allowed Domains. Add your domain, port, and anything else necessary to allow CORS. In this case, I am using python to create a HTTP server on port 8000. I've added http://localhost:8000 to my list of allowed domains.
Sample code
Updated 7 months ago
