MaaS360 as an identity source
Introduction
IBM MaaS360 comes bundled with IBM Verify to provide zero-trust architectures from a single vendor. This integrated solution is ready for you to take advantage of seamless single sign-on (SSO) and conditional access to corporate resources from mobile devices and desktops.
IBM Verify works with existing identity providers such as ADFS, ISAM, or Azure AD. Verify can still manage all your cloud apps’ single sign-on requests leveraging your existing Identity Provider without any additional infrastructure required. In fact, you can use the Verify bridge or an existing MaaS360 Cloud Extender to replace your existing Identity Provider infrastructure.
MaaS360 administrators can enable Verify under the Identity and Access Management service in the MaaS360 portal and give it a try. It is that simple. When you enable the MaaS360 Identity and Access Management service, a full featured IBM Verify tenant is configured for you within minutes and you can begin configuring cloud resources for SSO and conditional access.
In this guide we’ll discuss the value Maas360 and Verify integration provides, review the architecture, and walk you through the high level configuration steps to get you started with seamless SSO and conditional access to SaaS apps from your mobile devices.
How it works
The objective of MaaS360 Identity and Access Management is to provide seamless SSO on and conditional access control for mobile devices to third party cloud apps using the integration of Maas360 and Verify. The diagram below is a high level overview of the integration and data authentication flows after the configuration is completed for one of your cloud apps.
When mobile users open a mobile app on their device, the request is sent to the cloud app, for example, Box. The cloud app recognizes the user’s domain as one that is using Verify and then redirects the authentication request to Verify. The Verify authentication service challenges the device for authentication and the device presents an identity certificate that MaaS360 provisioned to the device when it was enrolled. Verify recognizes the certificate and checks if the device is compliant per corporate policies in MaaS360. After all the checks are passed, Verify issues a SAML token to the mobile app which in turn presents it to the third party cloud app, in this example Box. The user is successfully authenticated, and the app opens.
When you enable Identity and Access Management in the MaaS360 portal, you configure a Verify tenant automatically. After the configuration, your Verify tenant and Maas360 tenant exchange information and a regular synchronization begins where user and compliance information are exchanged. This is what allows Verify to serve as the Identity Provider for mobile apps that are pushed from MaaS360 to the devices.
Pre-defined Connectors
Verify has 1000s of predefined connectors for cloud apps. The administrator configures the connectors for the cloud apps that will be accessed by the MaaS360 enrolled devices. The connectors enable the federated SSO using SAML, where Verify is the Identity Provider and cloud apps such as Box and Salesforce are the Service providers. When you configure an app in Verify, you identify what type of devices can access it and the kind of access. For example, you can specify that only managed mobile devices that are compliant can access the app. You can also choose multi factor authentication using IBM Verify.
SSO using Identity Certificates
When a device enrolls with Maas360, an identity certificate is provisioned to the device. The identity certificate is used to authenticate the user and allows for the seamless SSO experience. The certificate is unique to the user and the device. SSO fails if the certificate is used on another device. The identity certificate is what is used to authenticate with Verify, so the mobile user does not need to enter credentials, except maybe an email address. MaaS360 uses its own Verify to provision the identity certificate, so you do not need a PKI. All certificate revocation and renewals are handled by MaaS360.
SSO Payload and Compliance
MaaS360 also governs access to the cloud apps based on compliance with mobile device management policies that are applied to the device. When the device enrolls in MaaS360, the MDM policy provisions an SSO payload to each device. The SSO payload has information on the SSO cloud apps the user can use. MaaS360 regularly checks compliance on the device. You can configure Compliance Rules in the MaaS360 portal, for example, to make sure the device is at a specific OS level. If the device is not, it will be marked out of compliance and that information will also be made available to Verify.
Wandera customers take note
If you are a Wandera customer and have integrated their service into Verify for compliance, then you can use the Wandera threat level to trigger an out of compliance event so that in certain situations the user cannot log into sensitive applications. When the user attempts to access a mobile app, Verify will not grant access based on the out of compliance state if you have enabled that level of conditional access.
Pre-requisites
The purpose of this configuration guide is to provide a high level of understanding of what is involved in the set up. Before you begin configuring, you should understand what your Identity source is. You must identify an Identity source in Verify. If you are using Local Users and Groups in MaaS360, then you do not need to configure a new Identity Source. Cloud directory (local users and groups) is the default.
Using Cloud Extender for User Authentication with an On-Premise directory service?
Identity Source: MaaS360 Cloud Extender (or LDAP Pass-through)
Using an enterprise Identity source such as Azure AD, ISAM, or ADFS?
Identity Source: SAML Enterprise
Enable the Verify service in MaaS360
- In the MaaS360 portal, select SETUP > Services and find Identity and Access Management service.
- Enable it and click Configure.
- You need an IBM ID to configure the Verify service.
- Enter a hostname to register for your Verify tenant
- Note: Usually this is your company name (ex. company for company.verify.ibm.com)
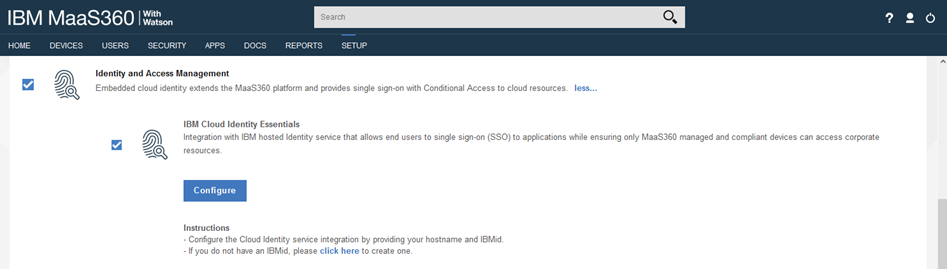
Note: If you support Windows 10 devices then you will see an additional checkbox for laptop conditional access. Only enable the laptop access if you want to use conditional access for Windows 10.
Launch Verify and set the default Identity Source
After your Verify tenant is created, you can launch it from the Identity and Access Management service selection in MaaS360.
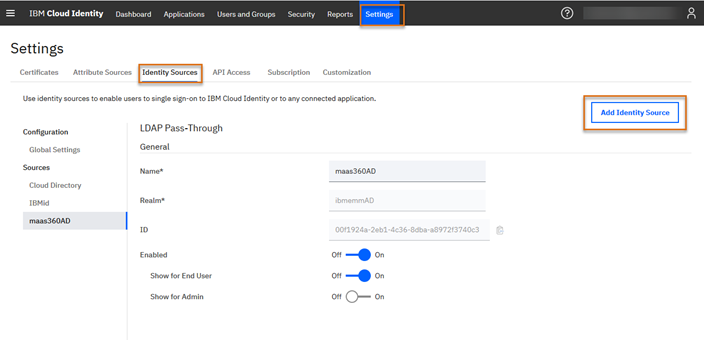
In this step, you must define the Identity Source you plan to use for authentication. If you are using local users and groups, Cloud Directory is already set up and is the default. In this example, Cloud Extender with Active Directory User Authentication is being used in the MaaS360 portal. Therefore, we create an LDAP Passthrough Identity Source.
In the Verify portal, click Add Identity Source.
Type a Name and a realm. Name is the name that you assign to represent the user registry that is used by identity providers such as Microsoft Active Directory, Microsoft Azure Active Directory, or others. Realm is an identity source attribute that helps distinguish users from multiple identity sources that have the same user name. In both cases, you can enter whatever value you want in these two fields but make them meaningful to your environment.
Enable the new Identity Source by setting Enabled to On. When the identity source is configured and enabled, users can single sign-on to Verify and into their entitled applications with the selected identity source. Set Show for End User to On for all end users sign in page. You can also enable it for Administrators if you want them to use LDAP Passthrough for authentication. Note that the sign in page is only displayed to the mobile user if the certificate authentication fails.
When you save the new Identity Source, a unique ID is generated and the new Identity Source displays in the list of Sources. Disable the other Identity Sources that you will not be using.
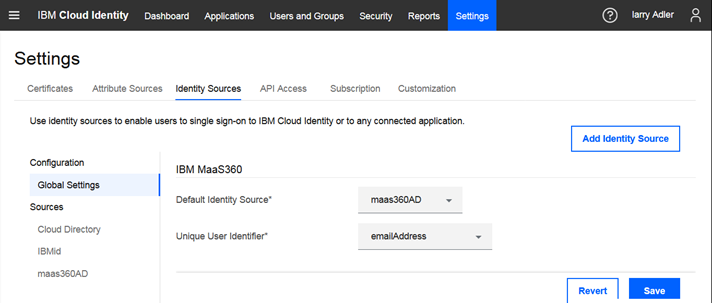
Next, go to Global Settings and select your new Identity Source in the Default Identity Source field and select a unique user identifier. The unique user identifier is used to identify IBM MaaS360 users who access Verify.
Configure Verify for 3rd party applications
Configure the cloud apps that your mobile users will be accessing from their mobile device. If you want your MaaS360 mobile users to have seamless SSO and to control access based on their MaaS360 compliance status, for example: Salesforce and Box, you must select these predefined connectors in Verify and configure them for federated SAML authentication. When the mobile user accesses the app from their device, the authentication request goes to the cloud app, such as Salesforce, and Salesforce redirects the request to Verify. The connector configuration enables that redirection and authentication to happen. Each connector has detailed configuration steps that you follow.
If certificate authentication fails, the user will be redirected to their identity source to enter their user name and password (access to the application depends on your access policy). If certificate authentication succeeds, the user will automatically be authenticated and will not be shown a user and password log in screen.
When you select an application, you are also provided with a risk score and details from IBM X-Force Exchange. You can also link to X-Force Exchange for risk details.
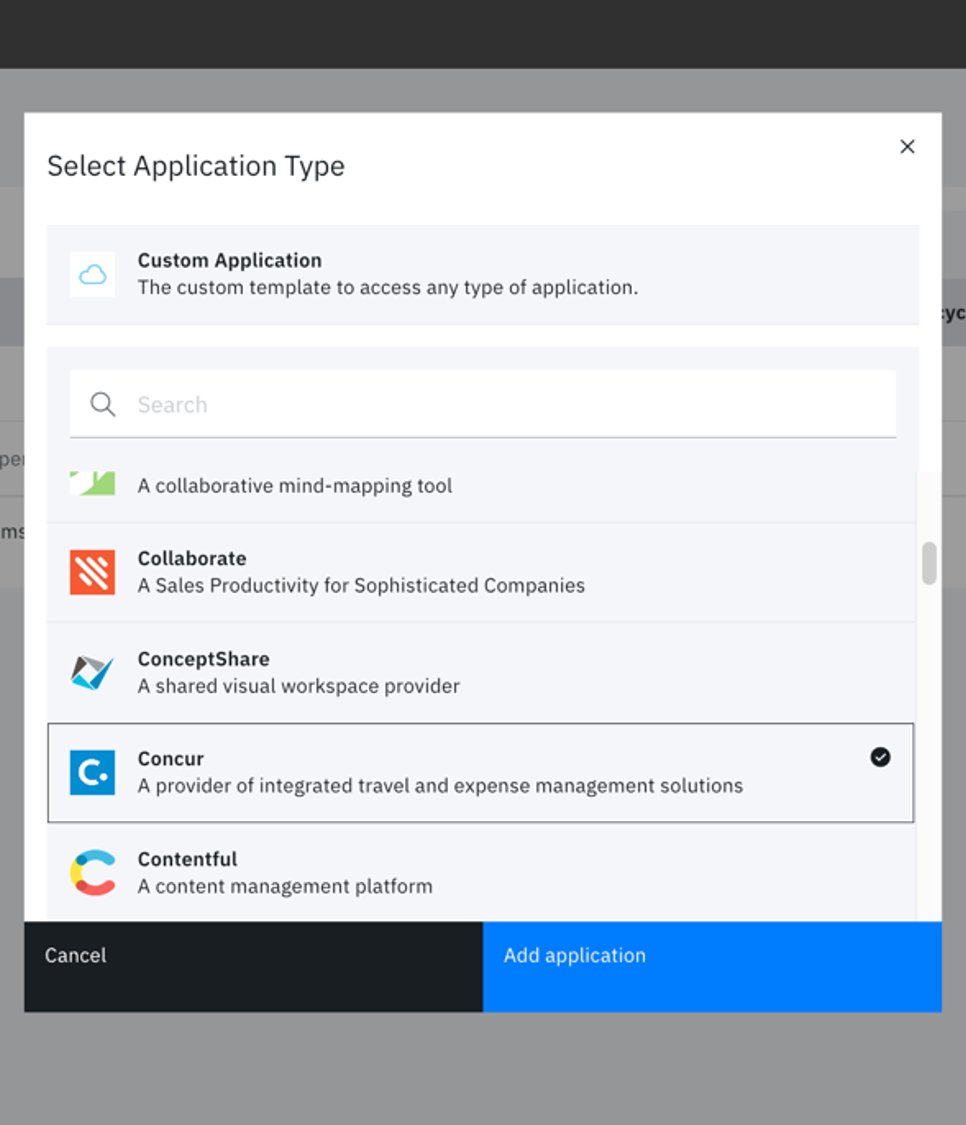
Verify provides detailed configuration steps for each cloud app connector. You will also need to log in to the cloud app, for example, Salesforce to complete configurations and gather parameters for the connector.
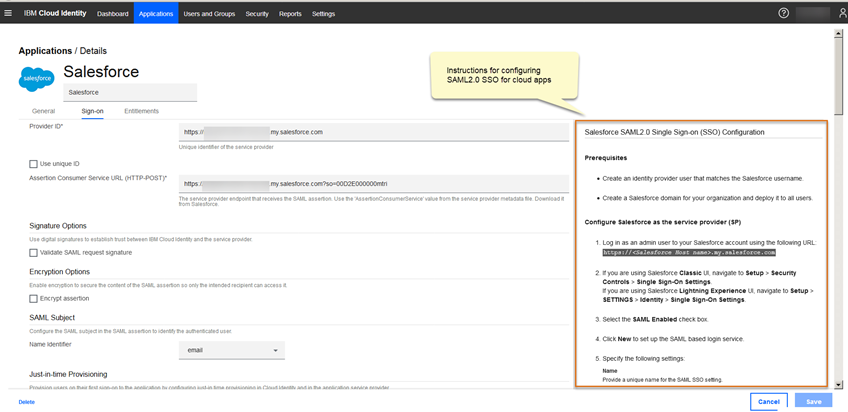
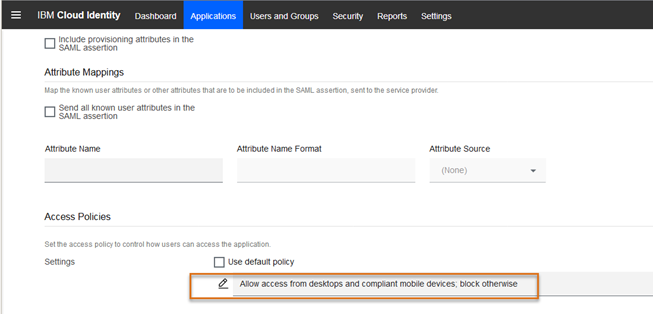
When the Sign On configuration is complete, you must also select the Access Policy for the application. This is where you can identify access criteria. For example, if you only want managed, compliant devices to access Salesforce, all other devices will be blocked from access. So, if you have a device user that is not enrolled in MaaS360, they will not be able to access the app. Or if they are enrolled in MaaS360 but are not in compliance with mobile policies, they will not be able to access the application.
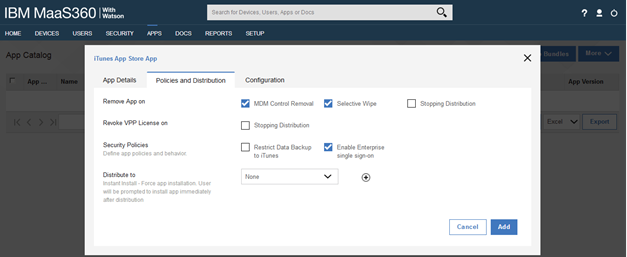
Configure Apps in MaaS360 for Enterprise Single Sign On
In the MaaS360 portal, you must add the mobile apps to the MaaS360 App Catalog and set Enterprise Single Sign On. Or if you have existing application in the catalog, you can edit the app catalog entry to set enterprise single sign on. Therefore, if you configure a Salesforce connector in Verify, you must add the Salesforce mobile app to the MaaS360 App Catalog and Enable Enterprise single sign-on.
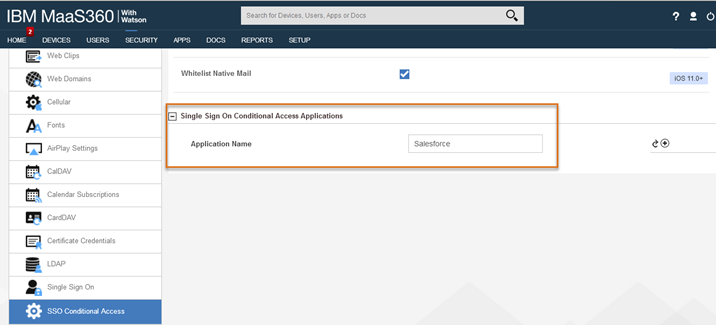
Set SSO Conditional Access in MaaS360 policies
Depending on the mobile device type: iOS, Android, or Windows 10, you must update the MDM policy in MaaS360 to enable SSO Conditional Access for the apps. The apps display in the Application Name selection based on Enterprise Single sign being checked in the App Catalog. After you save and publish the policy, the updated policy must be assigned to the mobile devices to take advantage of SSO and conditional access. This can be accomplished by setting the policy as the default, assigning the policy to a device group or single device.
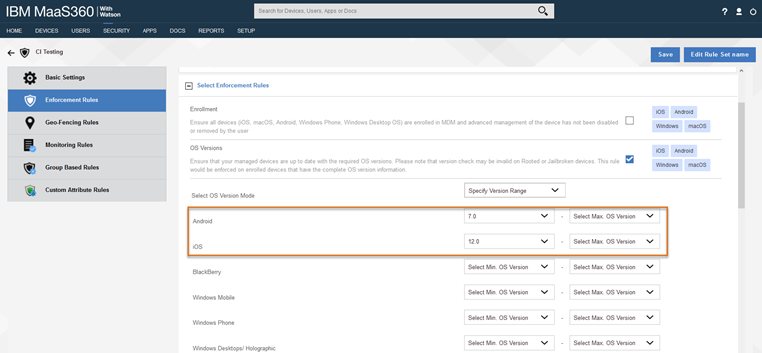
[Optional] Configure Compliance Rules in MaaS360
You can also configure compliance rules in MaaS360 to evaluate whether a device is compliant based on criteria you set. Compliance rules are very flexible; there are standard compliance conditions, such as checking for jailbroken devices, or making sure the device has a current OS version. You can also create custom compliance conditions based on group based rules and custom attributes. Configure the Compliance Rule and assign it to mobile devices by making it the default or assigning to a device group. If the device is marked as out of compliance and you set the access controls in Verify to check for compliance, then the device will not be able to access the cloud apps you configured for SSO Conditional Access.
Start accessing mobile apps using SSO
To take advantage of the conditional seamless SSO, the mobile device must be enrolled in MaaS360 with the policy assigned and the enterprise SSO enabled apps distributed to them. When the device enrolls, the SSO payload and identity certificate is provisioned to the device. The user simply taps the app to open it and the seamless SSO authentication and conditional access check is done.
Resources
Video Course: Implementing Seamless SSO with MaaS360 and Verify
These IBM Security Learning Academy videos walk you through the steps to integrate IBM MaaS360 with IBM Verify in to enable seamless single sign-on for mobile devices and desktops.
💎Margaret Radford, IBM Security
Updated 7 months ago
