Enable MFA for applications
Introduction
Multi-factor authentication protects applications and critical system assets like it's network and servers from bad actors. Verify provides this capability through a simplified policy editor. Admins can create access policies based on various user, device, geographic, and network based context to decide whether to allow, deny, or challenge for MFA.
Customers of Verify can easily create block or allow lists without much effort. In this config guide, we'll create a simple policy based on some conditions that we can gather from the user.
Pre-requisites
To complete this guide, users must have a free trial or a paid instance of Verify with the multi-factor authentication subscription.
Create an access policy
Log into your tenant as an admin (https://yourtenant.verify.ibm.com).
Steps
- Navigate to Security
- Select the "Access policies" tab.
In this area, you will be able to create specific access policies around user and device information to determine if access should be allowed, denied, or challenged for a second factor. - Click "Add policy"
- Give your policy a name
This is how you reference the policy inside applications. It will also be displayed during MFA challenges in your reporting events. - Select Federated sign on policy
Since user's will be authenticating via SSO, choosing this policy will allow you to quickly protect applications in your catalog. - Optionally, on the Rauthentication page, select how often you would like MFA to be performed on a recurring basis.
- Create a new policy rule
- Give the rule a name and create some conditions; If:
- User attributes > Group attributes > must exist in attribute > Sales
- Device attributes > New device > Is > detected
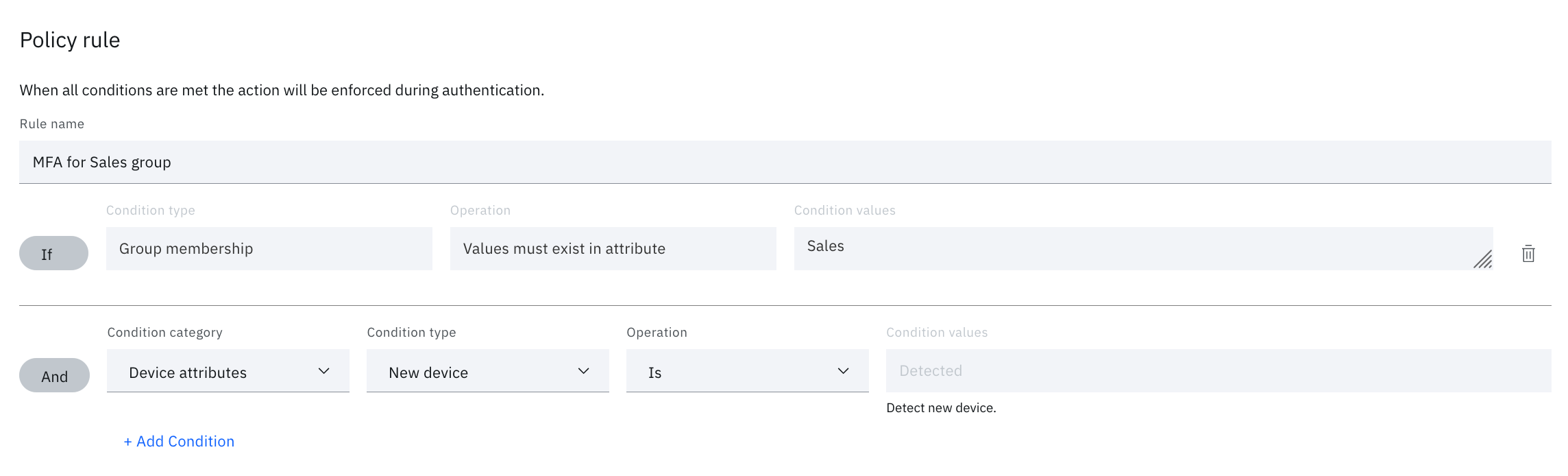
- Select the action to take when the condition is met including which MFA methods are allowed.
Select "MFA per session". Optionally, If not conditions are met, the default rule applies. - Save the rule
- Save the policy
Add your MFA policy to applications
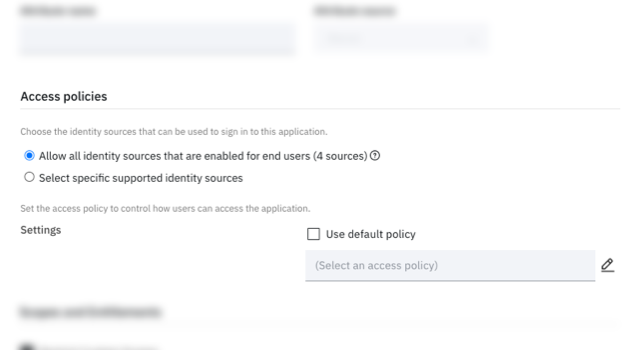
Your access policy was created successfully. Now, once you onboard applications to your catalog, you can apply different access policies to each application in the "Access policies section" under the "Sign on" tab.
Handling multiple access rules in a single policy
Adding more than 2 policies will provide a way to specify the sequence of evaluation. Policy rules are evaluated from top to bottom. Once a condition is met, the access policy stops. Adjust the sequence to apply a different evaluation workflow for your policy. Keep this in mind when creating specific access rules. With access rules, global access policies can be achieved by combining conditions.
Updated over 2 years ago
