Identity linking
Introduction
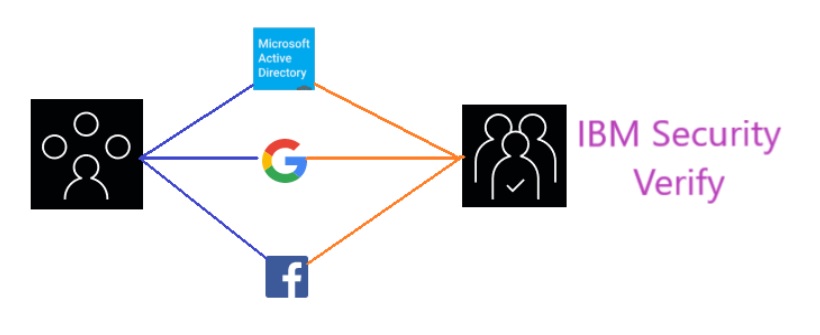
IBM Verify allows you to link the various accounts of an end user to a single account record in a primary identity source realm. This provides flexibility for the end user, in terms of how they choose to authenticate, and also provides a single record for storage of user information and application entitlement.
Prerequisites
To set up account linking you will need to have at least one SAML Enterprise or Social login provider configured. For social providers, see Using social providers. For SAML Enterprise providers, see details in IBM Documentation.
Configuration
Global configuration
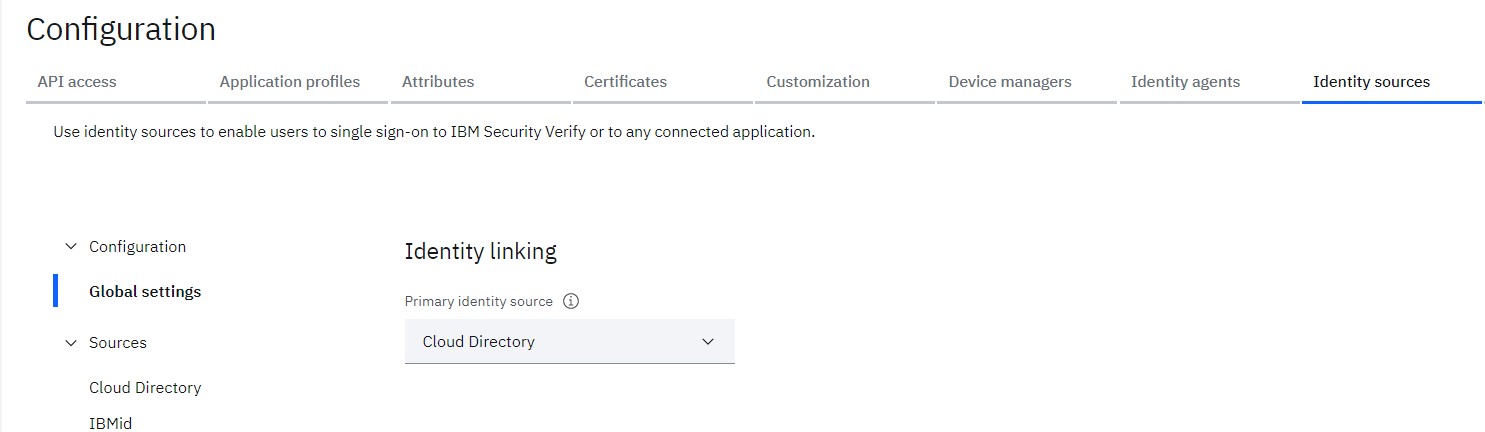
The Primary identity source for the tenant identifies the identity source where the account records will be located for identity sources that are enabled for account linking. By default it is set as Cloud Directory.
- Login to your IBM Verify tenant admin console as an administrator
- Navigate to Configuration > Identity Sources
Supported primary identity sources
At present, only the Cloud Directory and SAML Enterprise identity sources can be defined as the Primary identity source.
Lets keep the Cloud Directory as the primary identity source
Enable the identity linking for an identity source
- Login to your IBM Verify tenant admin console as an administrator
- Navigate to Configuration > Identity Sources
- Select a SAML Enterprise or Social provider identity source
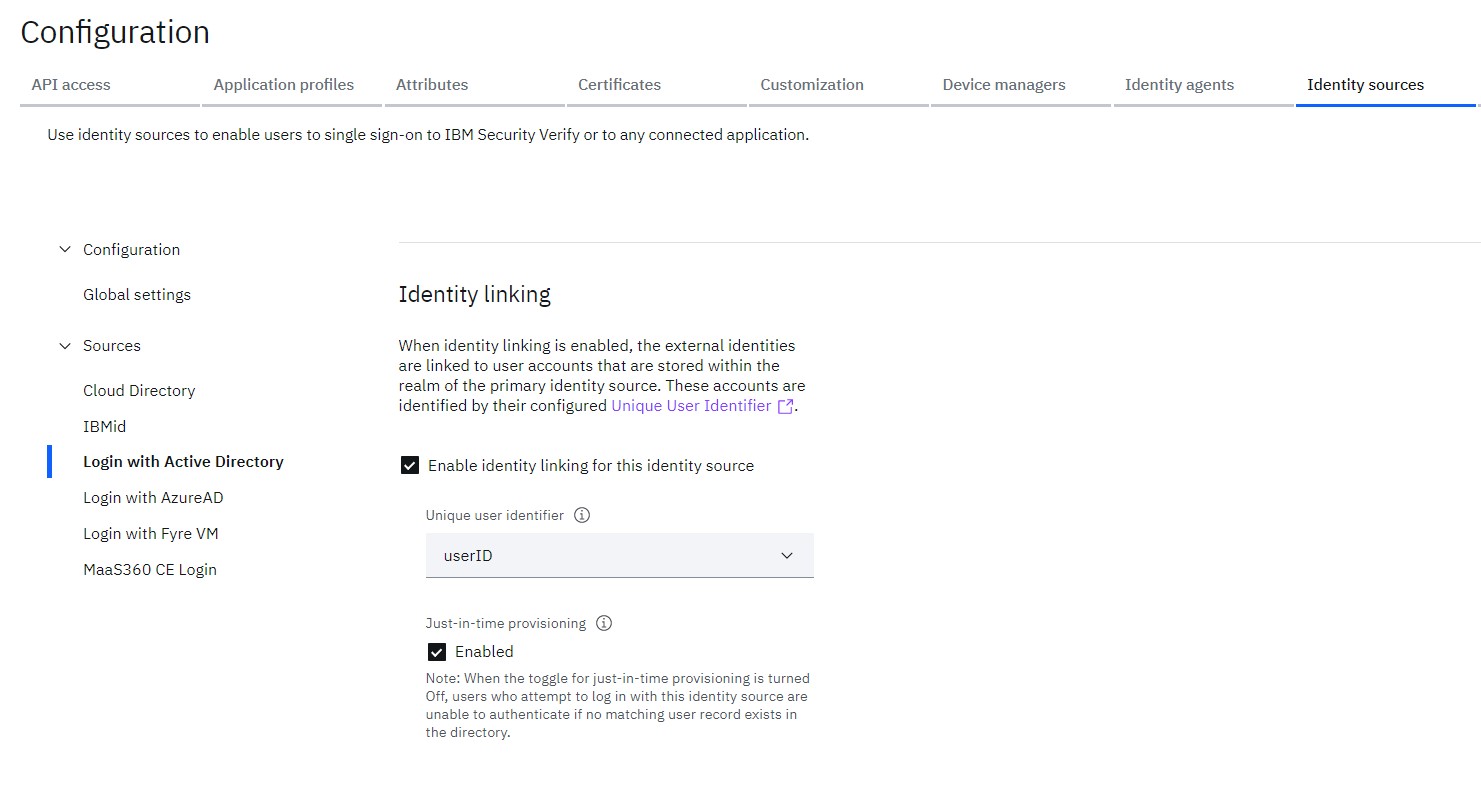
- Navigate to Identity linking section
- Enable the checkbox for Enable identity linking for this identity source
- Select the appropriate Unique user identifier from the list (e-mail is often a good choice)
- Enable the Just-in-time provisioning
Just-in-time configuration
If selected, a user record gets created in Primary identity source realm for an authenticating user whose record does not exist. If not selected, a user that has no record in Primary identity source will be denied access.
More details can be found at Identity source configuration
Test identity linking
Create a user in Primary identity source
For this test you will create a user in the primary identity source (rather than relying on Just-In-Time-Provisioning).
- Login to your IBM Verify tenant admin console as an administrator
- Navigate to Users & groups
- Create a new user that has a username which matches the account linking attribute of the user in the identity source you've enabled for account linking. (e.g. [email protected])
Login using the identity source you set up with account linking
- In new browser, access the tenant as and end user
- Select the identity source you set up with account linking
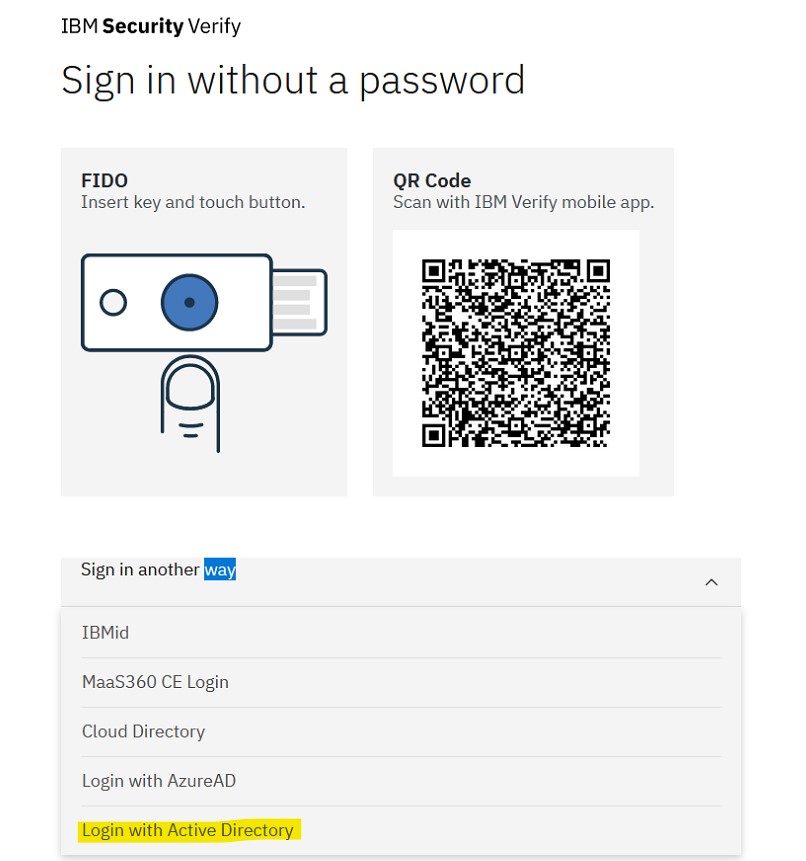
- Login with your identity source credentials
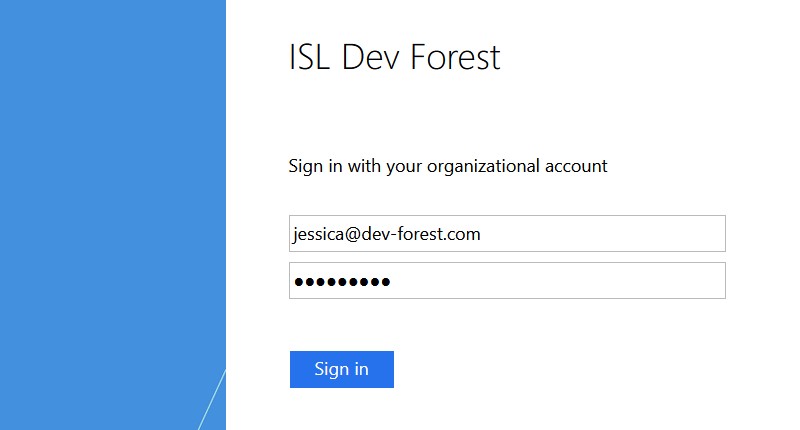
- Validate user is able to login successfully
Validate linked user details
- Login to your IBM Verify tenant admin console as an administrator
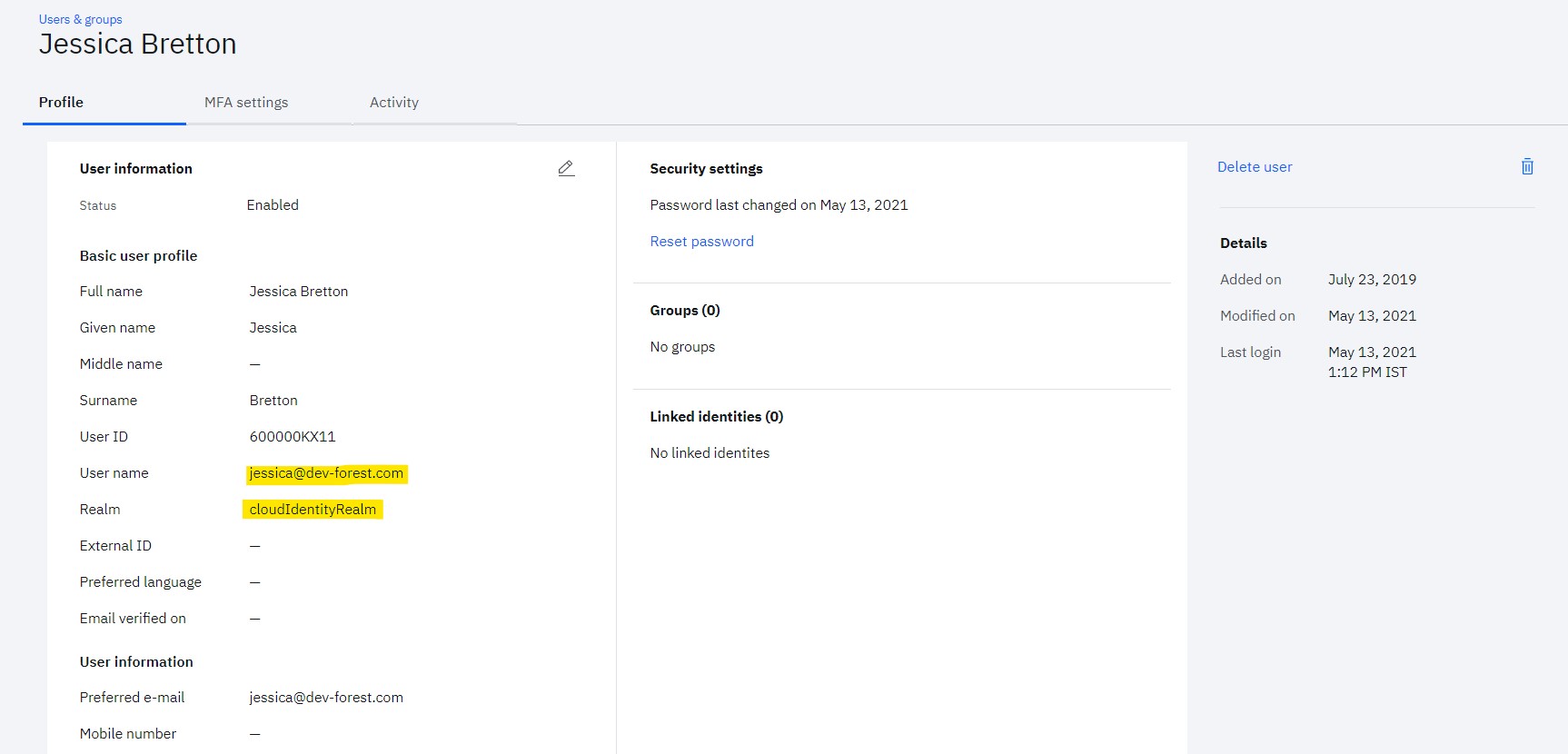
- Navigate to Users & groups
- Validate the details of existing user (e.g. [email protected])
- User will have details of linked user account
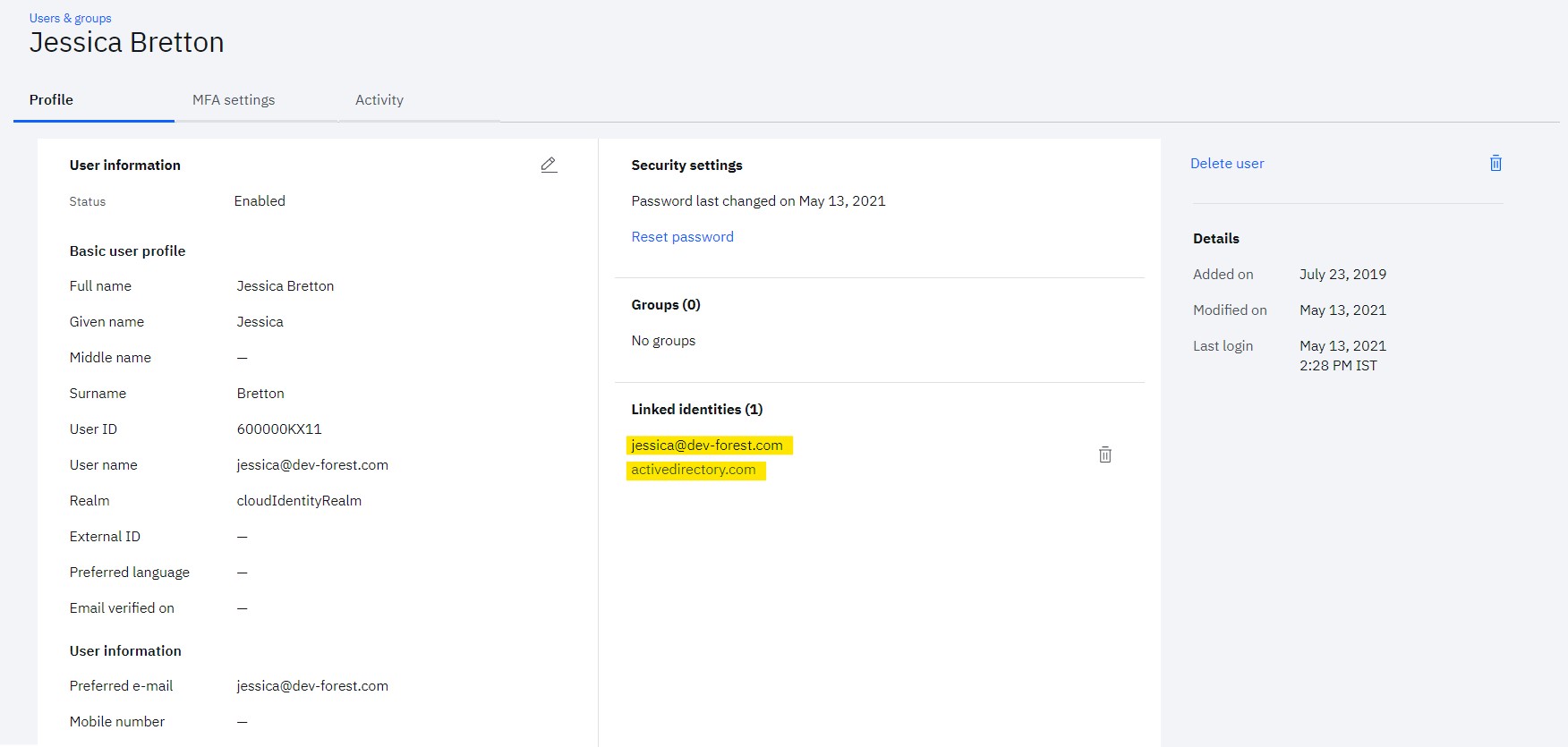
As the new identity is linked to existing user, it will have access to all entitled applications. This will ensure that although the user has accounts in multiple identity sources, they are treated as single user in Verify and have correct entitlements.
Nilesh Atal, IBM Security
Updated 7 months ago
