Unified MFA
Verifying users identities should be a seamless process for any enterprise to implement, regardless of use case (consumer or workforce, citizen or contractors). Verify provides mechanisms to verify users through basic methods (SMS / Email) all the way to advanced methods (such as push notification / biometric / FIDO2). Multi-factor adds a critical layer of defense that is often not just suggested, but essential.
MFA uses any combination of two or more factors to authenticate identity and keep vital assets secure from fraudulent access. By now, we’ve all used two-factor authentication (2FA) online to authorize a login or transaction by combining a password with an SMS code sent to our mobile device. If one factor is compromised, the system is still secure.
Three main factors can be put into play to confirm identity:
- Something you have — a physical item such as a bank card, key fob or USB stick, phone, watch, etc.
- Something you know — a “secret” such as a password or PIN.
- Something you are — a biometric factor such as fingerprints, voice, iris scans and other physical characteristics.
When to use multi-factor
When there are aspects of the user's login attempt that seem suspicious based on various contextual triggers, MFA should be used. There is a time and place for MFA to be challenged however. Perhaps you want to challenge when users meet a certain set of criteria. This is known as conditional MFA. IBM Verify supports conditional MFA through access policies. This is separate from Risk-based authentication and Adaptive access which dynamically scales up and down risk based on continuous factors that are evaluated through IBM's Trusteer machine learning algorithms.
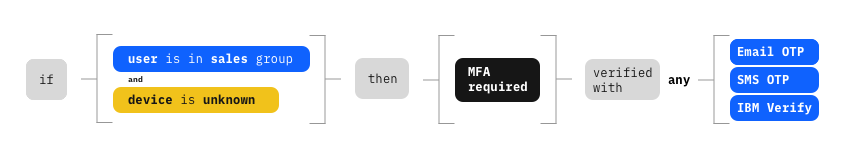
Conditional MFA allow customers to specify criteria if MFA should be challenged and when. These criteria include:
- User attributes (department, title, email domain, etc)
- Group information (member, or not, of a certain group of users)
- Geographic rules (Country, city, state, etc)
- Network rules (IP subnet, VPN, etc)
- Known device (User is coming from a fingerprinted device)
- Application context (What application or scope is requested)
- Managed device (MDM enrolled)
- Compliant device (MDM enrolled and compliant with IT policies)
Building out conditional statements for when MFA is required gives customers the control over precislely when MFA is required for a specific application. Actions taken when conditions are met are determined by teh company as well. Actions include:
- Allow access without MFA
- Challenge for MFA, all the time
- Challenge for MFA, only once per session
- Block access
When challenged for MFA, users need to be allow to enroll MFA factors if they have never enrolled before. This is called inline muilti-factor and without writing any code, customers of Verify can enable this in less than a few seconds.
Selective MFA
Applications across the enterprise are not always equal. Access to a financial database application, BI tool, document sharing, and email may be treated completely separately. Through specific access policy rules, certain MFA methods may be not approved (ex. SMS one time passcode) to reach the level of security required for that application. Verify supports selective MFA methods by policy rule allowing for granular control over the security requirements dictated by numerous security regulations.
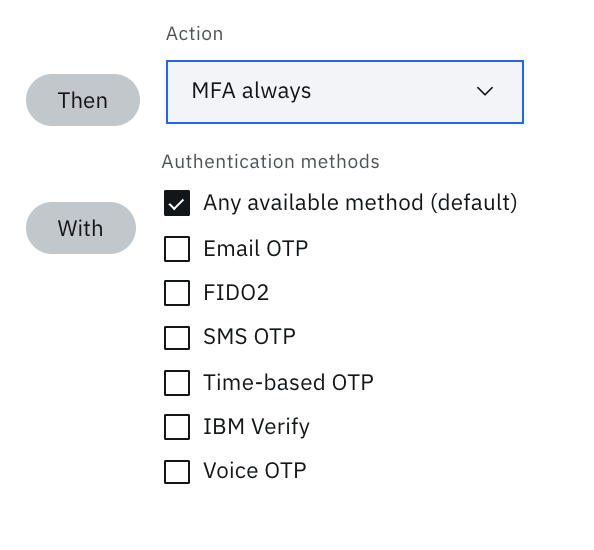
Stacking multiple rules together create a global policy of numerous conditions that give corporations pinpoint accuracy on how the users will experience multi-factor authentication for precise verification.
Unified MFA to provide security everywhere
With Verify, we unify multi-factor methods across applications and systems. This provides a single source of truth for verification methods for access to Linux server shells, remote desktop to servers, Windows desktop login, VPN RADIUS, on-premise and web applications alike.
With Verify, customers have immediate access to protect:
Each system uses the same enrolled factor for user verification rather than have multiple tools to accomplish the same type of task. One enrollment portal handles all MFA factors making the process painless for users.
Updated 7 months ago
