Using social providers
Introduction
What better way to provide a clean authentication experience to your consumers than to offer them the ability to use credentials that they already have. Essentially, this allows users to bring their own identity (BYOI) which is typically already validated. This approach is very common for consumer identity access management (CIAM) use cases as either the primary authentication method or as a convenient alternative to other credentials.

Users are offered the option to use social providers when authenticating for access to applications which have been enabled for social sign-on support. These will usually be consumer applications - it would be unusual to allow employees to authenticate using social providers. At this time, social providers cannot be used for access to the IBM Verify launchpad or admin portals.
Pre-requisites
For every social provider you want to enable, you will need a developer account with that provider so that you can register your Verify tenant as a client. For more information on each individual social provider, read the provider-specific entries in the IBM knowledge center.
Configure the social providers
In in Verify Admin UI, navigate to Configuration and then choose the Identity sources tab. Click the button Add identity source" and choose the provider to onboard. Instructions are provided on screen, but additional details are provided in the knowledge center.
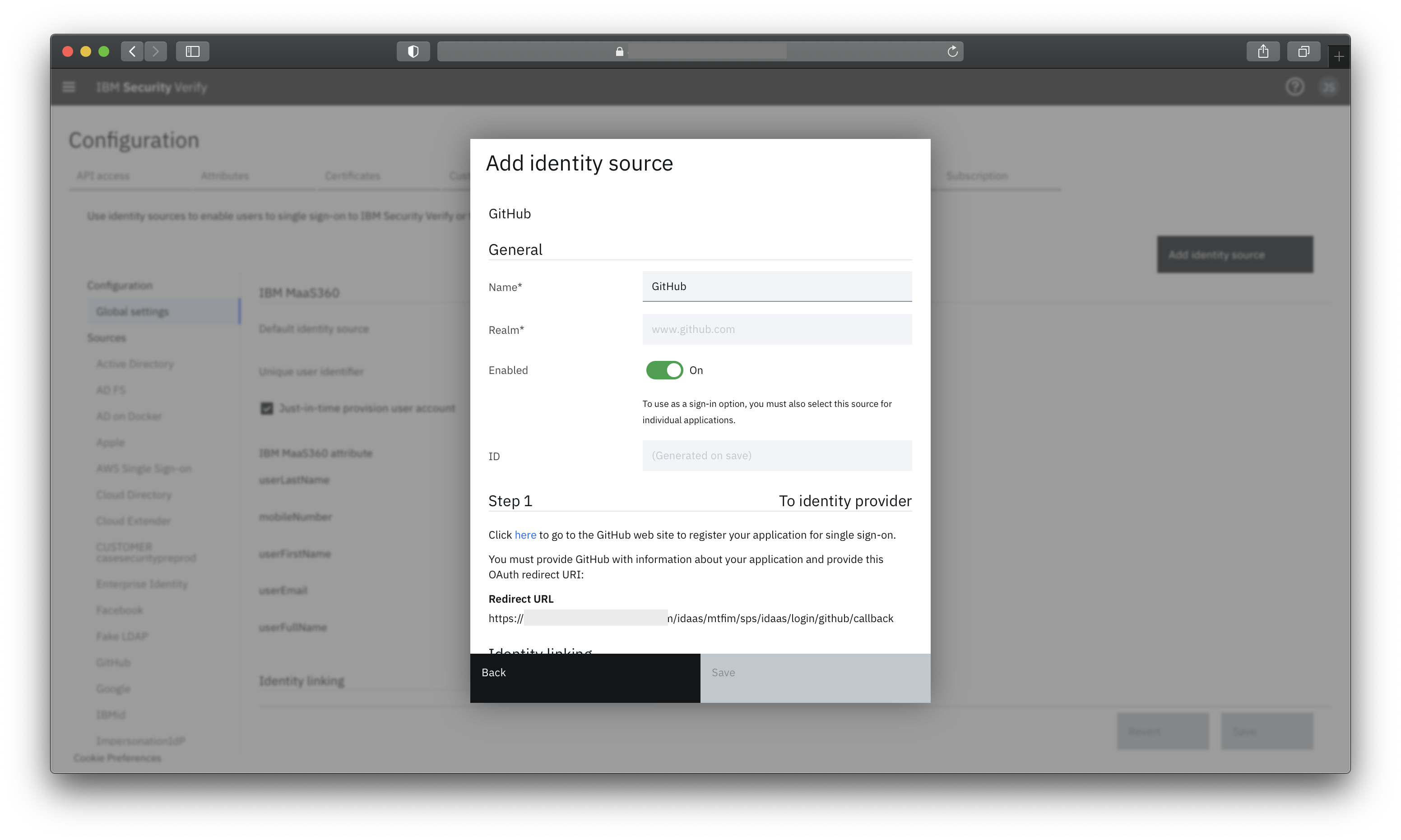
Configuring GitHub as a external provider for user authentication
Read through the appropriate entry in the IBM knowledge center to configure the social identity provider.
Every provider is different
While all social providers communicate with Verify over standard protocols, the configuration and requirements of each differ slightly. For ease of configuration, Facebook, GitHub, and LinkedIn tend to be the quickest to configure.
Enable an application for social sign-on
Once one or more social providers have been onboarded, the next step is to configure an application to use them. This is achieved by navigating to Applications and editing the application properties. Both SAML and OpenID Connect apps can be enabled to use social providers.
For this guide, we will use the sample SAML application. If you're not familiar with this, read more on the sample application provided by IBM Verify for testing purposes.
On the Sign on tab of the application, scroll to the Access policies section. Select the option that says "Select specific supported identity sources". This will enable you to select the social providers you want to be offered when users authenticate to access this application.
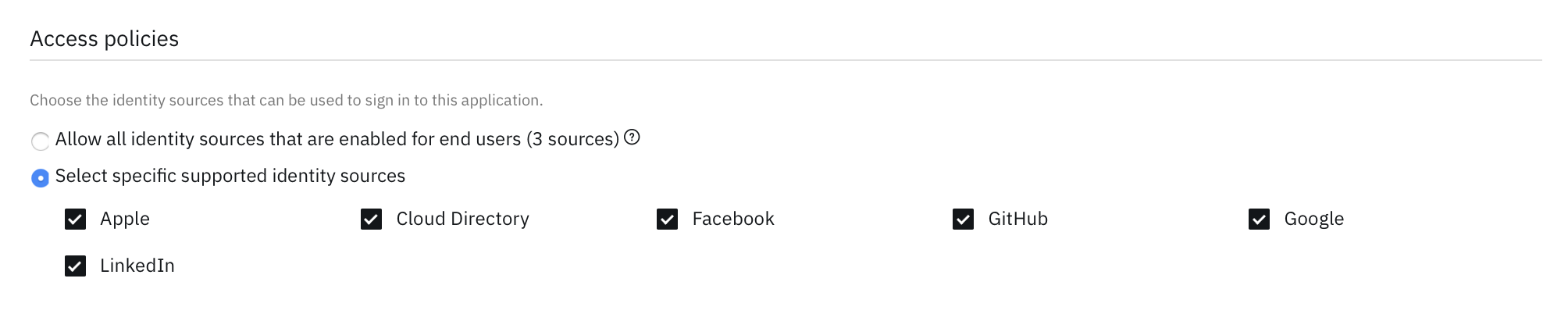
A list of configured social providers for the IBM Verify sample application
Don't forget to save the updated application configuration.
Try it out
Start a new browser session and access the sample application's login URL to initiate the login request to Verify. You will now be met with a selection page for different authentication providers that are enabled.
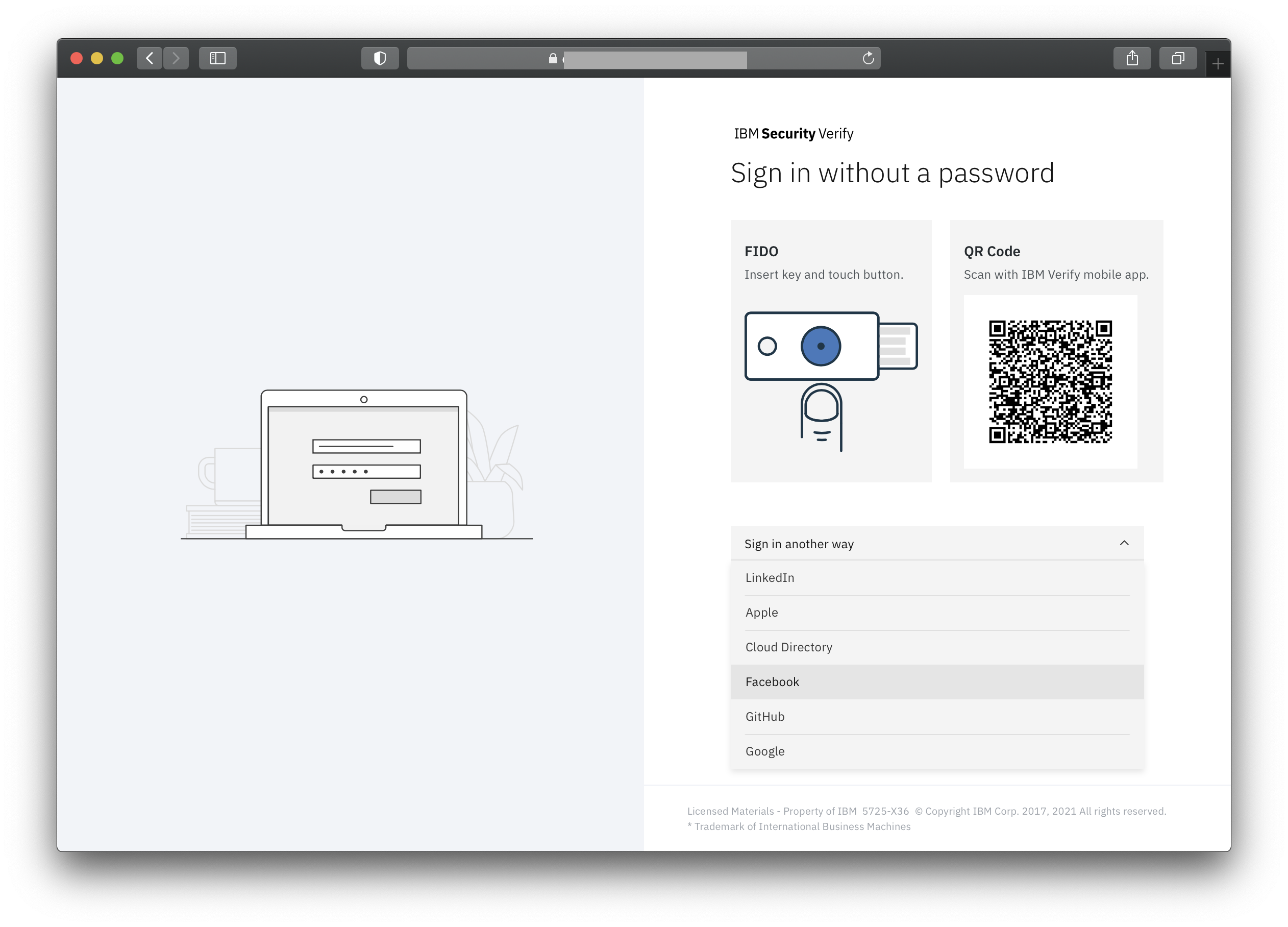
Selecting one of the providers will immediately redirect you to the provider. If you are not already logged into the provider it will show its own login page. The first time you use this provider to authenticate to Verify, it may also ask for approval to provide your identity data.
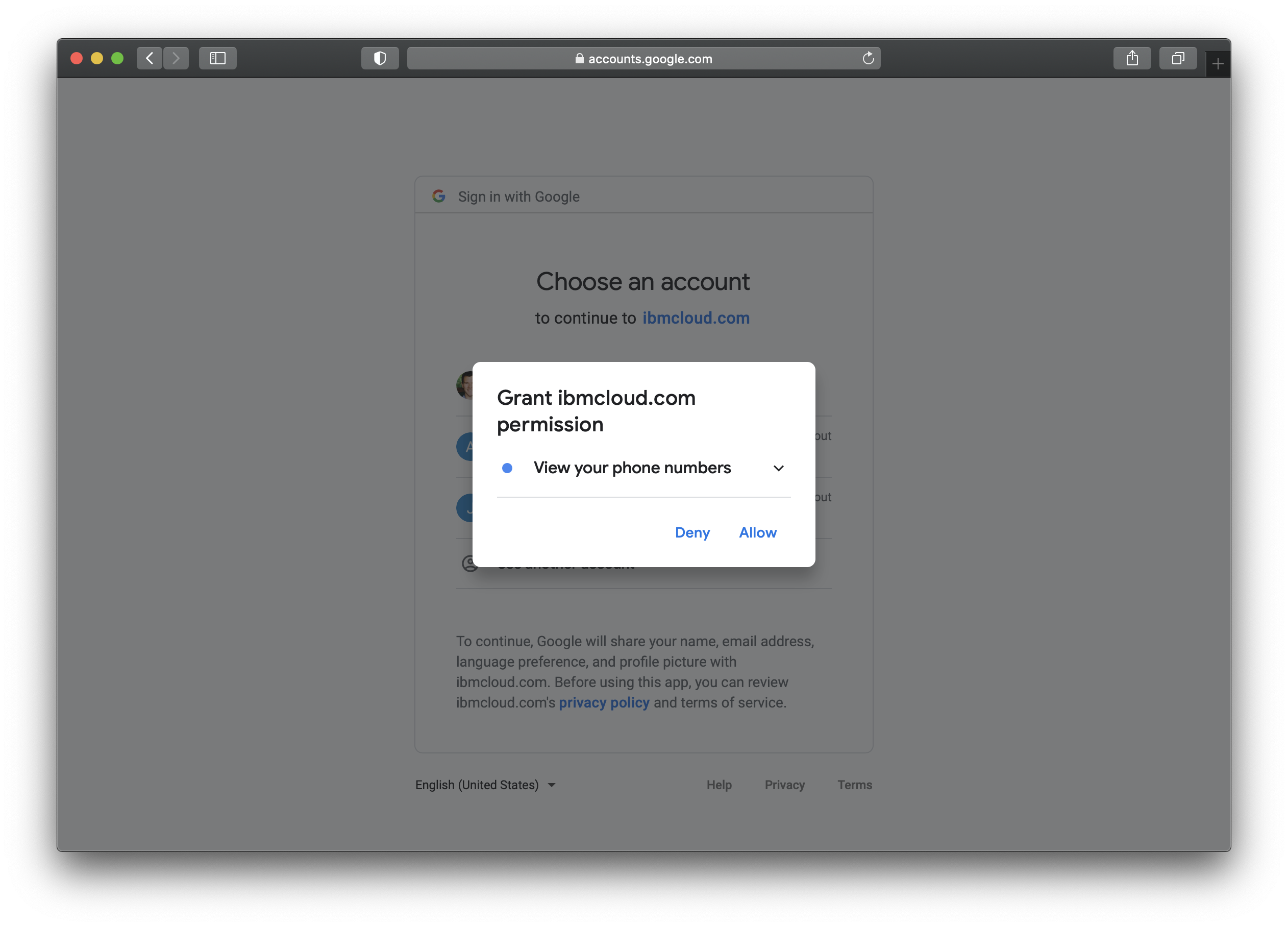
After you successfully authorize Verify, you will be logged into your application with the information provided by the social provider. An account will be created in the Verify Cloud Directory as part of the login process.
Adam Case, IBM Security
Updated 7 months ago
