Multi-factor authentication
IBM Verify supports a wide array of multi-factor authentication mechanisms to verify users during authentication from web applications, desktops and mobile, and servers (both cloud and on-premise). Multi-factor authentication ensures that users who are accessing applications and servers are truly the right person.
Every instance of IBM Verify includes the capability to use multi-factor with any application with little to no configuration required. Access policies are supported throughout to create conditions where MFA is required. Going one step further Adaptive access can be applied to limit invocations of MFA to reduce user friction even more.
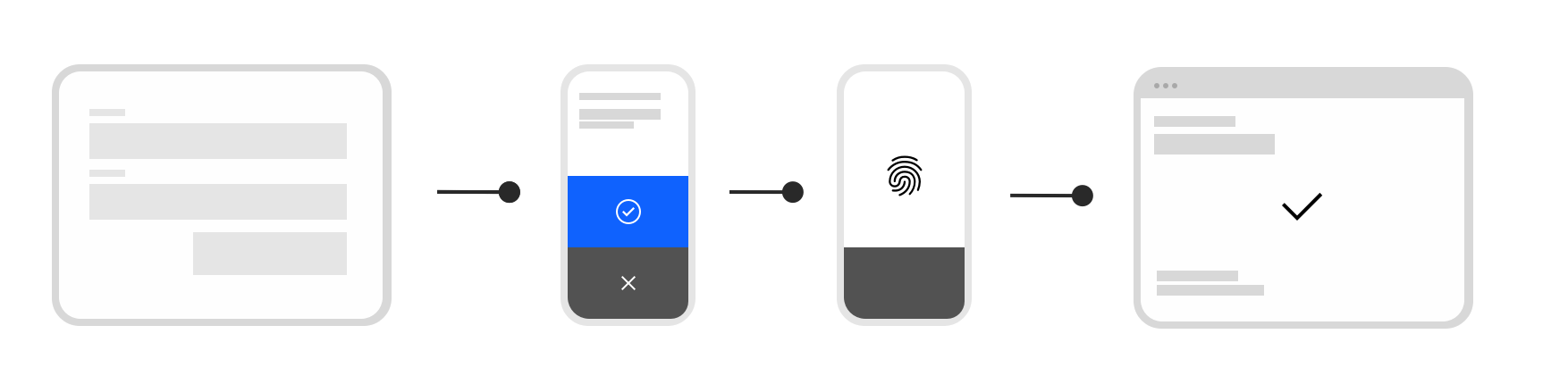
Applying MFA verification should not be a burden on users. This is why Verify has been designed with users in mind to ensure that the process from enrollment through to verification is seamless. During user authentication, Verify can be configured to require users to enroll any allowed MFA option as a one time action.
Use IBM Verify to secure your network, applications, workstations, and on-premise systems using a single set of MFA enrollments.
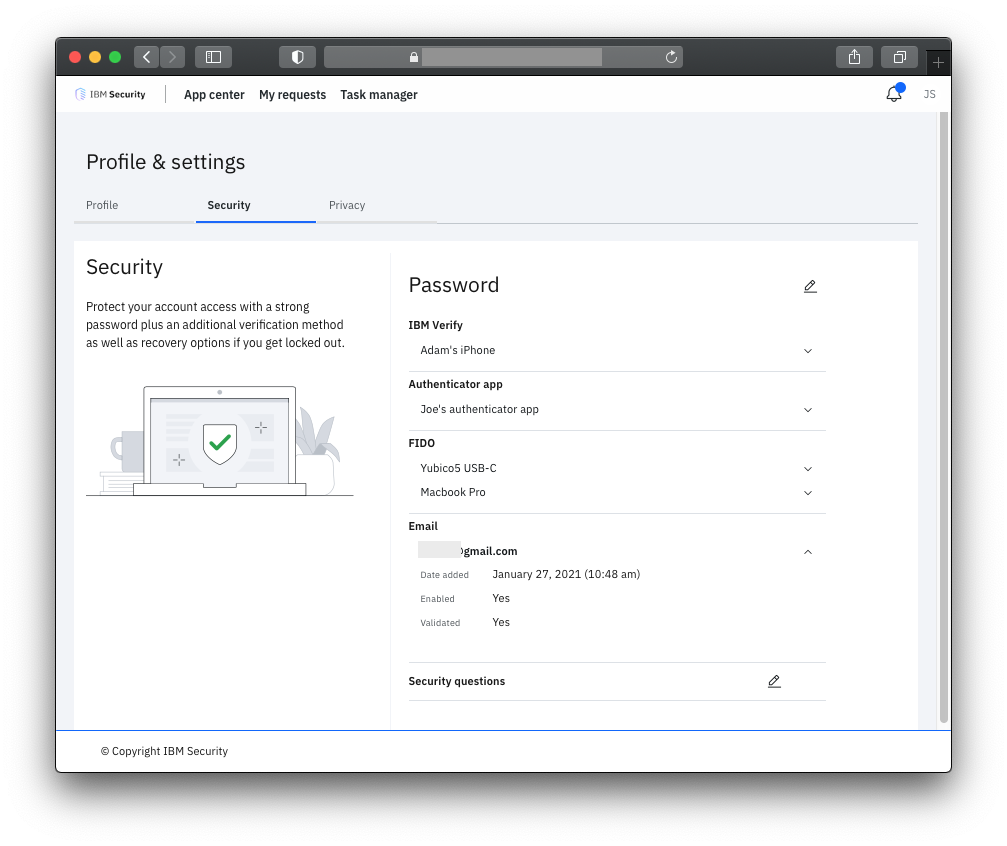
Supported verification factors
In order to provide support for a wide variety of use cases, Verify provides options for admins to enable to secure user's personal profiles as well as their applications. It is important to know that not all factors are equal in their security, so be aware of the pros and cons of each factor when deciding what to enable.
From our point of view, using platform authenticators such as TouchID and Windows Hello or physical devices like a FIDO authenticator and IBM Verify app for iOS and Android is preferred.
| Factor | Description |
|---|---|
| Knowledge questions (not recommended) Note: This is not enabled by default. Customers wishing to use this method can contact IBM Support to enable it in their instance. | This method allows for users to enter known answers to questions. |
| Email OTP | A one time code is sent to the user's email address. |
| SMS OTP | A one time code is sent to the user's phone number on record. This number must support the ability to receive SMS. Landline phones, such as office phones, will more than likely not work. |
| Voice callback OTP | A phone call will occur with the user's phone on record reading back a 6 digit code. |
| Time based OTP (TOTP) | A randomly generated code is provided in the user's authenticator application. This method can be configured with IBM Verify, Duo, Google authenticator, Microsoft authenticator, and other apps following this standard. |
| IBM Verify App (user presence) | This is an enrolled factor to that uses the IBM Verify app (located in both iOS and Android app stores) to support push notifications. This method involves the user simply pressing "approve" and access will be granted. |
| IBM Verify App (biometric) | This is an enrolled factor to that uses the IBM Verify app (located in both iOS and Android app stores) to support push notifications but requires the user to use fingerprint or other device biometrics to approve. |
| FIDO authenticator (without PIN support) | A hardware token that is typically inserted into the device that ensures the user who's authenticating also is physically present on that same device. This supports both FIDO2 and FIDO U2F protocols. This method is used for 2nd factor verification only. |
| FIDO authenticator (with PIN support) | A platform authenticator or hardware token that supports a PIN or biometric protection to secure the resident key on the device. This can be used for password-less authentication (configurable by admins) and 2nd factor authentication. Examples of this factor are Apple TouchID, various Android devices, Yubico, Windows Hello, and others listed on the FIDO alliance website. |
Updated 7 months ago
