Refresh Tokens
Refresh Token grant type
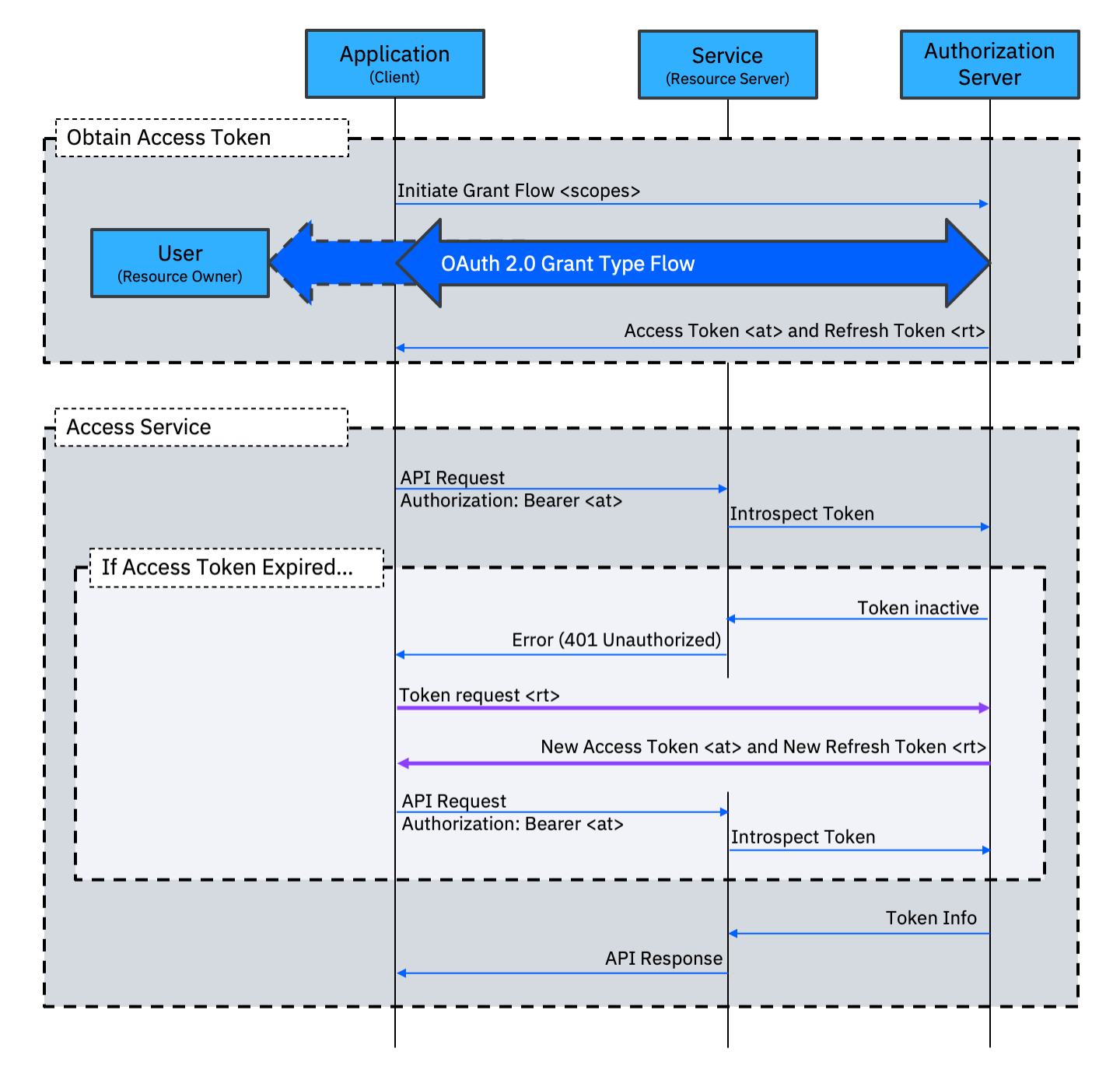
The Refresh Token grant type has a very specific purpose; it allows an application to obtain a new Access Token without having to repeat the full user interaction that was required to establish the initial grant. This allows an application to maintain its delegated access for an extended period.
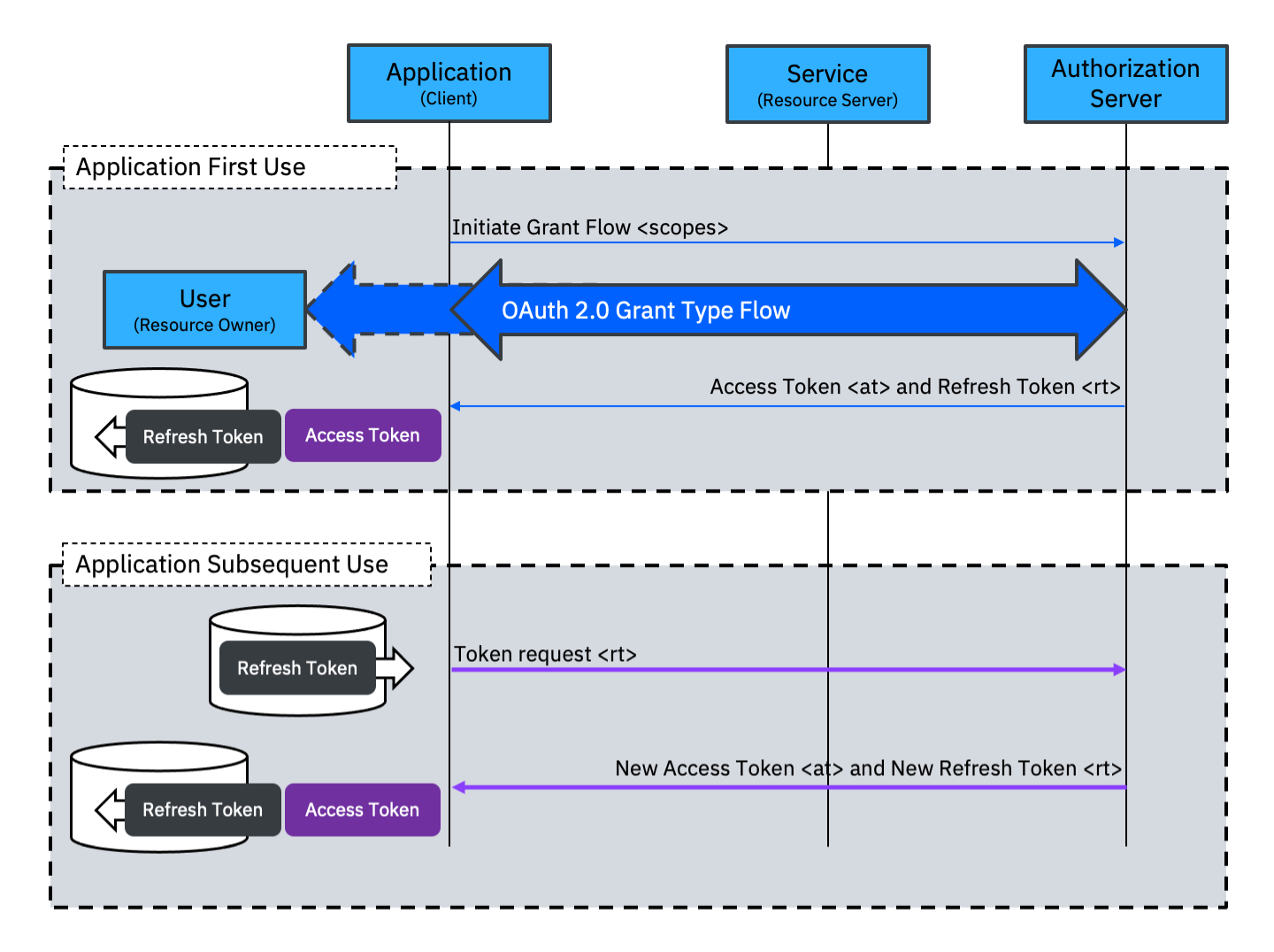
The Refresh Token grant type is not used alone. At least one other grant type must be available to establish the initial grant. When the Refresh Token grant type is enabled, a Refresh Token is returned at the end of the initial grant type flow. This Refresh Token will have a lifetime that is (much) longer than the Access Token. The application stores the Refresh Token and uses the Access Token for access to services. At a later time, usually after the Access Token has expired, the application can use the Refresh Token grant type to receive a new Access Token (and a new Refresh Token).
The Refresh Token grant type can be used to allow an application to obtain a new Access Token if a user session lasts longer than the lifetime of the Access Token obtained at the start of the session. In this case the Refresh Token would will usually be stored as part of the user session.
By having a short Access Token lifetime, but allowing the Refresh Token flow, an Authorization Server forces applications to regularly re-request access. This gives an opportunity to re-evaluate access policies. Having a short Access Token lifetime can also mitigate the impact of a stolen Access Token.
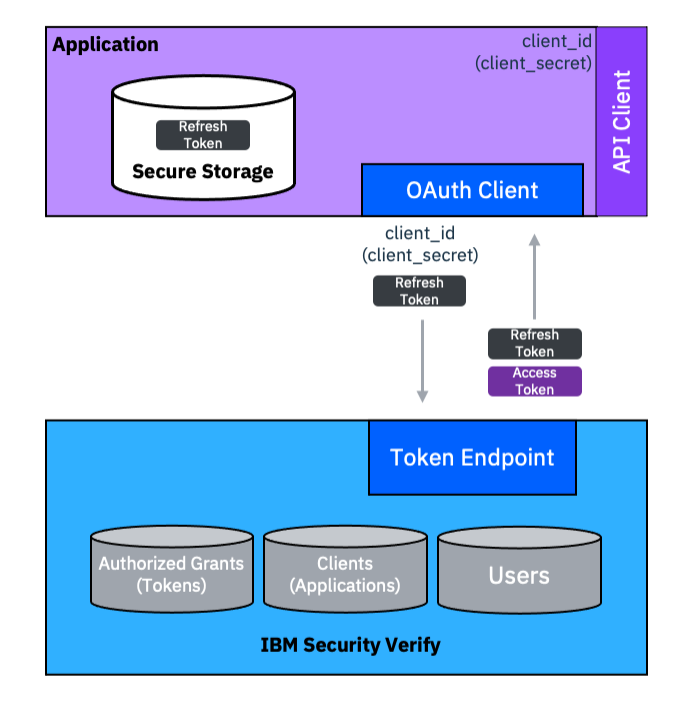
The Refresh Token grant type can also be used allow an application to seamlessly obtain a new Access Token when it is started after some period of being shut down. This is a common pattern for mobile applications that never want to run a full OAuth grant type flow again after initial registration.
When implementing this use case, the Refresh Token should be stored in a secure location. On a mobile device this usually means the key-chain. For additional security, the Refresh Token can be encrypted with a key from the secure enclave so that a bio-metric operation is required to access it.
Jon Harry, IBM Security
Updated over 3 years ago
