Identity proofing
Identity proofing
Introduction
Identity proofing is the process of verifying the claimed identity of a person. It is a critical step in protecting against identity theft and fraud. Identity proofing can be done using a variety of methods, including:
- Knowledge-based authentication (KBA): This is the most common form of identity proofing. It involves asking the user to provide information that only they would know, such as their date of birth, mother's maiden name, or previous addresses.
- Document verification: This involves verifying the authenticity of a user's identity documents, such as a driver's license or passport.
Identity proofing can be done online, over the phone, or in person. The level of identity proofing required will vary depending on the sensitivity of the information that the user is trying to access. For example, a bank may require more stringent identity proofing for online banking than for a simple website registration.
Identity proofing is an important part of protecting your personal information and preventing identity theft. By taking the time to verify your identity, you can help to keep your information safe.
Here are some additional benefits of identity proofing:
- Reduced fraud: Identity proofing can help to reduce fraud by making it more difficult for criminals to impersonate legitimate users.
- Increased security: Identity proofing can help to increase security by making it more difficult for unauthorized users to access sensitive information.
- Improved customer experience: Identity proofing can improve the customer experience by making it easier for legitimate users to access the information and services they need.
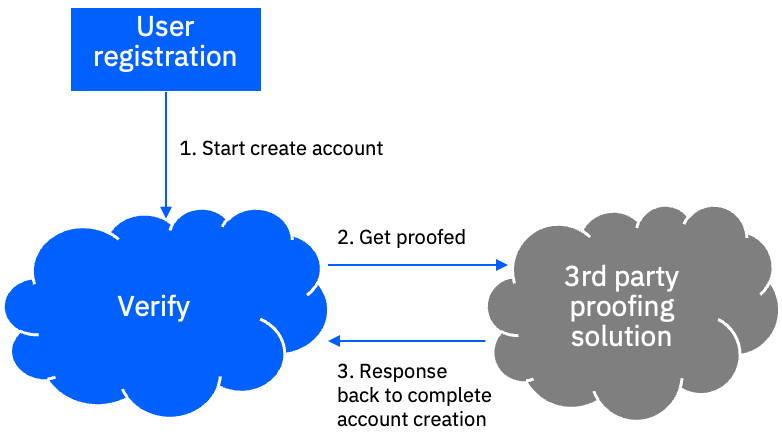
IBM Verify has the ability to integrate with an OIDC based identity proofing vendor to add this functionality to various user journey flows. The integration supports both the OIDC spec version of identity proofing as well as vendor specific OIDC implementations. It was designed with a "bring your own vendor" model in mind, allowing for dynamic configuration that can be molded to fit a variety of generic OIDC ID proofing implementations using Verify scripted rules.
Updated 7 months ago
