Identity sources
Introduction
An identity source is a repository of user information that an identity provider references for user authentication and for provisioning accounts. You can configure more than one identity source. All configured and enabled identity sources are displayed as options in the Verify Sign In page. Users can sign in to Verify with any of these identity sources.
Managing identity sources
To create identity sources, admins navigate to Configuration, then select Identity sources. Creating a new identity source involves exchanging Verify information with the partner.
Supported identity source types:
| Type | Method | Description |
|---|---|---|
| SAML Enterprise | SAML2.0 | A way for users to authenticate to Verify using existing SAML2.0 supported identity providers. |
| LDAP Note: This method requires an identity agent first. | See Connect to Active Directory | A way to allow users to use existing LDAP / Active Directory credentials to authenticate to Verify. |
| Social (Facebook, Linkedin, etc) | OAuth / OpenID | A way to allow users to log into applications using existing social providers. Read more on using social providers. |
| MaaS360 Cloud Extender Note: Customers must have already integrated an existing MaaS360 tenant and Verify. | API integration | A way to use an existing MaaS360 cloud extender setup for user authentication. |
What is a "realm"
A realm identifies the source of the user who's exists and authenticates in Verify. Realms are unique in each customer's directory. This allows for separation of user data if there are multiple identity sources in use. Typically, realms are domain names (ex. www.ibm.com) or represent the domain of the directory (ex. org.customer.com) however they can be anything that is defined by a user.
Users are identified in Verify by username @realm. This means that a username of "[email protected]" and a realm of "CSEBANK" would be represented by [email protected]_ @CSEBANK. in more complicated deployments, customers have multiple directories and could share usernames, however the realm helps keep things separated
Identity source selection
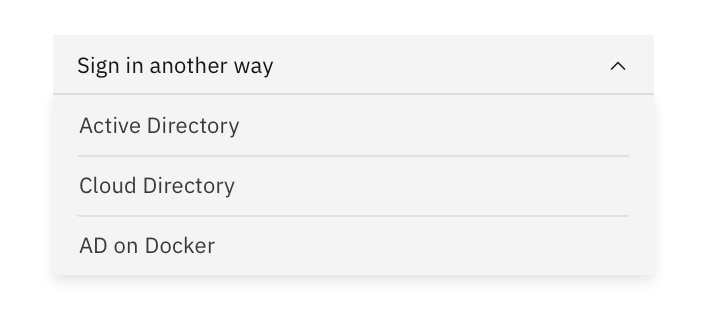
When multiple identity sources are enabled for user authentication or per application, users will get a selection menu in the default login experience. Customers can present these in different ways using branding.
Advanced scenarios
For advanced branding and customizations, In each login page, there is a variable in the head tag that includes all possible ID sources and login URLs. Each ID sourse has its own identifier that allows you to craft a login URL for each ID source.
{
"type": "ONPREMLDAP",
"displayName": "Active Directory",
"passwordless": {
"qr": false,
"fido": false
},
"loginUrl": "https://tenant.verify.ibm.com/authsvc/mtfim/sps/authsvc?PolicyId=urn:ibm:security:authentication:asf:onpremldap&Target=${appURL}&identity_source_id=5a8084b2-0729-490d-bb16-8a7ba874012b",
"id": "5a8084b2-0729-490d-bb16-8a7ba874012b",
"realm": "ONPREMREALM",
"displayLabel": "Sign in with Active Directory"
},
Updated over 2 years ago
