Adaptive access
Adaptive access is a critical part of any organization's Zero Trust strategy. It is important to ensure that the right users on the right devices get connected to sensitive information for businesses. IBM Verify's Adaptive access functionality is backed by IBM Security Trusteer to provide high-fidelity risk evaluation that continuously applies business policies based on contextual information from the user, device, network, and other behavioral elements.
Evaluating risk against true behavioral information encourages less verification challenges, rather than prompting for MFA solely when a new device is detected.
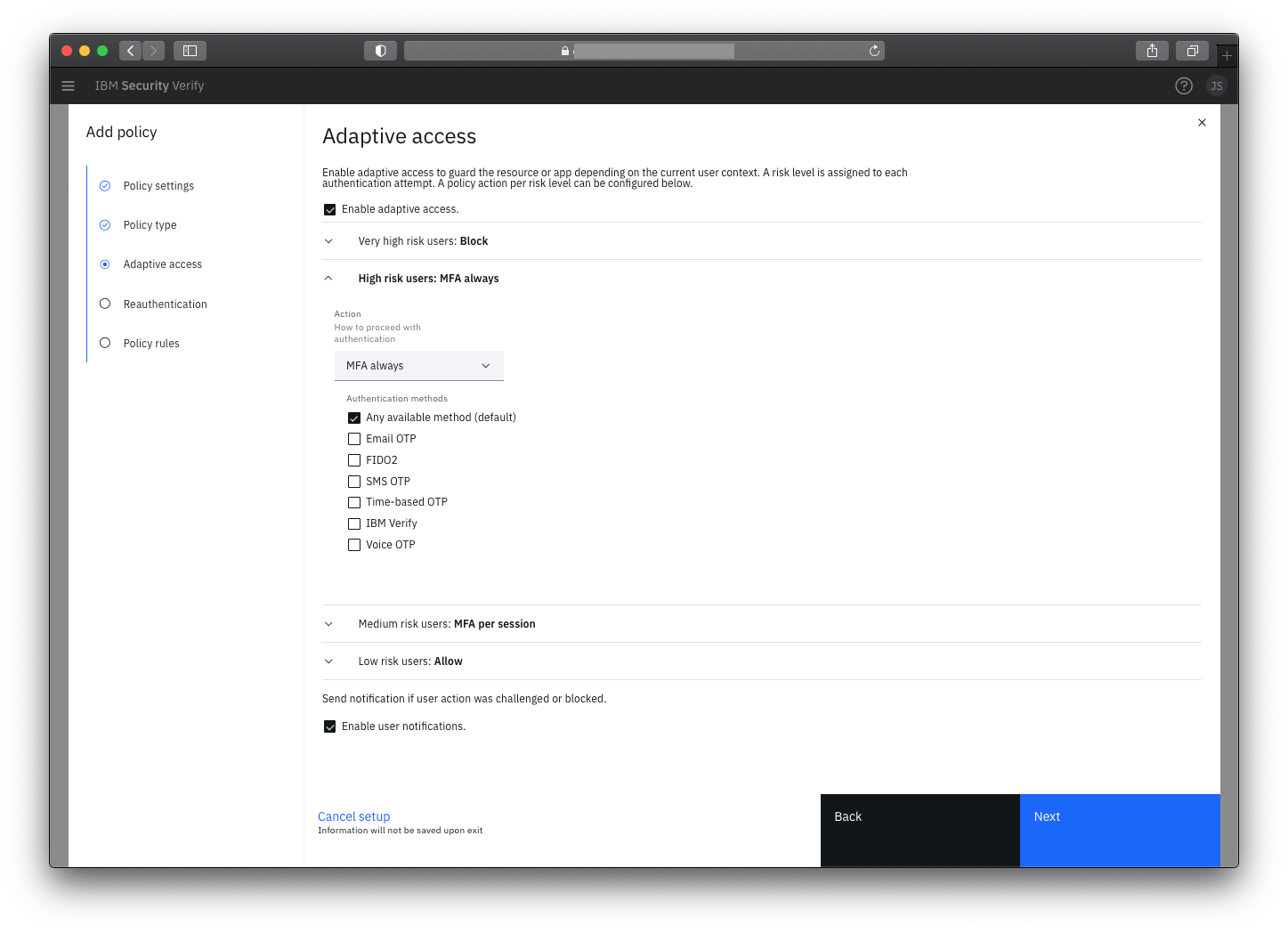
Risk-based authentication and adaptive access control
Allow streamlined access to low-risk users and either block or challenge access in higher-risk conditions with contextual, risk-based authentication and adaptive access. Organizations can use a simple policy editor to apply AI-informed access policies to prompt for MFA based on deep fraud detection signals across user, device, activity, environment and behavior context and the resulting holistic risk score.
Comprehensive context is key
To make accurate authentication decisions, AI and machine learning aided analysis of interactions simultaneously taking place is essential. Contextual parameters span:
User – profile attributes like phone number and email address and their reputation
Device – consortium data for device risk, organizational policy compliance, malware detection, virtual environment and remote access trojan detection, device fingerprinting, mobile hygiene
Activity – compare activity to detect anomalies from general population or job role, assess severity level of transactions
Environment – geolocation, time of day, and network connection evaluation, checking for exposed network, compromised DNS, malware in environment
Behavior – compare behavior against history to detect anomalies, behavioral biometrics like mouse movement, keystroke velocity, mobile phone positioning
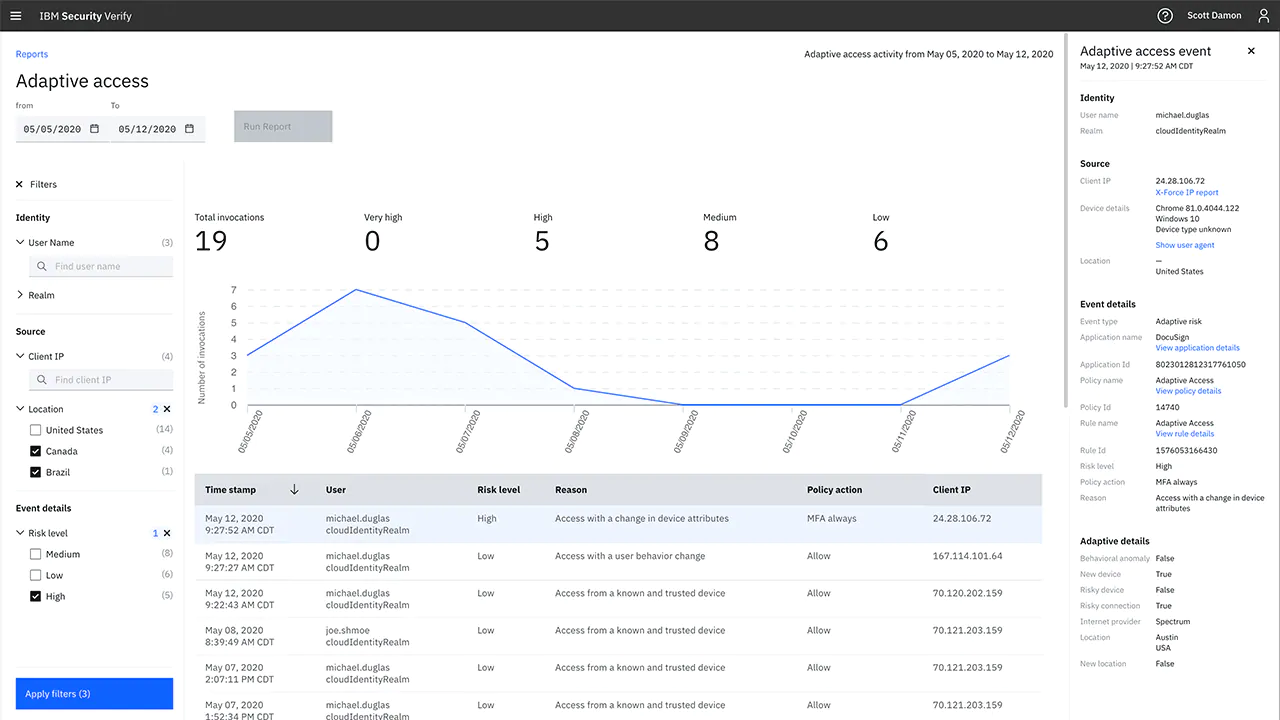
Monitor risk levels of events
Filter authentication activity to diagnose problems and view details of high-risk events that are sent to case management.
Updated 7 months ago
