Adaptive Access Policy for Native applications
The Knowledge Centre has some content available for authoring Native Application policies.
A Native application policy is made up of two sets of rules:
- Pre authentication rules
- Post authentication rules rules
A native policy must have rules defined for both.
Pre authentication rules
Pre authentication rules can use simple conditions to dictate which authentication methods a user must perform as their initial authentication step. Adaptive access is not available during pre-authentication.
Depending on the experience you need for your application you may have just one rule.
For Example, if your application will be performing username/password authentication to satisfy first factor authentication, your first-factor policy will be comprised of just one rule. This rule will be a challenge with the authentication type password
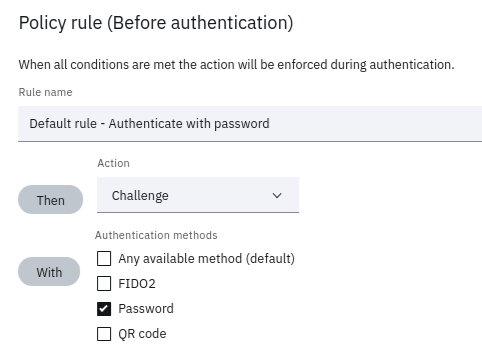
First factor policy rule
The conditions which are available, can be used to implement broad, non-user specific policy. Some which could be considered are:
- Require fido2 authentication if the user isn't on the corporate network
- Deny if access is coming from an out of country IP address
Post authentication rules
Post authentication rules are used to prompt a user for a 2nd factor based on conditions. Learn more about the conditions available on the Knowledge Centre
Adaptive access is applied as part of the post authentication rules. To make use of Adaptive access for your native application:
- Enable Adaptive Access on your policy
- Assign Actions to take for the given risk levels
- Very High
- High
- Medium
- Low
- Optionally configure email notifications for MFA/Denied access
- Optionally configure any Adaptive attribute conditions
- Optional configure any standard conditions
For more information on Adaptive access rules and conditions visit this topic on Knowledge Centre.
Applications which use single sign-on out of IBM Verify also support access policy and Adaptive access. For more information see Adaptive Access Policy for Single Sign On.
See also: Adaptive Access
See also: Managing Access Policy
Updated 7 months ago
