Connect a sample application
Introduction
We know that getting a test application is challenging, and coordinating with application owners is not any easier. IBM provides an out of the box application to connect your Verify instance to for testing out Single Sign on. While this application was built to be used with IBM Verify, it can also be used for IBM Verify Access and any other 3rd party IdP.
With this application, you can test out SSO functionality, various access policies, password-less authentication, and more.
Pre-requisites
The only requirement is that you have a SAML identity provider. If you don't have an IBM Verify trial or instance, register for a free trial below.
Before you begin
If you want an in-app guided experience setting this up, you can click "Guide me" at the top right of the header in your admin console. Click "Show me how to..." and then click "Connect a sample application".
Create a new application
In your admin console, navigate to Applications and add a new custom application. Provide a company name and then move on to the Sign on tab. Ensure that the connector type is set to SAML2.0.
Why are we using a custom application?
To allow for complete SAML testing and validation, we encourage you to use the custom connector with this application for the most variety of settings to use.
Gathering information for the service provider (application)
On the right hand side of the connector are the instructions for setting up a generic SAML2.0 application. We need to obtain a few bits of information from this side panel:
| Item | Example Value/Format |
|---|---|
| Login URL | https://tenant.verify.ibm.com/saml/sps/saml20ip/saml20/login |
| Logout URL | https://tenant.verify.ibm.com/idaas/mtfim/sps/idaas/logout |
| Certificate (in plain text) | -----BEGIN CERTIFICATE-----...-----END CERTIFICATION----- |
Configure the sample app
In the sample app home page, click Setup. Copy and paste in the login, logout, and certificate that you got in the previous step into their corresponding fields. Once done, click Next to move to the next step.
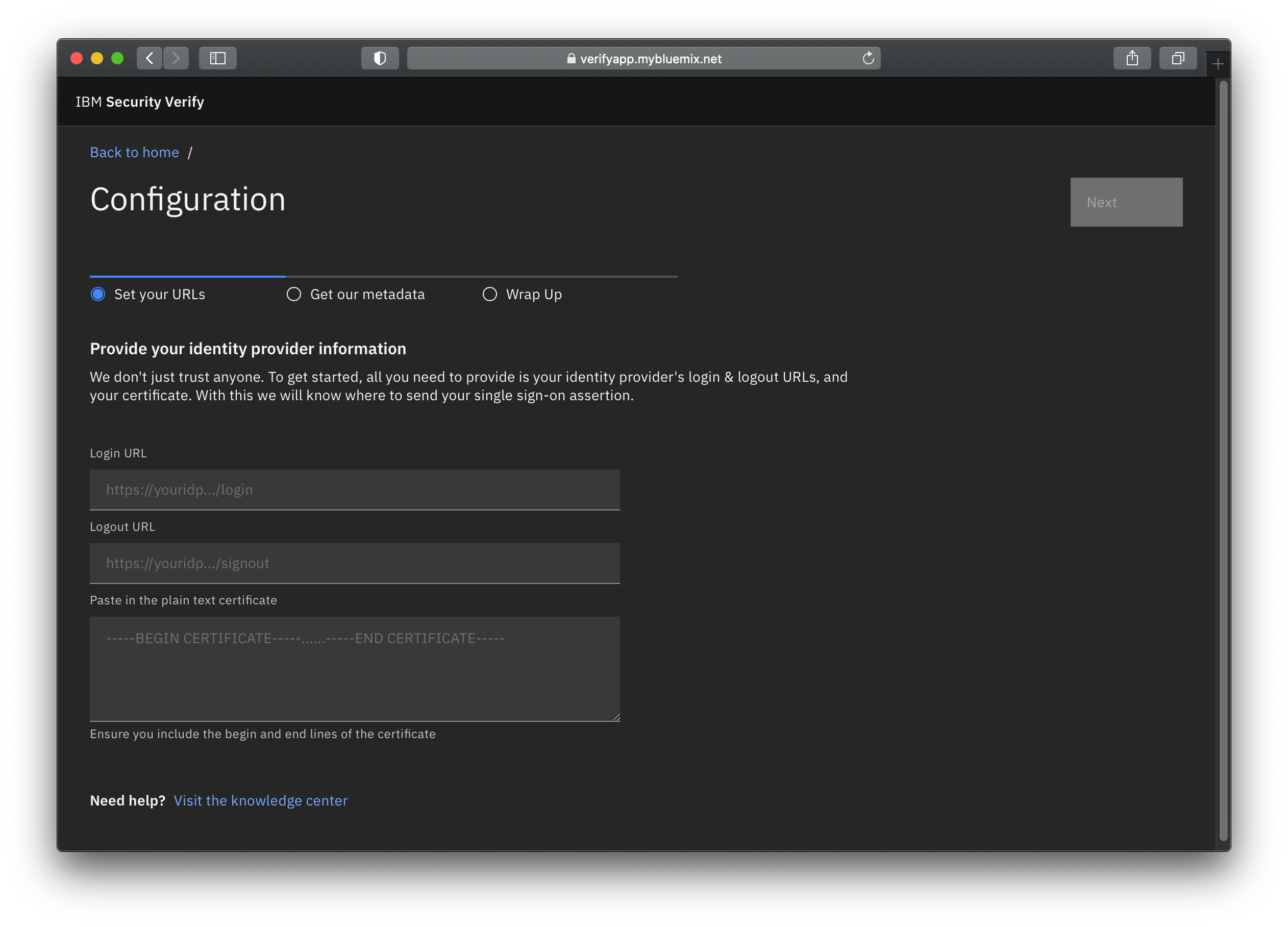
Sample SAML application for testing SSO with IBM Verify
Configure IBM Verify
In the sample app, three things are provided: Provider ID, ACS URL, and SSO login URL.
In the Verify custom connector, put in the following information into the corresponding fields
| Item | Example Value/Format |
|---|---|
| Provider ID | verify-app |
| ACS URL | https://samlapp.12murzlqn27z.us-east.codeengine.appdomain.cloud/assert |
| Single Sign on URL Note: This is the SP-initiated URL | https://samlapp.12murzlqn27z.us-east.codeengine.appdomain.cloud/login?uuid=xxxx |
Optional configuration
In this step you can play around with various settings like trying different attribute mappings.
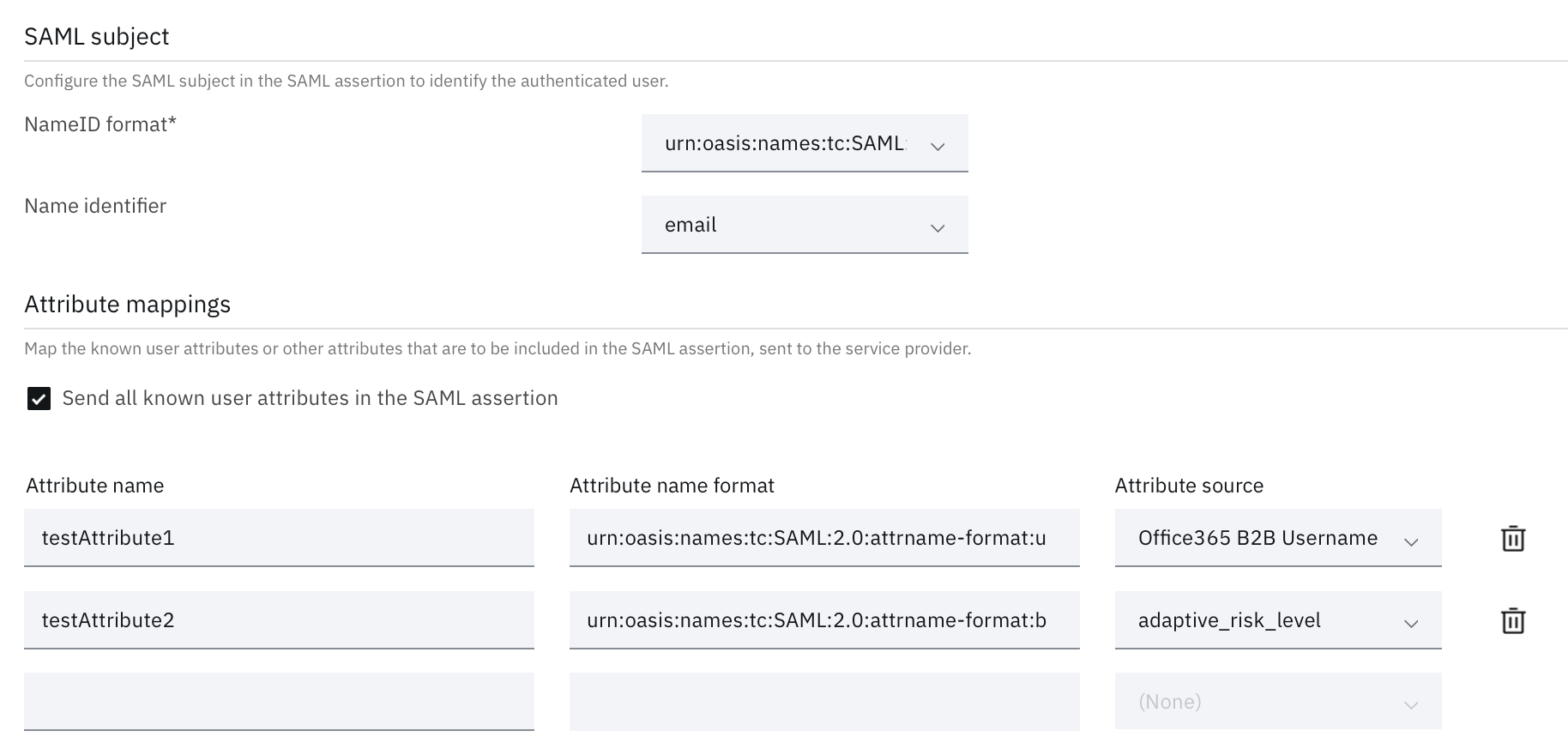
Apply a different access policy to try out multi-factor authentication.
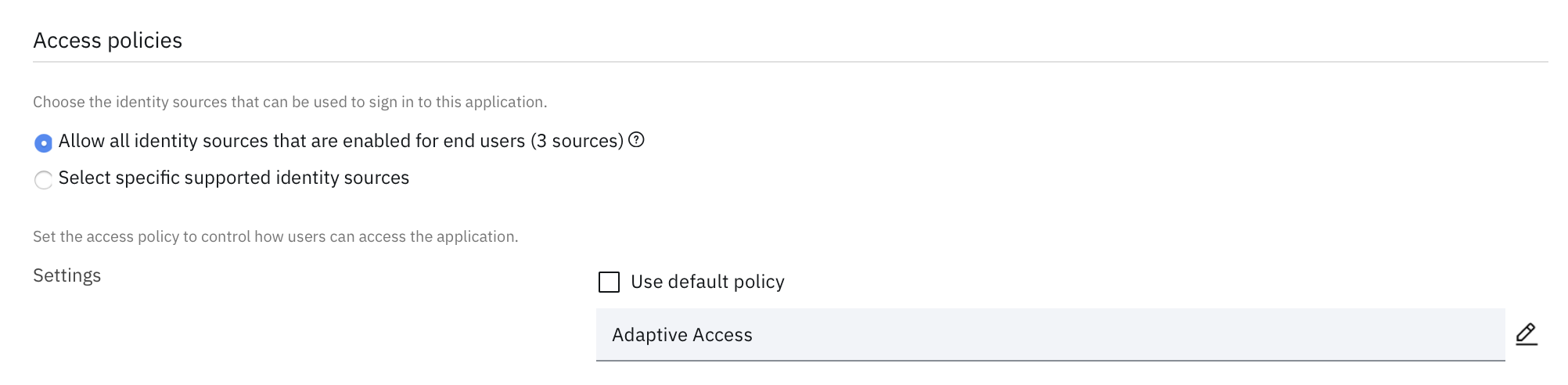
Provide birthright access for users and groups, or make this application request-able from user's self service launchpad with manager or app owner approvals.
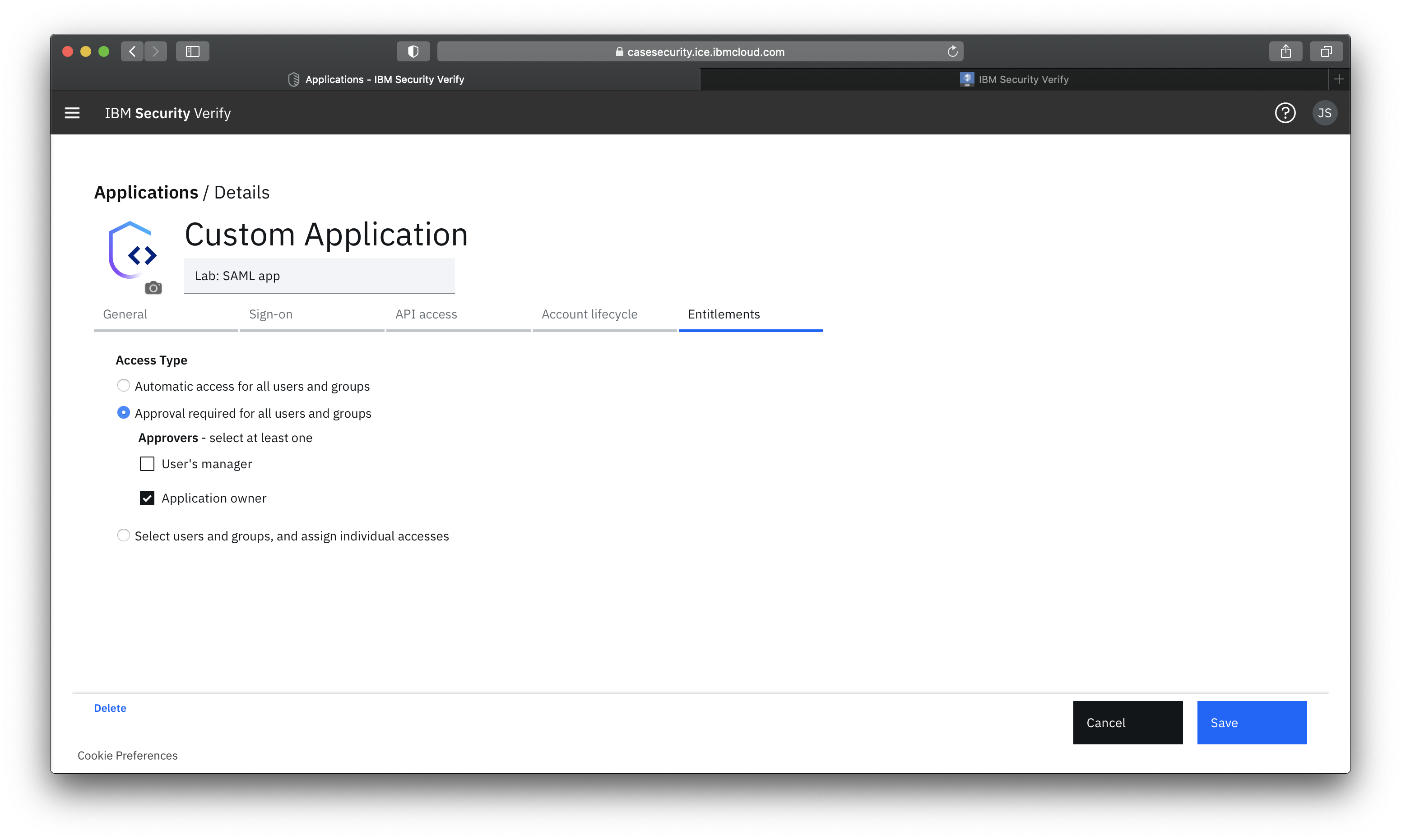
When you're done, click Save. The IBM Verify setup is complete.
Save the sample application
In order to complete and save the configuration in order for you to test SSO with this application, you must click Save on the sample app as well if you haven't done so.
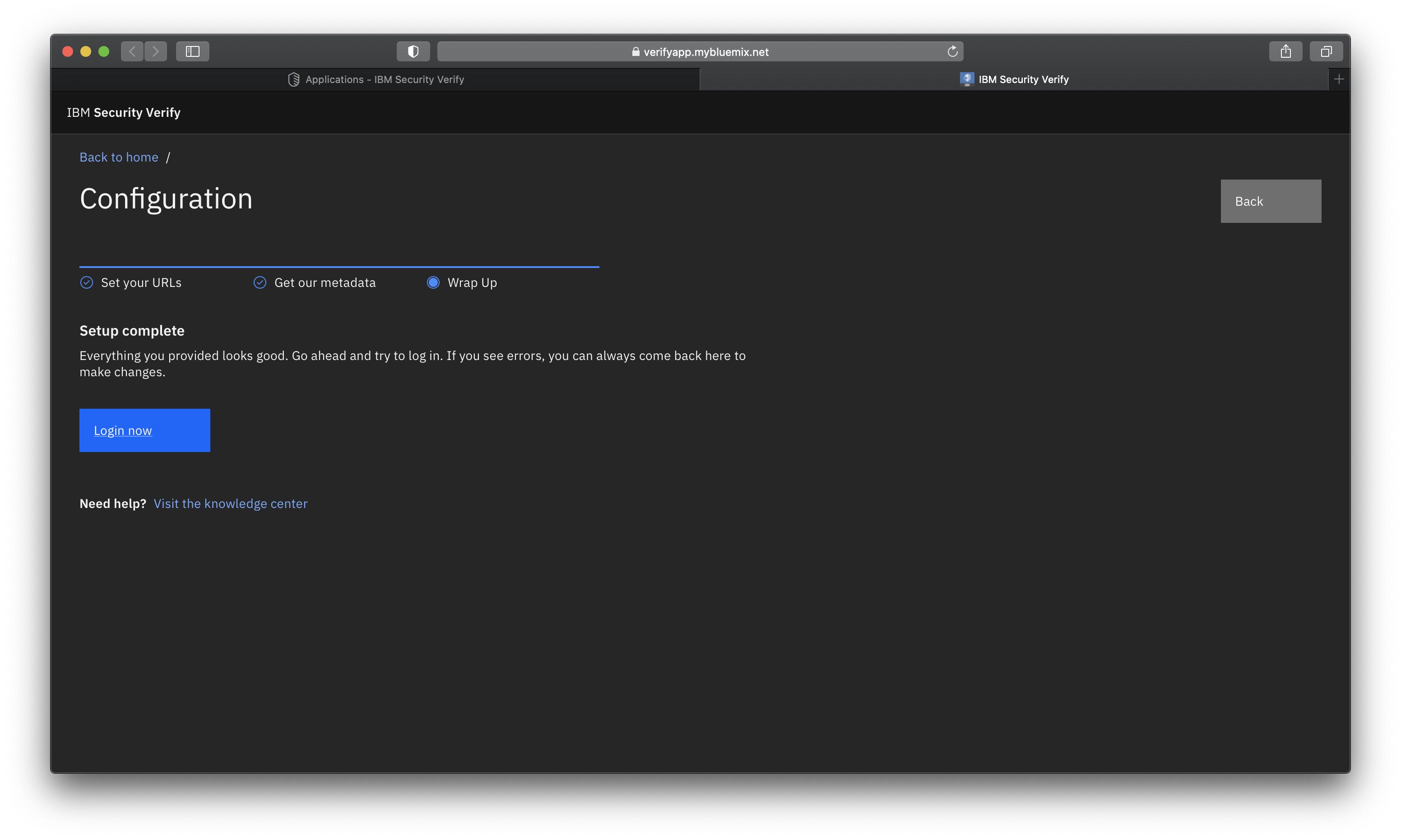
Login to your sample application hosted by IBM Verify
Test your sample application
Launch the sample application to log in by accessing from your Verify launchpad or from the link below.
You should be greated with a successful login and a welcome message on the application. Inside this application you can see the parsed list of attributes, including groups (which is provided if you chose to send all attributes). For more troubleshooting or analysis, the full SAML assertion is parsed and provided without the need for browser extensions.
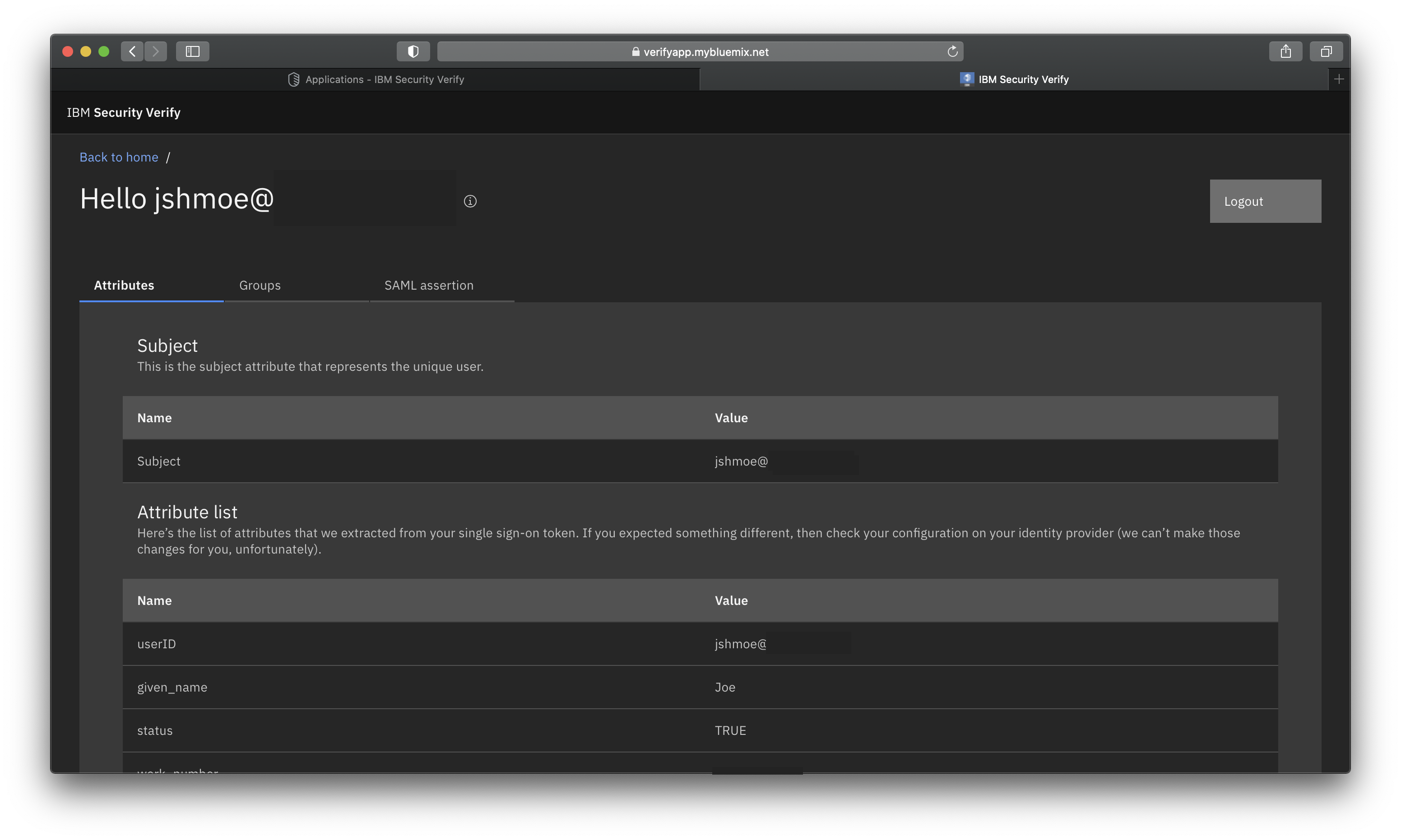
Sample application attribute viewer shown after a successful login
Bookmark the SSO URL
The configuration that you just completed is tied to your browser. If you ever clear the cache or access the sample app from a different browser, you will see the setup process again. However, the URL that was provided for SSO is uniquely tied to your configuration as well and can be bookmarked and accessed even in the event of a browser cache cleanup or if you want to provide to another colleague for testing. Also, this is quite useful when accessing from a private or incognito window.
Wrap up
Verify provides this application for your use and testing. Provide this application to developers or other admins to train users on how to setup SAML within Verify. It is encouraged to try various setup configurations on this application before moving to production applications.
Updated 7 months ago
