Orchestration
Orchestrating identity and access management (IAM)
Identity and access management (IAM) is complex and requires extensive domain knowledge and technical expertise. IAM is the cornerstone to interact with individuals, as employees, consumers, and machines. Hence, cross functional stakeholders such as Line of Business, Marketing, Privacy, IT, and more need to be able to produce business outcomes that also touch IAM setup and configuration. Organizations are looking for a simpler experience to consume and configure IAM across all personas as a foundational and enabling experience. Specifically, this includes:
- Defining the best user experience and journey.
- Assessing risk and fraud with proper mitigation.
- Connecting many IAM solutions through a common Identity Fabric. For example, legacy registries connected with a modern IAM platform.
An orchestration tool enables low-code or no-code configuration, which allows administrators and other personas to easily interact with IAM and configure experiences by using a drag and drop editor. Orchestration capabilities minimize any code that needs to be written and removes the need to have technical domain knowledge to deliver business outcomes enabled by IAM.
IBM Verify SaaS delivers orchestration through product capabilities such as the Flow designer, Adaptive access policies, standards based IdP integrations, directory agents, IBM Application Gateway, and more - all of which provide a low-code or no-code experience. This enables organizations to orchestrate the following scenario types:
-
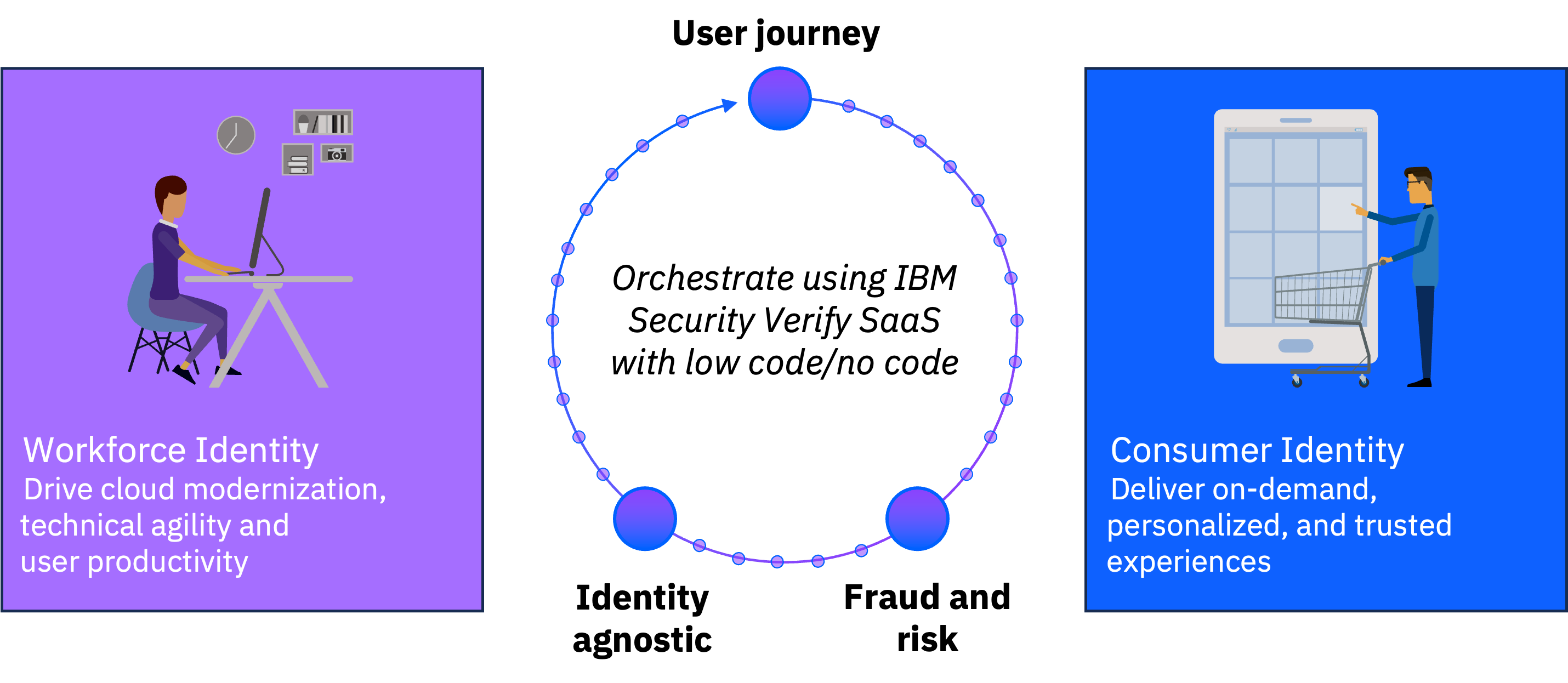
User journey: This orchestration experience is all about defining the pleasing and intuitive user journeys. This can span access account creation and registration, account creation approvals, application request approvals, data privacy and consent, login experience routing, account profile recovery, multi-factor authentication enrollment and use, and more. This orchestration experience is all about how individuals are routed to experiences based on the way organizations interact with individuals to deliver the best business outcome.
-
Fraud and risk: This orchestration experience is all about defining how the trusted individuals are allowed and the untrusted individuals are mitigated with security authentication. This can span from adaptive risk evaluation, third party risk assessment and mitigation, risk policy aggregation, and more.
-
Identity agnostic modernization: This orchestration experience is all about helping organizations manage, migrate, and enforce security on identities from one IAM solution to another IAM solution. This can be IBM Verify as the target IAM solution or any other modern IAM solution. Common scenarios include migrating users from a legacy directory to a new IAM system, protecting legacy applications with advanced fraud and risk protection, etc.
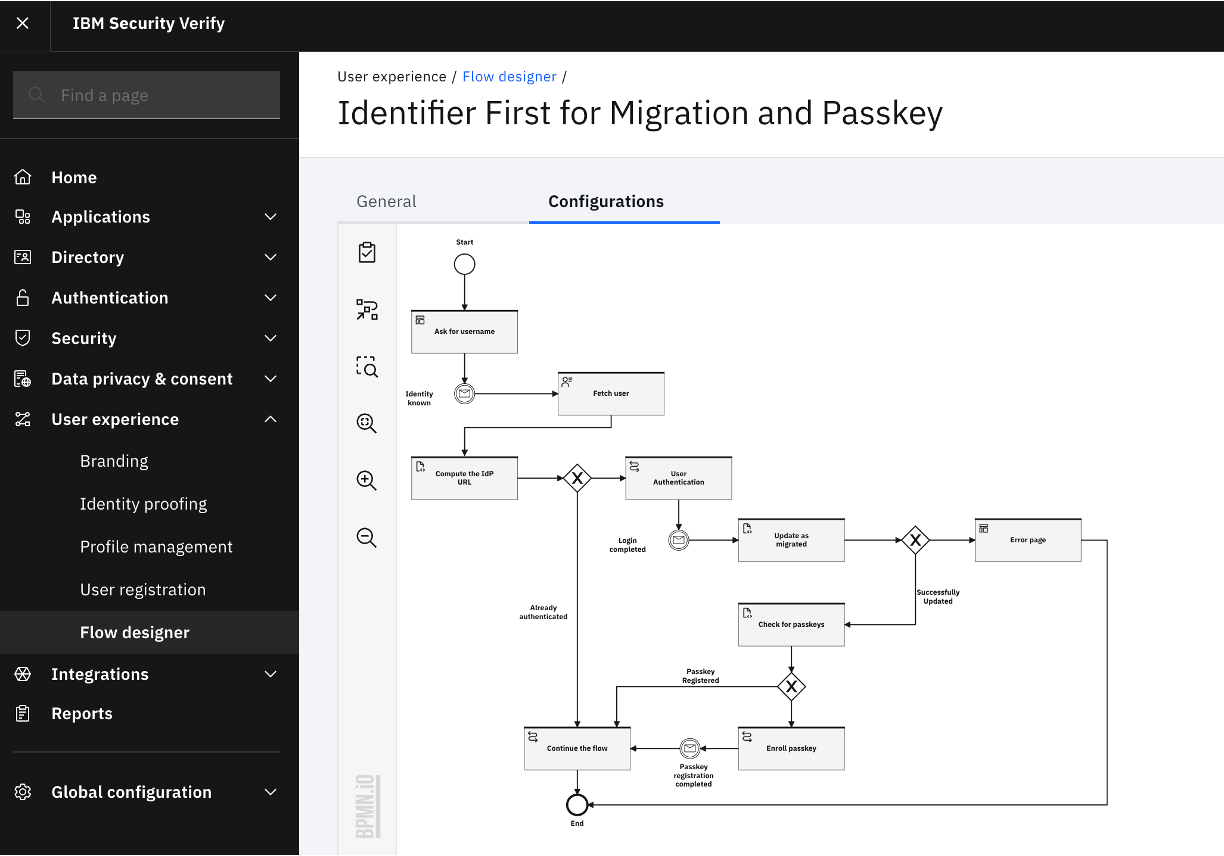
The flow designer within IBM Verify
To enable orchestration through low-code or no-code GUI experiences for administrators, IBM Verify delivers the "Flow designer". This is just one of the key capabilities that allows low-code or no-code experiences to orchestrate use cases within IBM Verify.
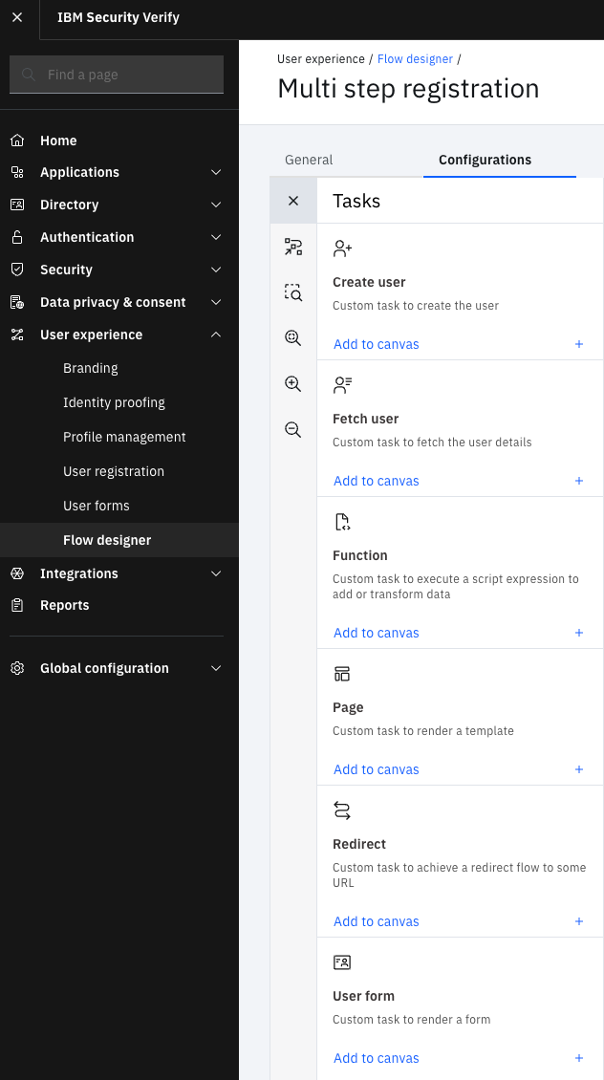
The Flow designer offers a few things that enable organizations to realize low-code or no-code experiences:
- Tasks: these are pre-defined components that are dragged onto the canvas of the flow designer and connected together to deliver the desired IAM experience. Examples of tasks are User forms, Identity proofing, Consents, Functions, Pages, Browser redirect, Create user, Approvals, and more.
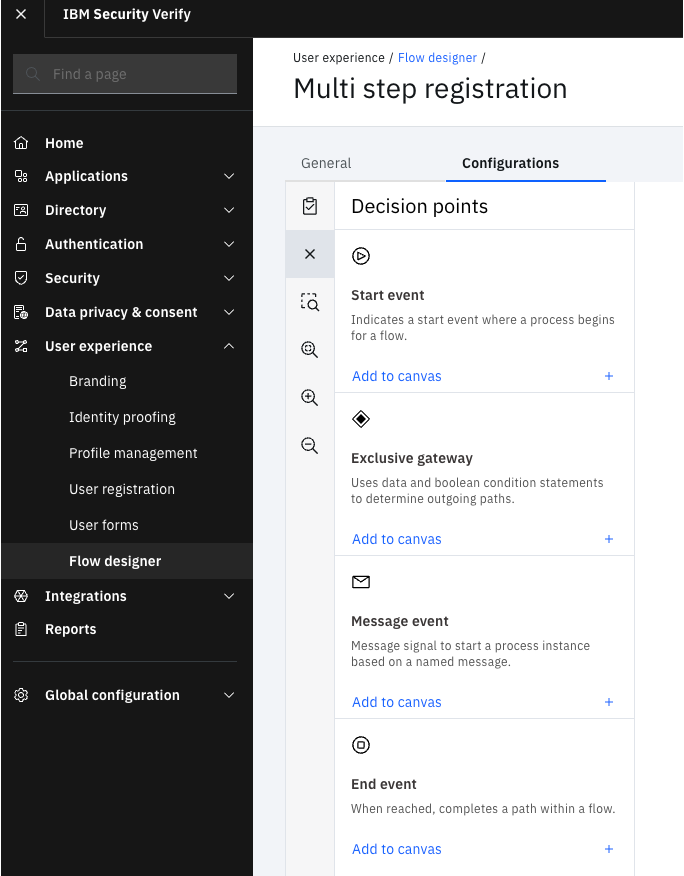
- Decision points: these are the conditions that determine how the experience navigates through the flow designer. Examples of decision points are Start, End, Conditional routing (Exclusive gateway), and more.
As flows are created and modified, administrators can import and export flows. This allows for the ability to create templates and easily modify a flow from an existing flow.
When used in conjunction with the other capabilities provided by IBM Verify (such as Adaptive access, Identity source integration, IBM Application Gateway, and more), the Flow designer helps administrators unlock powerful use cases defined by a common fabric for orchestrating IAM.
Getting started
To get started with flow designer within IBM Verify, go to these configuration guides to orchestrate an IAM experience.
Updated 7 months ago
