Orchestration guides
IBM Verify SaaS offers various user flows, such as user registration, password recovery, and more, that can be configured within minutes and published. However, IAM requirements can often be more complex, and this level of customization may prove insufficient. Use the Flow designer to address such needs.
Orchestration covers the concepts and capabilities that are offered by Verify. This article introduces several guides to learn about this capability and to also import common flows to your tenant.
Features
You may ask to enable certain capabilities on your tenant to unlock the full power of orchestration with Verify. These are listed here:
- Adaptive access: Offers risk evaluation using AI and machine learning models that combine device characteristics, user behavior and more to compute a risk level.
- Flow designer: Presents a canvas for a user to author customized flows beyond point-and-click orchestration options.
Guides
Several guides are available as sub-topics and you can view them at a glance here.
"Hello world"
"Hello world" flows are used to learn more about the capabilities and tools available. They should not be deployed into a production environment.
| Name | Summary |
|---|---|
| Login with username | Use an existing username to authenticate to the Verify tenant. |
User journey flows
| Name | Type | Summary |
|---|---|---|
| Identity source routing | Authentication | Use server-side rules to redirect a user to the appropriate identity provider. |
| Passkey auto-complete with identifier-first authentication | Authentication | Use registered passkeys to authenticate through the username auto-complete prompt. |
| Multi-step user registration | Registration | Build a multi-step user registration flow. |
| User registration with account claiming | Registration | Build a multi-step user registration flow with a claimed account. |
| User registration with identity proofing | Registration | Build a multi-step user registration flow with identity proofing. |
| Orchestrating user registration with risk evaluation | Registration | Build a multi-step user registration flow with risk evaluation. |
| User registration into a different identity provider | Registration | Build a multi-step user registration flow in IBM Verify to register a user in a different identity provider. |
Identity agnostic modernization
| Name | Type | Summary |
|---|---|---|
| MSFT IdP app protection | Authentication | Use IAG to protect legacy and on-prem apps with IdPs. Although IBM Verify can also be an IdP, if a 3rd party IdP is used, IAG can be leveraged to protect and modernize those applications. |
| Okta IdP app protection | Authentication | Use IAG to protect legacy and on-prem apps with IdPs. Although IBM Verify can also be an IdP, if a 3rd party IdP is used, IAG can be leveraged to protect and modernize those applications. |
| Ping IdP app protection | Authentication | Use IAG to protect legacy and on-prem apps with IdPs. Although IBM Verify can also be an IdP, if a 3rd party IdP is used, IAG can be leveraged to protect and modernize those applications. |
Usability and troubleshooting
| Name | Type | Summary |
|---|---|---|
| Trace flows in flow designer | Troubleshooting | Add trace hooks or debug statements to a Function task in a flow. Generate a trace URL for a published flow, to debug the Function task in the flow and view the generated traces in the Trace View. |
Adding flows to your tenant
The guides available as sub-topics contain instructions to add specific flows to your tenant. This provides a starting point for common flows. However, you may need to make some changes as described in each guide after you import the flow.
Associated assets
The associated assets, such as custom pages, flow model and any scripts, are available in the IBM Verify SaaS Resources repository. You will be expected to download the contents of this GitHub repository to your local machine. This folder you choose is referenced in the guides as $GIT_REPO.
There are two methods possible as described below.
Cloning the GitHub repository
You can use any Git client for this purpose and clone the repository to a local folder. For the purposes of this article, the commands are provided
here that can be run in a terminal. For Windows machines, this may need to be adjusted.
$ user@machine ~ $ echo "Choose any parent folder in your machine and change to it" && mkdir -p ~/workspaces && cd ~/workspaces
Choose any parent folder in your machine and change to it
$ user@machine workspaces $ git clone https://github.com/IBM-Security/verify-saas-resources.git && ls
verify-saas-resources
$GIT_REPO is the "verify-saas-resources" folder.
Note
You can use a GUI interface or any other method of cloning the GitHub repository to your machine. Also, if you have a valid SSH key, you may use SSH to clone the repository.
Downloading a zip
You may download the repository contents as a zip file and extract it in your machine. However, this is not recommended because it makes it harder to update the contents downloaded to your machine. With the Git client, partial updates can be pulled down more easily.
The steps to follow here are as below:
-
Open a browser and go to the IBM Verify SaaS Resources repository.
-
Download the source code as a zip and unzip to a source location. The
$GIT_REPOis the "verify-saas-resources-main" folder.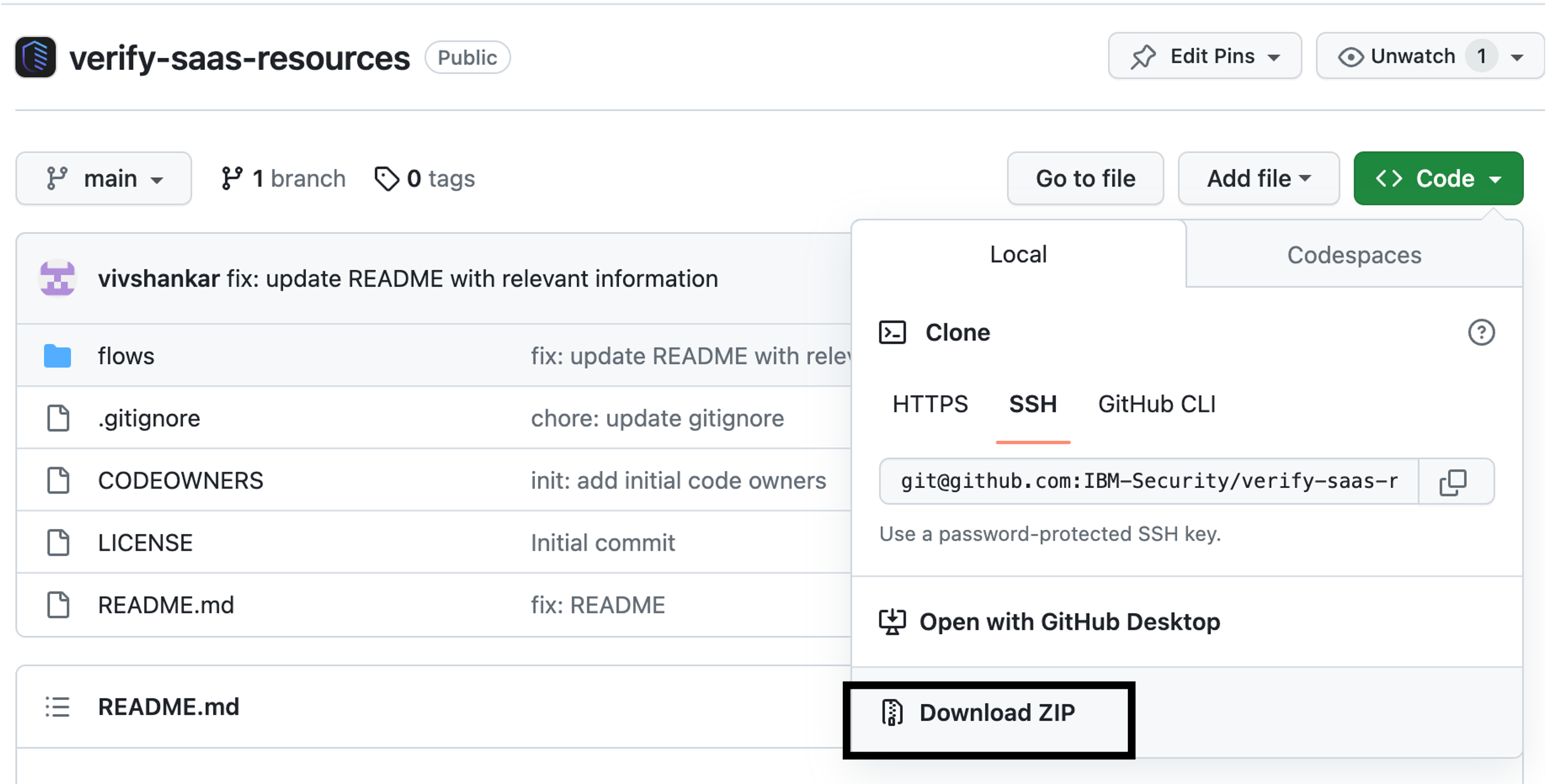
Updated 7 months ago
