Identity threat detection and response
Identifying and remediating threats
Identity and access management is the first line of defense for any organization. As the threat vectors, attack surfaces, and attack frequencies increase, a "shift left" approach to identifying threats is becoming essential. As attacks get more sophisticated, analysis and remediation of the attacks needs to be done with immediacy, in real-time. IAM solutions are capable to deliver security information and event management (SIEM) value natively, shifting identification and remediation of IAM-related threats "left".
Identity threat detection and remediation (ITDR) provided by IBM Verify allows organizations to proactively identify and remediate large-scale identity attacks. The native ITDR value provided by IBM Verify applies AI to determine anomalies found in all visible traffic. IBM Verify has mitigation for identifying and mitigating threats across various threat entry points.
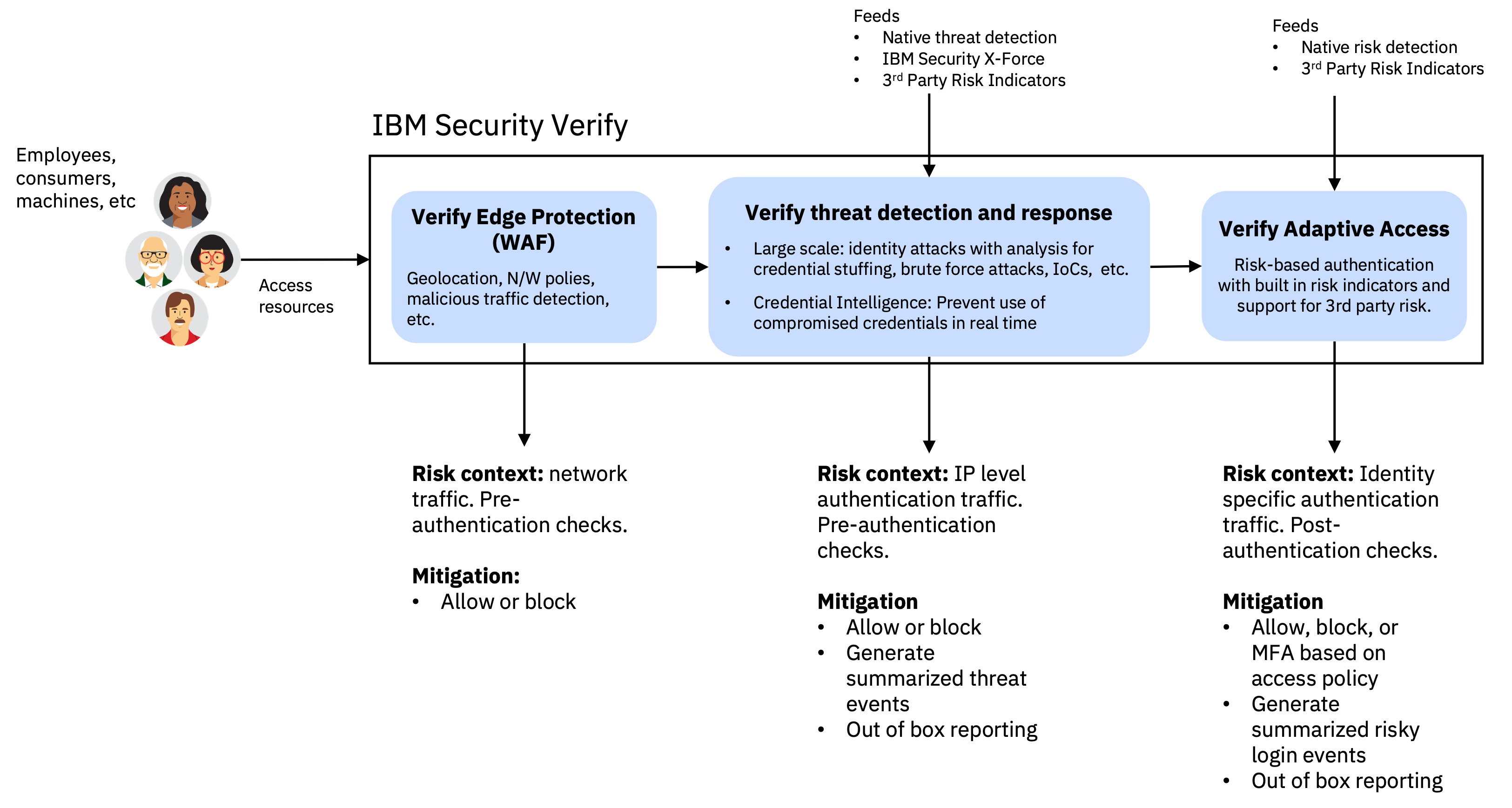
Verify edge protection (WAF)
Whenever a request comes to Verify, it is first analyzed at the Edge to block suspicious traffic. This helps prevent attacks like Command Injection, Cross Site Scripting (XSS), DDOS, Invalid HTTP, PHP Injection, Remote File Inclusion, SQL Injection, Trojan, and more. With an edge security solution, Verify also uses Geo-location and network policies to secure infrastructure. Identification and remediation actions include Web Application Firewall rules, IP rules, DOS Protection based on rate limits per IP, and client reputation based on prior behavior of individual and shared IP addresses. It is designed to stop malicious clients before they can attack.
In addition, the bot manager detects alerts and prevents bot traffic. Also, IBM Verify defines custom rules to deny suspicious traffic that might not fall under any of the standard protections that are provided by the WAF service.
The security detection and response team at IBM Verify monitors for threats and suspicious activity across its ecosystem of thousands of customers and partners, and it responds by taking appropriate action. Known malicious IPs are added to a blocklist at the edge layer along with various security controls covering encryption, tenant data security, network separation and security, and more. This helps prevent access from the IPs to any Verify tenant.
Verify Threat detection and remediation (ITDR)
The next layer of defense is the Threat detection and remediation module, which analyzes incoming traffic to detect potential identity-related attacks such as credential stuffing, brute force attacks, login anomalies, and more. It also uses threat intelligence from IBM Security X-Force.
The Threat detection and remediation module uses historical threat patterns that are generated across all IBM Verify tenants. Any tenant can take advantage of the alerts that the module generates, even if no previous attack existed. This capability allows for proactive mitigation of attacks. To align on privacy by design principles, tenant data is anonymized when other tenants decide to proactively remediate against threat attacks found on the target tenants.
Example: If Acme Corp is being attacked, Umbrella Corp and Big Blue Corp can be alerted of the attack and proactively remediate the attack without knowing Acme Corp was attacked.
The Threat detection and remediation module covers the following threat vectors.
-
X-Force Actionable IPs: This threat vector looks at the data feeds provided by IBM Security X-Force. The data feed is a collection of signals that are evaluated and aggregated to identify and classify suspicious IPs. Telco and other network data IBM Security X-Force participates within and contributes feeds into are used to detect the suspicious IPs. This capability is aimed at preventing known, suspicious IPs from accessing the system.
-
Failed logins: This threat vector looks at failed login patterns for both the first and second factor to determine whether the failed logins are within the normal threshold or deviating from normal thresholds. This capability is aimed at preventing large-scale attacks, specifically brute force logins from identified IPs.
-
Login deviations: This threat vector looks at successful login patterns for both first and second factor to determine if the successful logins are within the normal threshold experiences or deviating from it. This capability is aimed at preventing successful stolen credential logins from the IPs that are using this pattern of attack.
-
Credential stuffing/compromised credentials: This threat vector looks at the use of common or phished passwords during login to identify IPs that persist the behavior of using these passwords. This capability is aimed at preventing common or phished credential logins from the IPs that are using this pattern of attack.
After it is confirmed that the traffic is not suspicious, then it goes for Pre-Authentication checks. It includes checking whether the incoming credential is a common password or a previously compromised credential. If this check is passed, IBM Verify applies access policies to determine whether the request is allowed or blocked and if further verification is required.
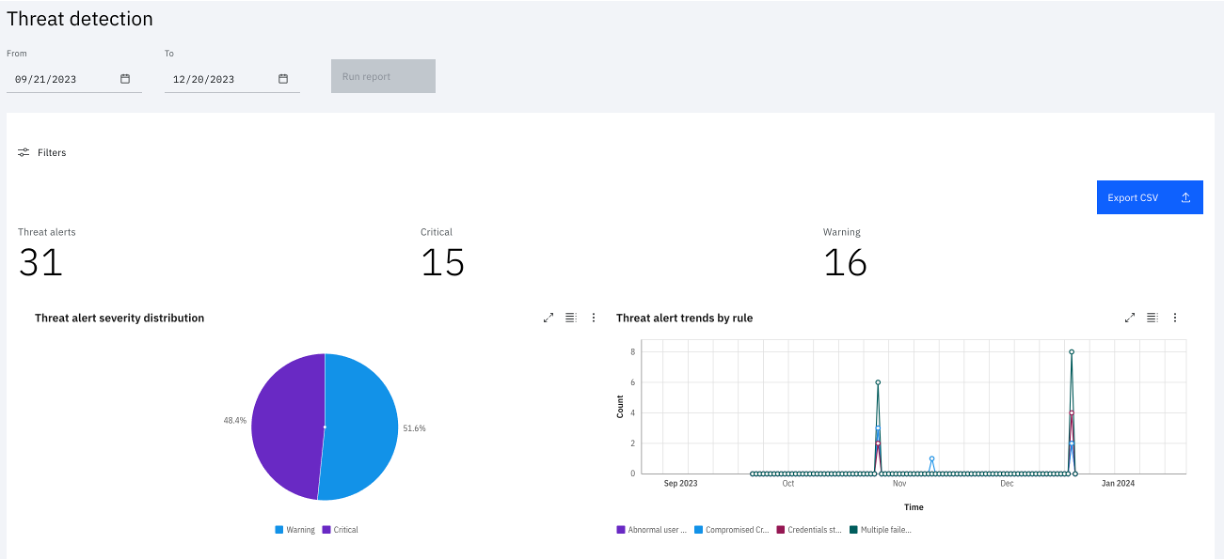
Threat detection events summarizes the threat events generated on detection.
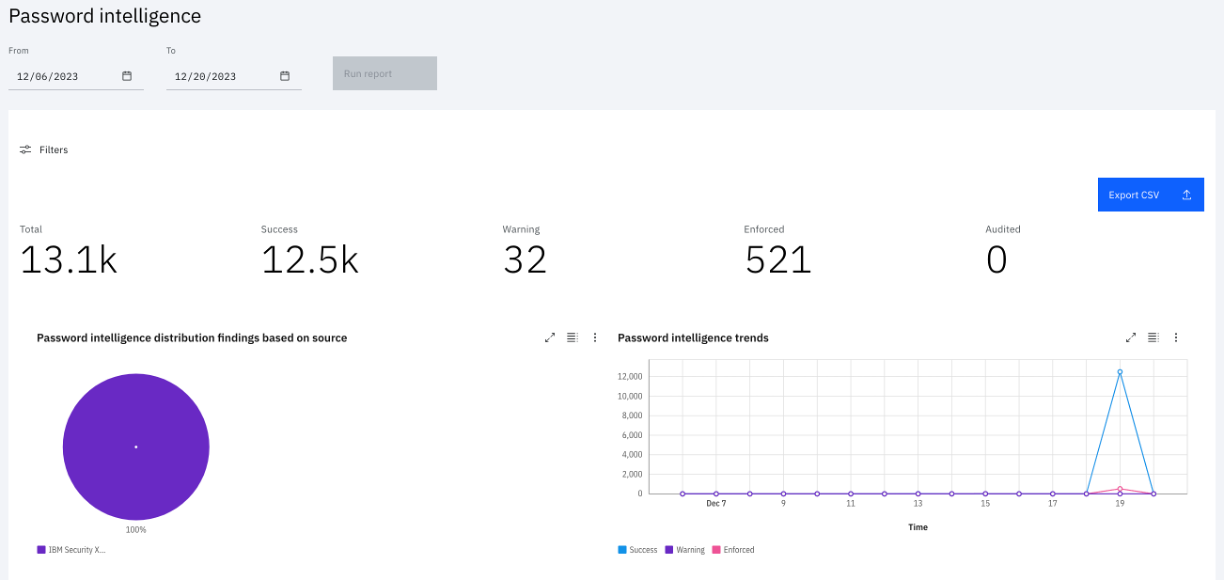
As part of the ITDR module, IBM Verify prevents the use of common or phished passwords with immediate remediation. IBM Verify has feeds from IBM Security X-Force and other password cracking communities to provide password intelligence. Password intelligence connects with the Credential stuffing/compromised credential threat vector.
Verify Adaptive Access
IBM Verify offers an adaptive and robust risk engine that can be configured to evaluate access control rules based on request context such as Geography and IP subnet ranges. It can also be configured based on user context and attributes, compliance state of a device drawn from a device management solution, dynamic user behavior biometrics, and more. Based on the outcome of a policy evaluation, the decision can range from allowing the transaction, blocking it, challenging for extra authentication factors or to direct the user to an external system.
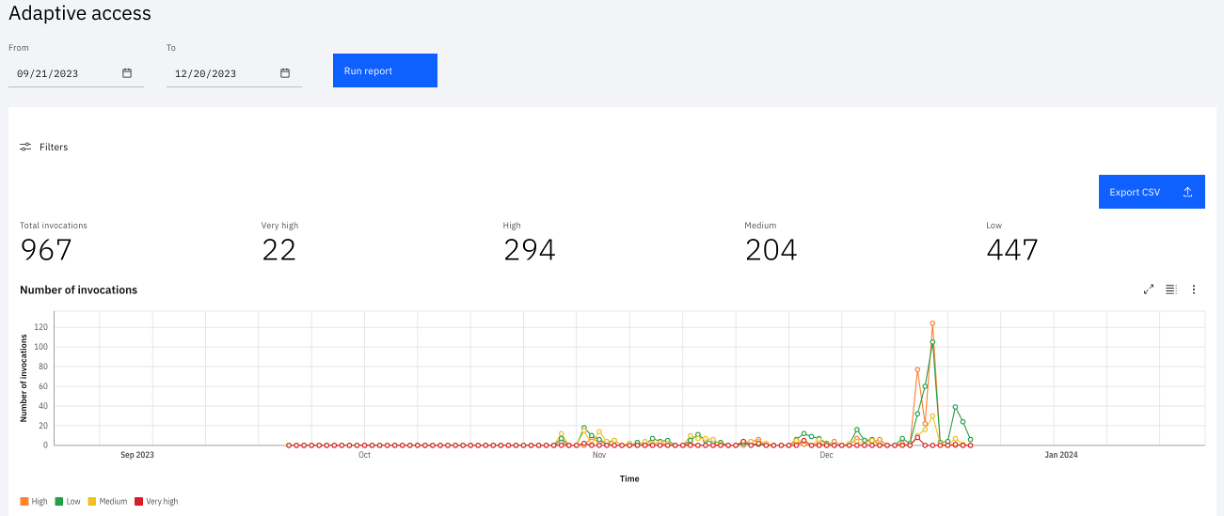
The risk-based authentication capability is Adaptive access. MFA options include SMS/Email OTP, TOTP, and IBM Verify Authenticator app (example: push, user presence, and biometric). Passwordless options also include QRCode, and passkeys (FIDO).
Threat related reporting and visibility
In addition to the detection and mitigation of threats, IBM Verify provides visualizations and further analysis of the threats and details that are associated with the threats.
Updated 7 months ago
