OpenShift Operator
Dynamically onboard applications running in an OpenShift environment to Verify SaaS for centralized authentication and authorization.
Introduction
The IBM Verify operator allows developers and admins of OpenShift to enforce authentication and authorization policies for all applications in an OpenShift cluster. The IBM Verify operator allows applications to be dynamically onboarded and centrally protected from IBM Verify SaaS.
The IBM Verify operator is available through the Red Hat OpenShift catalog and is certified as a Red Hat OpenShift image to ensure the proper currency and security when deployed within the OpenShift platform.
Prerequisites
To use the IBM Verify operator, the following pre-requisites must be met:
- OpenShift must be deployed. The IBM Verify operator does not support other Kubernetes environments.
- The Red Hat OpenShift certified NGINX Operator must be installed and the applications that will be protected by IBM Verify SaaS must be accessible by the NGINX ingress controller.
- An IBM Verify SaaS tenant is required.
IBM Verify operator installation
The details for the IBM Verify operator can be found in the IBM Verify operator GitHub. This will provide details on the operator architecture and flows supported, including the steps of configuring and installing the Verify Operator.
Configuring Verify SaaS with the Verify Operator
Once the Verify operator is installed, and corresponding pre-requisites are met, there are a few steps needed to complete the configuration.
1. Obtain client ID and secret in YAML format
The Verify Operator requires the client ID and secret for an API client that has the Manage OIDC client registration dynamically entitlement. In new tenants, an API client with this permission will already exist. For older tenants, you will need to create a new API client with this permission.
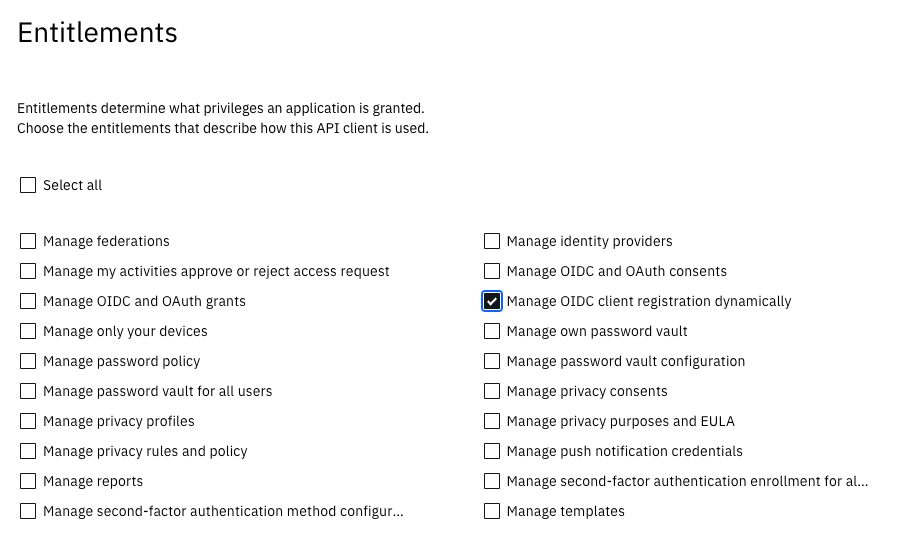
Grant "Manage OIDC client registration dynamically" entitlement.
To obtain the client ID and secret for your API client, log into your IBM Verify tenant as an admin and navigate to Security -> API Access. Click the dots on the tile for the client and select Connection details.
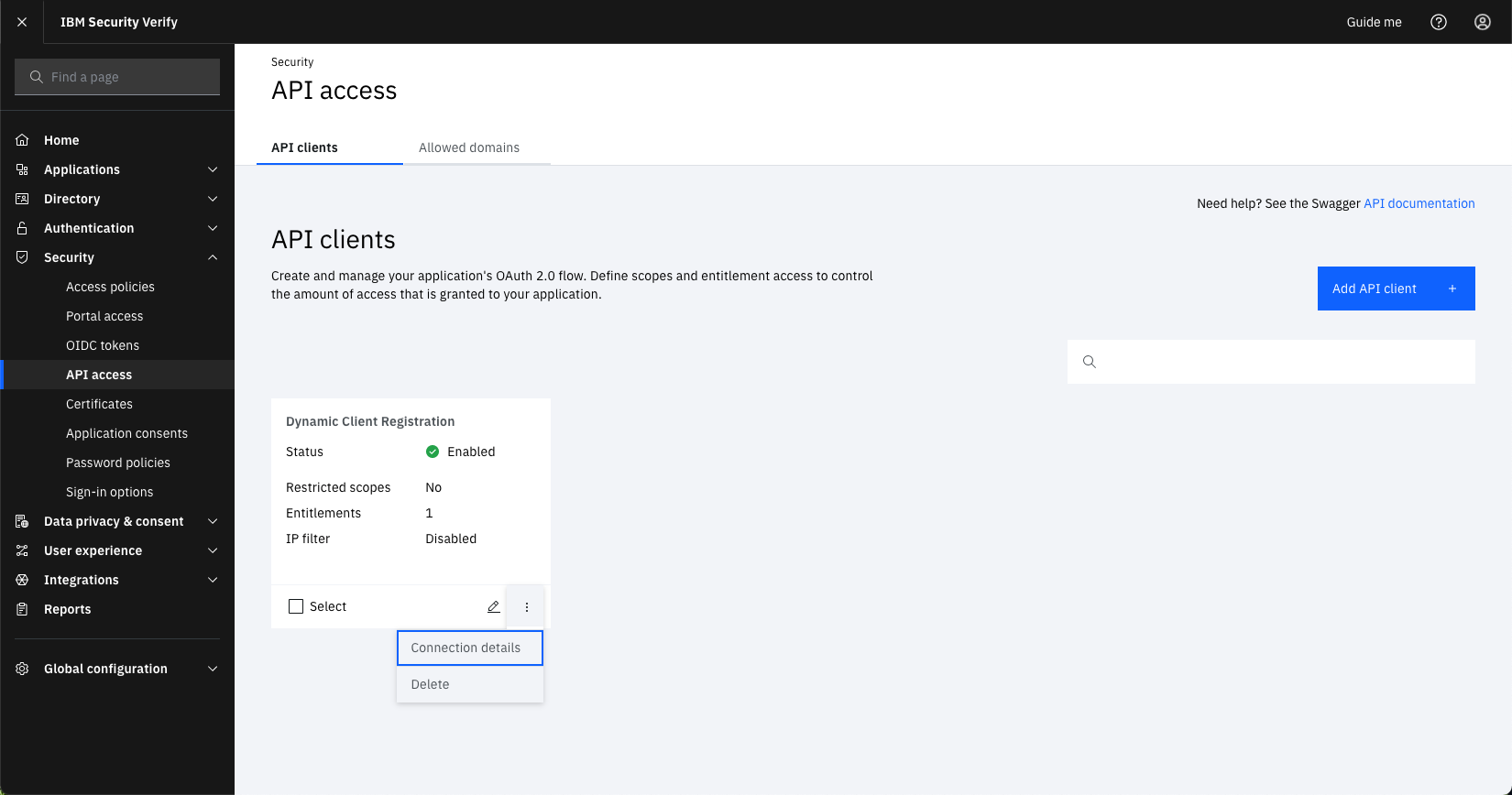
API client section in IBM Verify SaaS
Select the download icon for the Kubernetes secret to download a YAML file which can be used to create a Secret in OpenShift that contains the connection details. This Secret will be used by the Verify operator to connect to your Verify SaaS tenant.
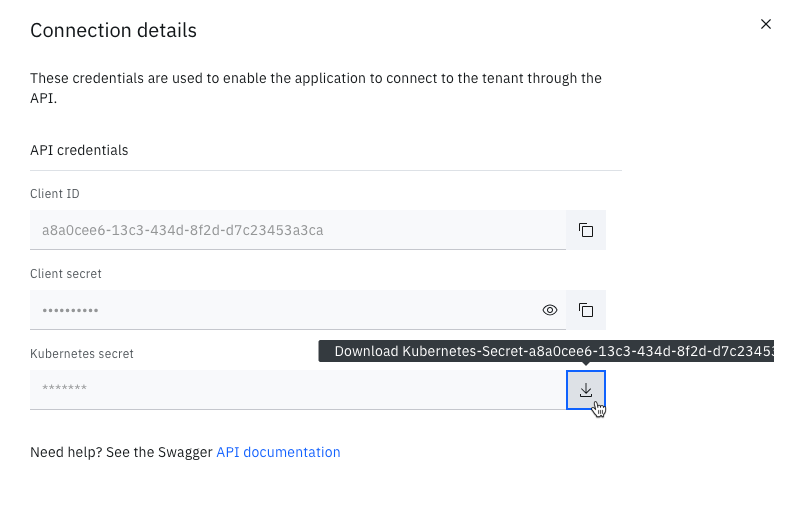
Download YAML needed for configuring Verify Operator with Verify SaaS
2. Create Secret and Custom Resource in OpenShift
Once the YAML defining the connection Secret has been downloaded, the following steps can be followed to configure the Verify operator, found in the Verify operator configuration section. Please ensure the formatting and data schema is followed when configuring the Verify operator with your Verify SaaS tenant.
Onboard applications
Applications can be onboarded automatically or manually. The Verify operator usage section outlines using the operator to protect applications.
Updated 7 months ago
